The National Institute of Standards and Technology (NIST) 800-145 defines cloud computing as "a model for enabling ubiquitous, convenient, on demand access to a shared pool of configurable computing resources (e.g., networks, servers, storage, applications, and services) that can be rapidly provisioned and released with minimal management effort or service provider interaction."
NIST further defines five essential characteristics of cloud computing, three service models, and four deployment models. These are summarized in the schematic below taken from the Cloud Security Alliance's publication: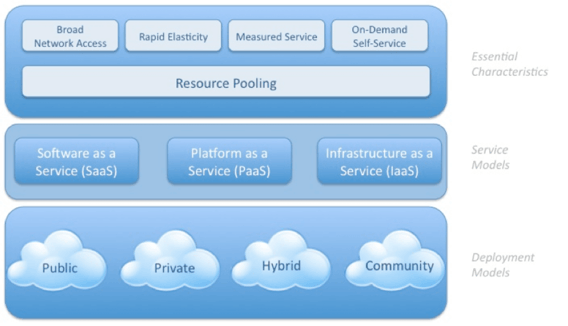
For clarification of each of the components, please refer to NIST 800-145.
Cloud computing can offer significant potential benefits in terms of reduced costs and improved business outcomes. For those organizations that are already familiar with an outsourced IT business model, cloud computing is an attractive option to handle on-demand capacity adjustments.
Some of the typical business drivers are:
Reduced Capital Expenses: There may be minimal initial investments required for establishing the infrastructure for computational resources
Reduced Operational Expenses: The overheads associated with maintaining a data center and its information assets can often become overwhelming. A cloud based infrastructure may mitigate these costs as a direct result of sharing between multiple customers
Improved Access to Resources: Broad network access to services and data in a cloud infrastructure can provide anytime, anywhere access as well as possible reduced latencies
Disaster Recovery and Business Continuity: Cloud infrastructures are typically located in multiple geographic locations and include replication as part of their operational models. This ensures network accessibility and continuity in the event of a disaster
Seasonal Demand Adjustments: Businesses often see spikes in demands for their goods and services based on annual or seasonal events. In such cases, it is cost effective and expedient to "spill-over" the demand into the cloud on an on-demand basis
The benefits of cloud computing notwithstanding, there are a variety of risks that must be considered when evaluating a cloud strategy for a company. The risks are directly proportional to the sensitivity of the information that is likely to be placed in the cloud. Furthermore, a cloud provider's implementation of its infrastructure and offerings may also result in risk considerations. Some of the major risks are listed below:
-
Since cloud service providers offer significantly reduced operational costs, they are often unwilling to provide even the very basic security controls as part of their services. This puts the burden on the consumer to accept the risk of minimal or missing data protection controls
-
Deficiencies in implementation of virtualization or other services by the provider may lead to information leakage, compromise or system instability
-
The geographically diverse nature of a cloud may result in a violation of local government laws prohibiting the transfer of information between foreign countries
-
Inadequate system/application level logging or monitoring may allow a problem to go unnoticed for significant periods of time
-
Targeted attacks or denial of service attempts may be a bigger concern for cloud environments due to a wider operational footprint
Cloud Security Considerations
For the most part, security considerations in the cloud should be no different than those required for any typical information technology environment such as a conventional data center containing information assets and resources.
However, a cloud poses additional risks and opens up attack vectors that arise as a result of its operational model, technologies used to provide services and the geographically dispersed and shared distribution of its computing assets. Therefore, an additional layer of diligence may be required to ensure adequate protection of information assets.
Numerous laws and regulations specifically require companies to adopt a reasonable set of security and privacy measures when storing or processing personal information. These laws and regulations include HIPAA, GLBA, PCI, HIPAA, Massachusetts Breach Law - 201 CMR 17.00, FTC Orders, OECD and EU directives etc.
Specifically, the PCI Data Security Standard and ISO 27001/27002 provide a detailed set of controls that must be implemented in order to demonstrate due diligence with the stated laws and regulations.
An organization's cloud security posture needs to take into account security controls at the following elemental layers:
(i) Physical Security: The controls around the physical environments constituting the cloud providers data centers and operating premises. This may include access controls, video monitoring, fire suppression, UPS and backup procedures etc.
(ii) Network Security: The security controls within the cloud providers network as well as those in the channels of communication to and from the cloud. This may include firewalls, IDS/IPS, network behavior monitoring and vulnerability scanning etc.
(iii) System Security: The controls around the operating systems, databases, applications etc. These may include system hardening, virtualization security, AV, encryption, application security testing, logging and monitoring etc.
Cloud strategy must be based on the sensitivity of data being stored or processed in the cloud and the mode of connectivity between the company's networks and information assets and the cloud provider's environment. Data that is deemed "sensitive" will have a higher degree of security requirements than data that is considered to be "non-sensitive" or "disposable".
The following sections define the categories of sensitive data and also list the specific security requirements for the storing and/or processing of sensitive as well as non-sensitive data.
Sensitive Data
Sensitive data can be broadly classified into two categories: PCI/PII/PHI data and Customer Confidential / Proprietary Data.
Payment Card Industry (PCI) data refers to credit card numbers, associated names and addresses on record, date of expiration and the card verification code. The PCI Council specifies strict controls on the movement and storage of cardholder data. Please refer to the PCI Data Security Standard (PCI-DSS) available at www.pcisecuritystandards.org, for the specific details of these controls.
Personally Identifiable Information (PII) can include a very wide variety of data elements but typically refers to the following:
-
Fistname, Lastname
-
Mailing Address
-
Email Address
-
SSN/National ID Number
-
Bank Information
-
Driver's License Number
State and Federal authorities specify varying degrees of penalties and breach notification requirements for the loss or exposure of PII.
