Famed hacker Kevin Mitnick learned early on to use emotion to manipulate and socially engineer his targets.
At the time, his targets were typically sysadmins, and the social engineering started with a phone call.
Hacker targets victims with fear
Mitnick says his favorite emotional tool was fear.
He writes about this in his book, "Ghost in the Wires":
"I would call the company I'd targeted, ask for their computer room, make sure I was talking to a system administrator, and tell him, 'This is [whatever fictitious name popped into my head at that moment], from DEC support. We've discovered a catastrophic bug in your version of RSTS/E. You could lose your data.'
This is a very powerful social-engineering technique, because the fear of losing data is so great that most people won't hesitate to cooperate.
With the person sufficiently scared, I'd say, 'We can patch your system without interfering with your operations.' By that point the guy (or sometimes, lady) could hardly wait to give me the dial-up phone number and access to the system-manager account."
Fear repeatedly got Mitnick access to a network so he could create a new account and install a back door to give him a secret way into the system.
And fear is what convinced employees to transfer $18.6 million to hackers in a single week after they were sure their CEO needed them to transfer money for a "highly confidential project."
Without the money transfers the project would fall through. That was the fear.
Security awareness advocate says 'check your emotions'
Now, emotional pleas for coronavirus help or offers of free coronavirus tracking information can lead to malware or even ransomware, which we wrote about in Cybersecurity and the Coronavirus: Are These The Lowest?
