Governance Risk Management & Compliance is a MUST
If you are operating in a regulated industry (Financial Services and Healthcare, just to name two), the challenges in adopting cloud technologies can be overbearing, since most regulations prohibit an organization of comingling personal/sensitive data with other organizations.
For those companies that need to comply with SOX, GLBA, HIPAA and/or SEC (FINRA), a Governance Risk Management & Compliance (GRC) program has been the standard framework to track, monitor and measure an organization's exposure to risk. A strong GRC program will provide an overview of where the gaps may exist for an organization. This creates an initial dialogue between the line of business executive, the risk management team and the internal or external provider.
More than GRC
Unfortunately, GRCs only provide a risk management system for registering, reviewing and remediating a risk. Most GRCs do not help organizations break down the true risk or have the ability to expand from the traditional data center model to possibly reaching a public cloud model. GRCs fundamentally review an existing process and help organizations define their adequate controls. Once a review is completed by the assessment team, the process is then repeated by the business the following year for reassessment. If there is a change before the reassessment, a serious risk is presented to the organization because of its inability to identify and detect a change in a timely manner. Today, GRCs do not identify and detect change. GRCs only help in the manage assessments, document risk and document the remediation process.
GRCs are good but not great! Organizations have started to implement and understand the importance of a cybersecurity framework, which provides a more comprehensive understanding of their security posture.
Adopting a Cybersecurity Framework
To meet the demand of regulators, technology departments and security professionals have adopted a cybersecurity framework standard. A cybersecurity framework will provide a road map to reduce the cyber risks for an organization. The most frequently used cybersecurity frameworks by professionals today would include COBIT 5, ISO 27000, and NIST 800-53. Recently, a new framework has been developed by NIST's "Framework for Improving Critical Infrastructure Cybersecurity."
The Cybersecurity Framework was published in response to Executive Order 13636. It is focused on the improvement of the security of the nation's critical infrastructure from cyberattacks, and it is a helpful tool for any organization that is looking to improve their internal and external cybersecurity posture.
Below is an illustration of the Improving Critical Infrastructure Cybersecurity Framework Core by NIST:
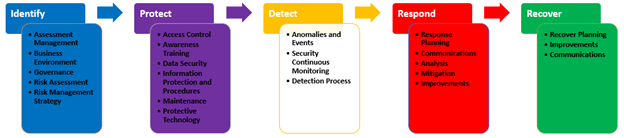
Most organizations today are utilizing one or more frameworks and should consider reviewing the Improving Critical Infrastructure Cybersecurity Framework by NIST. The framework is straightforward and can be used by any organization to map their existing ISO27001 (2), COBIT5 or other standard framework. Most importantly, Improving Critical Infrastructure Cybersecurity Framework is very simple to understand and implement for any organization.
Today, many organizations seem to have a strong understanding on how to manage a cybersecurity framework within their own data centers, but are challenged in managing their security posture into a cloud environment.
Cloud Adoption Risk & Recovery
Migrating to the cloud definitely comes with plenty of risk for any organization and the importance of measuring the risk versus the rewards is just as important as determining a plan B. The world of consumer cloud solutions, such as Netflix, Drop Box and Google Docs has elevated the awareness of cloud technologies to business executives, which has created havoc for technology departments. With their consumer experience of cloud technologies, these executives (without any depth of knowledge in cloud technologies) will just ask "can't we just put the solution in the cloud?"
If it were that simple, I would imagine every technology department would be pushing every application, virtual machine and database into the cloud. Technology executives and departments are constantly trying to measure three basic elements to maximize the Return on an Investment (ROI):
|
Cost: The Cost is based upon the capital or operational expense for a solution. SLA: The Service Level Agreement is the minimum business and technology requirements that an organization needs to be achieved in providing a service. Risk: The Risk level is based on the relationship of threats and vulnerabilities, available exploits and probable impact. |
Three Basic Elements: |
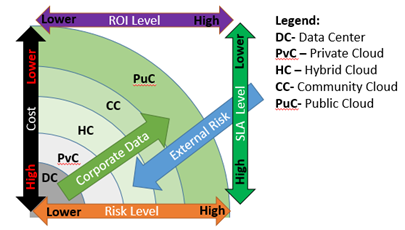
As an organization analyzes these elements with a focus on the location of data, it begins to develop boundaries or relationships between cloud layers and tolerance to risk and maximization of ROI.
Cloud Layers and Maximization of ROI
|
Traditionally, most organizations in a regulated industry have started within a standard data center. With the progression of virtualization technology, organizations have rapidly adopted virtualization, which has revitalized the enterprises' delivery of the application and service model. |
|
The illustration above sets a framework for any organization to understand its tolerance for risk with cloud adoption compared to the overall ROI. As corporate data is extended from a traditional data center, the exposure to external risk is increased with the lower costs to support and lower SLA offerings (or at least, a lower ability to control and manage service level agreements for the organization). The opportunity for significant ROIs are available today with a strategic cloud adoption plan that incorporates a high focus on risk level. Beyond the determination of risk and reward as to where to the data should rest, organizations need to establish a consensus between business executives and the technology organization. Consensus amongst all parties will establish an awareness, strong communication and feedback!