It happens several times a week—52 weeks a year.
PR agencies contact SecureWorld writers about an unsecured data bucket in the cloud that potentially exposed thousands, hundreds of thousands, or even millions of data records.
"And if you are covering this story today," the PR person says, "here is a quote from cybersecurity firm XYZ on the mistakes the company made."
It's a sign of the times, isn't it?
Everyone seems to be in the cloud, and misconfigurations seem to be everywhere.
However, they are far from the only cybersecurity vulnerability in the cloud. And the U.S. National Security Agency (NSA) recently issued a key document that can help keep your data and services in the cloud secure.
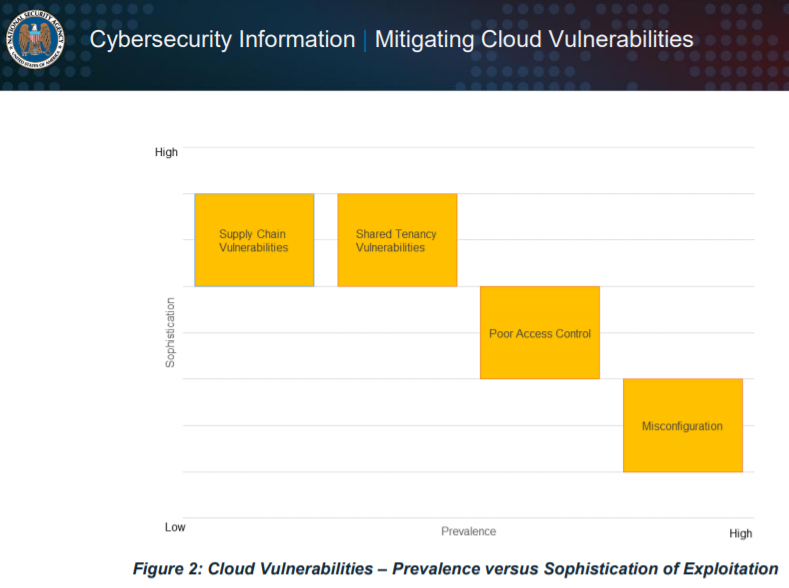
4 main classes of cybersecurity vulnerabilities in the cloud
The NSA says there are four classes of security vulnerabilities in the cloud. This includes supply chain vulnerabilities, shared tenancy vulnerabilities, poor access controls, and yes, misconfigurations.
This NSA chart shows the prevalence of the cloud security vulnerability versus the skill level required to exploit it:
Let's take a look at each of these.
Cloud security: misconfiguration vulnerabilities
The NSA says misconfigurations are the most common type of cloud security vulnerability. These really hurt because they are self-inflicted.
At SecureWorld cybersecurity conferences, leaders have told us repeatedly that misconfigurations most likely result from a lack of training and/or a lack of understanding around the shared model of cybersecurity in the cloud.
We've also previously written about a single toggle to secure AWS S3 buckets. And the NSA lists a host of things you can do to avoid this vulnerability.
For organizations to enforce least privilege, administrators should at minimum:- Use cloud service policies to prevent users from sharing data publicly without a mission-justified role;
- Use cloud or third-party tools to detect misconfigurations in cloud service policies;
- Limit access to and between cloud resources with the desired state being a Zero Trust model;
- Use cloud service policies to ensure resources default as private;
- Audit access logs with automated tools to identify overly-exposed data;
- Restrict sensitive data to approved storage and use Data Loss Prevention (DLP) solutions to enforce these restrictions.
Cloud security: poor access control vulnerabilities
Another prevalent cyberattack in the cloud has to do with vulnerabilities around access control. Often this is due to weak authentication or authorization methods or is linked to vulnerabilities that bypass these methods.
The National Security Agency shared a couple of recent examples that federal agencies investigated:
- In October 2019, a CSP reported cyberattacks in which cloud accounts using multi-factor authentication (MFA) were compromised through password reset messages sent to single-factor authentication email accounts.
- In March 2018, FBI reported about the Iran-based Mabna group bypassing MFA by using alternate single-factor protocols for a cloud-based email service.
Here is what the NSA says are best practices for access control security in the cloud:
- Use MFA with strong factors and require regular re-authentication;
- Disable protocols using weak authentication;
- Limit access to and between cloud resources with the desired state being a Zero Trust model;
- When possible, use cloud-based access controls on cloud resources (e.g., CSP-managed authentication between virtual machines);
- Use automated tools to audit access logs for security concerns;
- Where possible, enforce MFA for password resets;
- Do not include API keys in software version control systems where they can be unintentionally leaked.
Cloud security: shared tenancy vulnerabilities
Now, let's look at a more rare security vulnerability in the cloud that takes a high level of skill to exploit; it's called shared tenancy.
As you are probably aware, cloud platforms involve a number of software and hardware components. Adversaries who are able to determine the
software or hardware used in a cloud architecture could take advantage of known vulnerabilities and elevate privileges in the cloud.
Security researchers have demonstrated possibilities in this area. And now the NSA says it has compiled this list of best practices to mitigate the risk from this type of sophisticated attack. These involve separating resources:
- Enforce encryption of data at rest and in transit with strong encryption methods and properly configured, managed and monitored key management systems;
- For DoD organizations, use DoD CCSRG accredited cloud services;
- For especially sensitive workloads, use dedicated, whole-unit, or bare-metal instances, reducing the risk of an adversary collocating and exploiting a hypervisor vulnerability to gain access to your resources;
- For sensitive workloads, use virtualization for isolation instead of containerization when available;
- When considering the use of a cloud service (e.g., serverless computing) understand the underlying isolation technology (e.g. virtualization, containerization) and whether it mitigates risk for the intended use;
- Select cloud offerings that have had critical components evaluated against National Information Assurance;
- Partnership (NIAP) Protection Profiles (PPs), particularly hypervisors that have been evaluated against the NIAP Server Virtualization PP.
Cloud security: supply chain vulnerabilities
This fourth class of attack against the supply chain is rare, sophisticated, and mainly the responsibility of cloud service providers, according to the NSA.
It lists a couple of examples of supply chain security threats, although these are not specific to the cloud:
- In the ShadowHammer operation, downloads from live update servers were modified to add malicious functionality. Half a million users downloaded the software, although analysis of the software showed the actor's goal was to attack specific hosts by targeting MAC addresses.
- In December 2019, two malicious Python Package Index (PyPI) libraries were discovered stealing credentials from systems where developers unwittingly installed them.
The CCleaner attack, which used millions of infections to download just a few cyberattacks, also seems like it could be on the list.
We won't cover the supply chain vulnerability mitigations here, however you can read more in the NSA Advisory: Mitigating Cloud Vulnerabilities.