And hackers will continue to use emotion an an effective social engineering tool now and into the future, because it works.
KnowBe4 Security Awareness Advocate Erich Kron is an expert in this space. And many of these attacks are not just going after the individual, they are going after the organization, as well.
He says a challenge for organizations now is that many underestimate the sophistication and urgency of Business Email Compromise (BEC) attacks which arrive primarily to the inbox as a phish:
"Sophisticated hackers have moved way beyond misspelled, poorly-formatted emails. Now, they turn the tables on employees, often by using fear as a trigger as if that person needs to act right now to avoid consequences for the organization or the employee."
5 emotions hackers and cybercriminals use against us
Here are five emotions hackers and cybercriminals often use against your employees, your C-suite and board of directors, and you.
1. Greed
Here's an example of a phishing email your employees might receive that uses greed to try to get them to click a link. You've got the inside track on a hot IPO if you click.
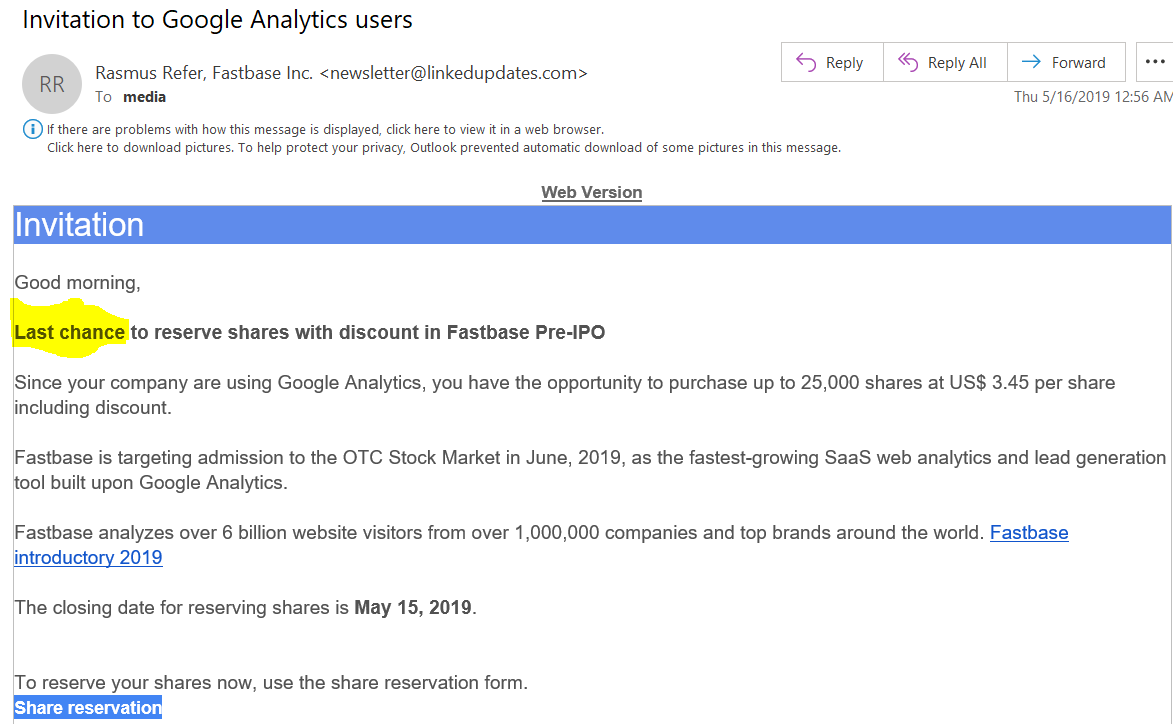
This is your "last chance" to get in on this deal. If your investment does well, maybe you can finally quit your day job!
2. Curiosity
Here's an example of a smishing message that came to an Instagram user on a mobile device.
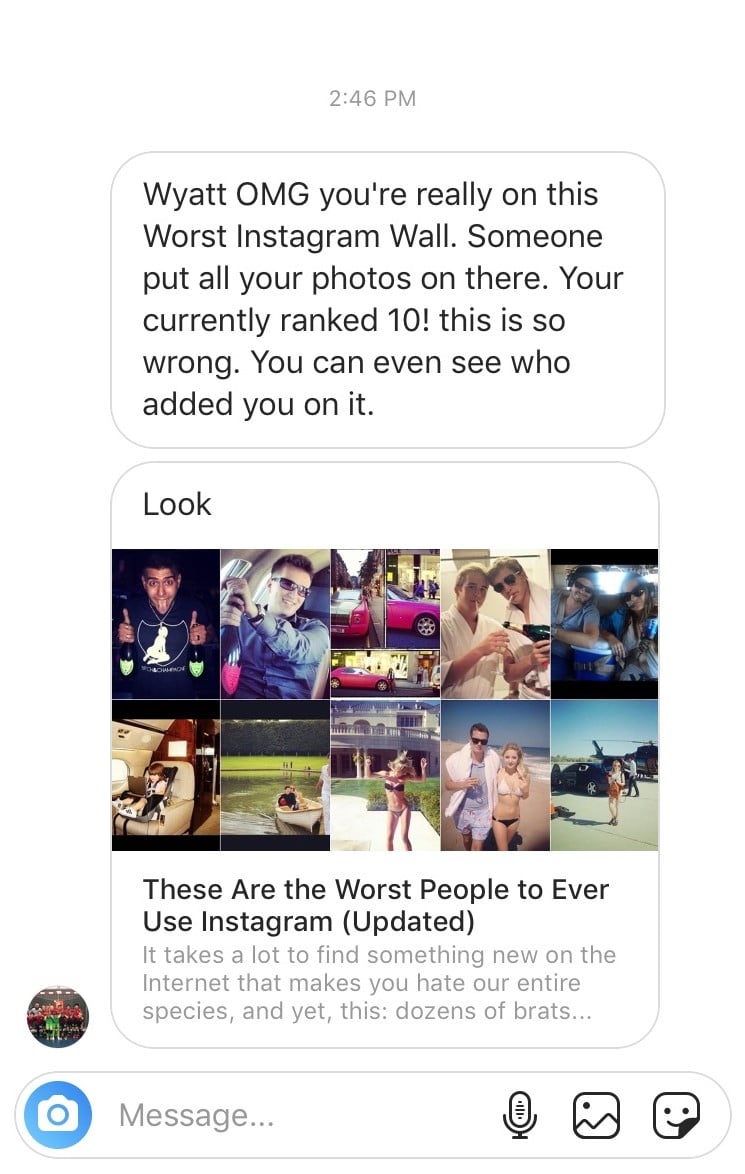
"OMG, you're really on the worst Instagram wall, someone put all your photos on there," says the message. And if that doesn't get you to click, then maybe the closing line will: "You can even see who added you on it!"