Protected Health Information (PHI) refers to information that can identify an individual and their past, present or future health or mental condition as well as the treatment or payment processing of the treatment/medication for that condition.
Customer Confidential / Proprietary Data includes the following:
-
Company's intellectual property such as patents, designs, trade secrets, internal documents
-
Pricing and discounts
-
Financial data
-
Marketing data
If any of the data components specified above are to be stored, processed or transmitted to a cloud, the security controls listed below must be considered and implemented.
(i) Appropriate Contractual Language: A formal contract must exist with the Cloud Service Provider (CSP). The boiler plate contract provided by the CSP (often as an online Terms of Use statement) may not always be acceptable. The contract must have specific provisions around data ownership (your company must retain ownership of data), data disposal at the termination of the relationship and other obligations as defined by your company's legal or information security department.
(ii) CSP Certifications: The Cloud Service Provider must be able to provide certifications for their data center hosting the services. Acceptable certifications are SOC - 1 or II (Type 2), ISO 27001/27002 and/or PCI-DSS.
(iii) Firewalls: The connectivity between your company and the CSP must utilize stateful packet inspection firewalls or Application Layer (Layer-7) firewalls (when appropriate), to protect your corporate networks. Only the minimum number of protocols/ports that are required for business must be configured through the firewalls.
(iv) IDS/IPS: An intrusion detection and prevention system must be installed to routinely monitor any unauthorized or malicious activity within the cloud environment and to prevent any unauthorized access to your company's networks from within the CSP's network
(v) Access Control: A mechanism must be implemented to authenticate and authorize users that are likely to utilize the data. Formal de-provisioning processes must also exist to remove users that are no longer with the company or no longer have a need to access the information. Access controls must be in accordance with your company's policies and standards for account and password management etc.
(vi) Encrypted Transmission: The channel of communication between your company and the CSP must utilize SSL encryption to protect the data in transit.
(vii) Vulnerability Scanning: All VMs and systems deployed within the cloud must be in scope for vulnerability scanning, at least annually.
(viii) System Hardening: Virtual Machines, operating systems and databases that are deployed within a cloud provider's environment must be hardened using security standards published by SANS, NIST and the Center for Internet Security (CIS).
(ix) Anti-Virus: A centrally managed antivirus must be installed on all operating systems. Some CSPs actually include this requirement in their contractual language
(x) Two-Factor Authentication: If administrative access to the systems and/or data are required over the Internet, then some form of two factor authentication must be utilized.
(xi) Logging: Appropriate levels of logging must be configured at the OS, DB and application levels and the logs must be aggregated at a central location.
(xii) Security Patches and Updates: The operating systems, middleware (Apache, Tomcat, IIS, Websphere, Weblogic etc.) and databases must be patched with security updates and hotfixes in accordance with established company standards.
(xiii) Encryption at Rest: Data must be encrypted end-to-end. The requirement for encryption during transmission was specified earlier. Data at rest must be encrypted continuously in order to obviate state and federal breach notification requirements in the event of loss, exposure or compromise.
(xiv) PCI - DSS Considerations: The presence of cardholder data in a cloud environment imposes additional security controls and requirements in accordance with the PCI Data Security Standard.
The controls outlined above, for sensitive data, apply in their entirety, including encryption. However, encryption is just one of the 230 administrative and technical controls that the PCI-DSS mandates for systems that store, process or transmit cardholder data. Therefore, if cardholder data is to be stored in the cloud then the entirety of the DSS must be considered and implemented.
However, if the Primary Account Number (PAN) on the credit card can be tokenized before being placed in the cloud, then the systems are likely to be considered out of scope for PCI.
Non-Sensitive Data
For those instances where company data does not consist of PCI, PII, PHI or company's intellectual property and/or other proprietary data, some of the security controls may be obviated.
The following core requirements persist:
(i) Appropriate Contractual Language: A formal contract must exist with the Cloud Service Provider (CSP). The boiler plate contract provided by the CSP (often as an online Terms of Use statement) is not acceptable. The contract must have specific provisions around data ownership (your company must retain ownership of data), data disposal at the termination of the relationship and other obligations as defined by your company's legal or information security department
(ii) CSP Certifications: The Cloud Service Provider must be able to provide certifications for their data center hosting the services. Acceptable certifications are SOC - 1 or II (Type 2), ISO 27001/27002 and/or PCI-DSS.
(iii) Firewalls: The connectivity between your company and the CSP must utilize firewalls to protect your company's networks. Only the minimum number of protocols/ports that are required for business must be configured through the firewalls.
(iv) IDS/IPS: An Intrusion Detection/Prevention System must be utilized in order to protect your company's network from malicious activity originating from the cloud providers network.
(v) Access Controls: There must be a mechanism to authenticate and authorize users that are likely to utilize the data. Formal de-provisioning process must also exist to remove users that are no longer with the company or no longer have a need to access the information. Access controls must meet your company's established policies and standards for account and password management etc.
(vi) Encrypted Transmission: The channel of communication between your company and the CSP must utilize SSL encryption to protect the data in transit.
(vii) Vulnerability Scanning: All VMs and systems deployed within the cloud must be in scope for vulnerability scanning at least annually.
Conclusion
A common sense risk-based approach needs to be considered when evaluating cloud based services for computing or storage requirements. Based on the nature of the data, the security controls should equal or exceed those expected in conventional data centers. The focus should be on the protection of data in the cloud as well as the protection of the circuit that connects company networks to those of the cloud service provider.
Business units who have an interest in cloud based services for their business needs must ensure that they completely understand the associated risks and security requirements and are able to establish internal processes to validate that the controls are in place and are exercised on an ongoing basis.