Can this really be true? Your end-users may become curious.
And the quality on this next "curiosity" example was low, but the significance was high. After the second Boeing MAX 8 crash, these emails came with a file you could open that claimed to be a leak of data about the risk of flying on these aircraft:
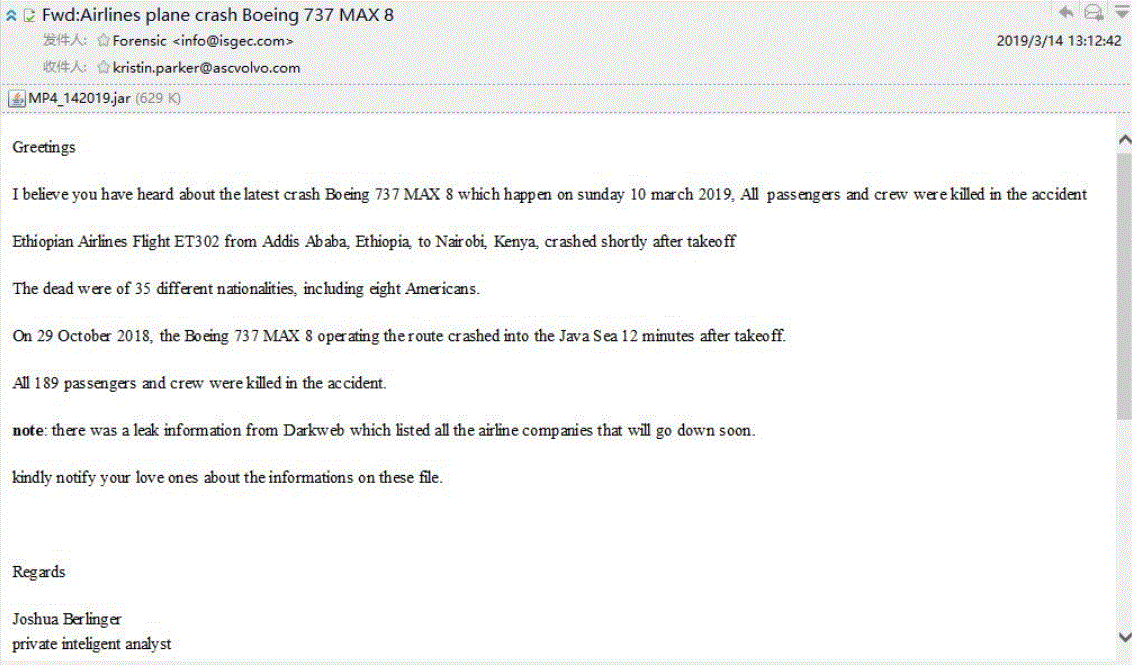
And check out the malicious payload the file delivered, according to the 360 Threat Intelligence Center:
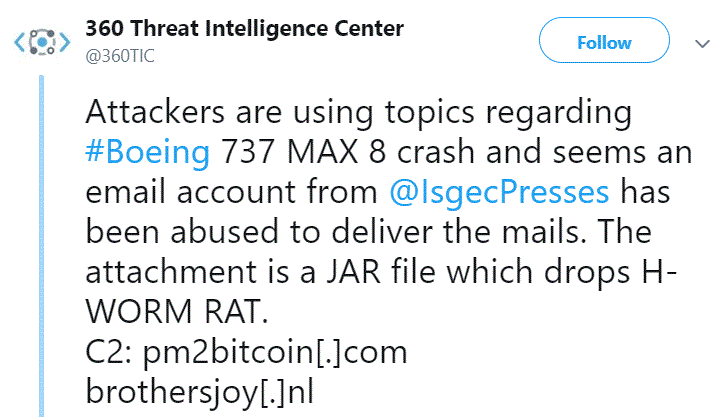
And for our last examples of how hackers use curiosity to kill the cat—er, network—check out these unexpected emails and attachments that appear and make you wonder if someone at the organization actually needs this forwarded to them.
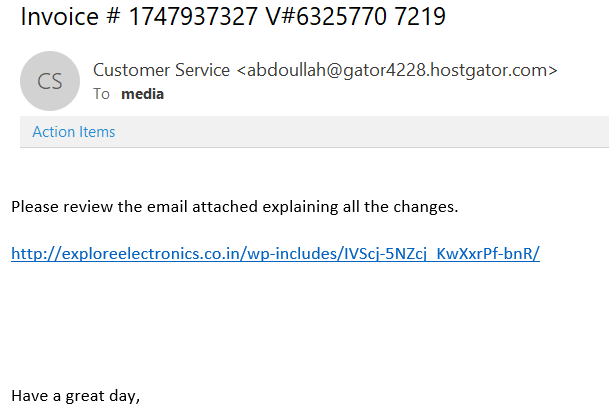
And here's one that could make your employees wonder: did the State Department accidentally share some confidential information with me? Yes, but only for a "short time," according to this phishing example:
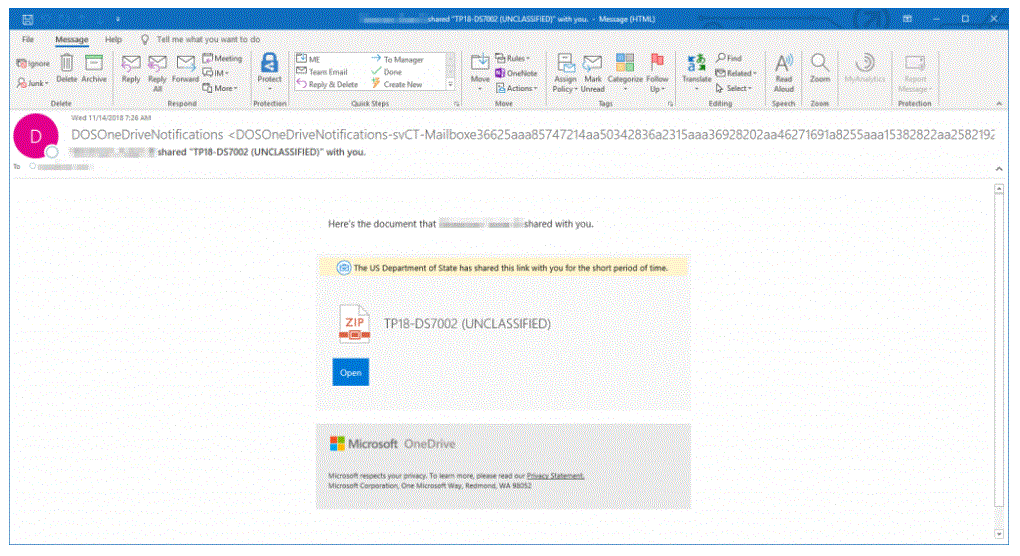
And watch for sophisticated fake invoices which look really good and contain legitimate logos.
3. Urgency
Hackers use fake security alerts like this one—exclamation mark and all. Clearly, it's urgent: "Virus Infection Blocked... Virus will steal and delete your iCloud, Photos and contacts if you don't Act Now."
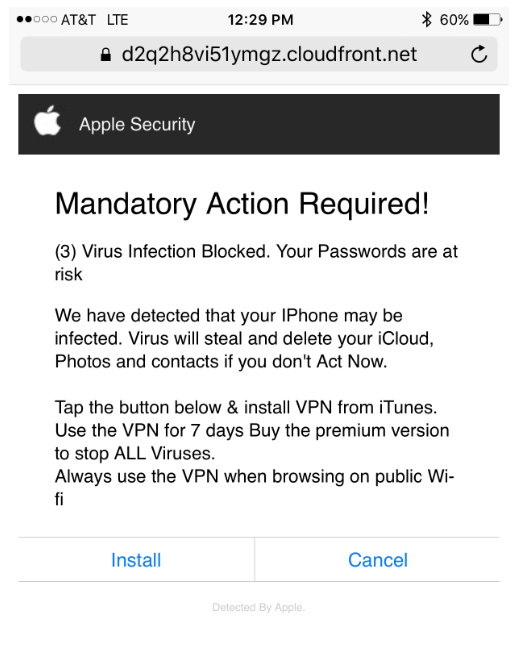
And how convenient, there are two buttons you can click to get phished. Choose Install or choose Cancel and you've been hooked by hackers.
Here's another urgent example that came in via text message or SMS:
.png?width=1189&name=social-engineer-smishing-AMEX%20(2).png)
With Card Alert mentioned three times, AMEX must really need to get a hold of you. Most employees may not notice the http:// is missing the "s" on the end, and honestly, credit card companies do send a lot of alerts these days.
4. Helpfulness
Studies have shown that most of us are willing to help, which is why campaigns asking for help are often very successful. Unfortunately, hackers and cybercriminals use major tragedies to appeal for help—but they are only helping themselves.
Here's an example from the New Zealand mosque shootings that killed more than 50 people in March 2019:
"Cyber bad actors are spoofing Westpac, which is one of Australia’s four major banking organizations and one of the largest banks in New Zealand.
These emails are NOT from Westpac and we advise anyone who receives one to forward it to phishing@westpac.co.nz. If you hover over the link you'll see it goes to a scam site called mothersawakening. The account number they supply is NOT the correct account for donations."
5. Fear
And now, here we are, back with hacker Kevin Mitnick's old friend, fear. Hackers love to use fear against us.
We are seeing this right now in COVID-19 related cyberattacks, like the app that promises to alert you of new cases on "your street" but once you download it, it serves up ransomware instead. And guess what, this part of the attack also uses fear. Pay $100 in Bitcoin or lose your contacts, photos, and everything on your phone.
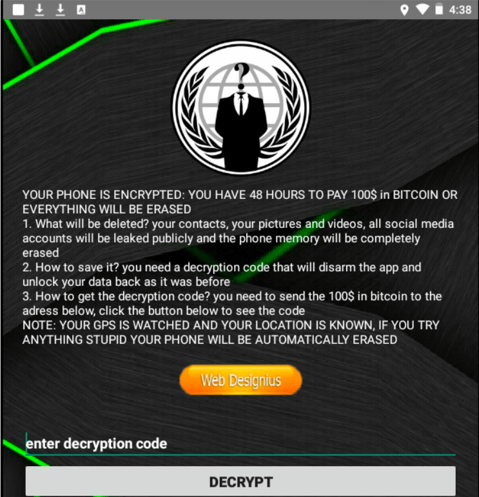
Here's another example of fear.
A security report against my American Express account? I'm afraid I'll get cut off from my account if I don't respond:
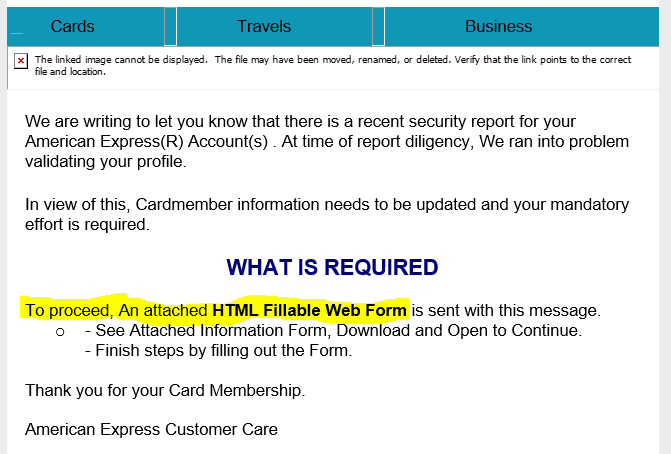
To proceed, all I have to do is open and fill out the attached web form. That makes it so easy for hackers.
And how about the old "someone has accessed your account" phishing routine and you'd better enter your username and password to figure out who it was:
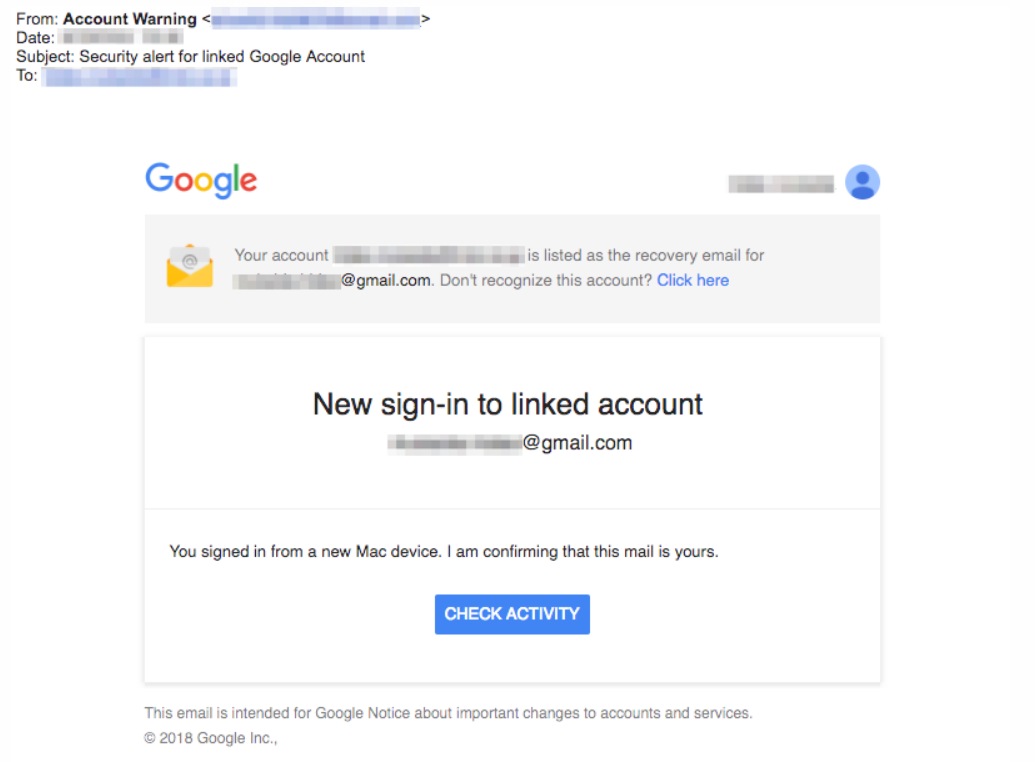
And there are many "account closing" and similar type of phishing emails, often featuring the actual logo of your own bank.
The bottom line on hackers using our emotions against us is that they want us to make an emotional decision about acting "now" before we stop to think things through.
And KnowBe4's Erich Kron says this should be your litmus test when you are going through your inbox:
"If an email comes in and it triggers an emotional reaction—you should step back. That should be a red flag."
Emotion is a red flag that cybercriminals are targeting you in an attack, during the coronavirus and long after the worst of the pandemic has subsided.




