Petya, NotPetya, WannaCry 2, GoldenEye, PetrWrap, PetyaWrap.
The new malware variant that spread like a stink bomb on Tuesday has so many names it's hard to keep up. It's hard to keep up in general with the plague of large-scale cyber crimes that have clogged up our computer screens and news feeds over the past few months.
Whatever name you deem best fitting for this ill-fated malware strain, here are five things you should know regarding the internet's most recent attack.
1. It was not spread through 'traditional' avenuesThe Petya malware family was originally discovered a year ago. However, this new strain uses three separate attack methods to infiltrate your computer. There was no large-scale campaign with links to click on, and no dedicated spear-phishing behind this attack.
Instead, the malware first targets the same vulnerabilities that WannaCry did through the Windows MS17-010 SMB vulnerability. If you did your homework and issued the patch in time, PetrWrap will instead turn to Windows remote execution tool called PsExec. It's already embedded in the malware, so it won't need to be downloaded first.
As a third resort, Petya uses a password sniffing tool called LSADUMP from the Mimikatz toolkit to gain access to other computers on the network with administrative privileges.
2. It's not focused on extorting money
If you were a cyber criminal mastermind, and wanted to make billions of dollars and then retire on a beach in the Bahamas, you'd charge a lot of people a huge ransom fee right?
Except PetrWrap is only charging $300 for the decryption keys. A security researcher referred to as the grugq points out that for such a sophisticated malware, its payment method is pretty weak. NotPetya uses a single, hardcoded Bitcoin wallet that you need to access with a code through an email provider. Can I mail a check instead?
3. But even if you wanted to pay the ransom, you can't
However, even if you wanted to pay the ransom, which you shouldn't, you wouldn't be able to. Posteo, the German email provider that the hacker used to create an account to send money to, has been shut down.
"Midway through today (CEST) we became aware that ransomware blackmailers are currently using a Posteo address as a means of contact. Our anti-abuse team checked this immediately—and blocked the account straight away," Posteo wrote in a blog post. "There was no press coverage at that time. We do not tolerate the misuse of our platform: The immediate blocking of misused email accounts is the necessary approach by providers in such cases."
At the time of publication, NotPetya has brought in about $10,500 from 45 different sources, according to a Twitter account tracking the Bitcoin wallet.
4. Ukraine was hardest hit
Initial reports of the outbreak saw Ukraine as "ground zero" for the attack, with the source supposedly being a tax software tool that was compromised.
However, no matter how it started, multiple banks, both the Kiev metro and airport, and the state power distributor were all among the list of victims in Ukraine.
The Chernobyl nuclear power plant in Russia was also struck by the virus, but radiation levels were maintained, according to shift director Vladimir Ilchuk.
Maersk, a Danish shipping and energy company; WPP, a British advertising firm; and the Madrid office of DLA Piper, an international law firm, were also among those hit with NotPetya.
5. There are similarities to WannaCry, but this could be worse
The PetrWrap malware took advantage of the same Windows security vulnerabilities that WannaCry was famous for. Also like WannaCry, Petya began by using the ETERNALBLUE vulnerability that the Shadow Brokers stole from the trove of NSA exploits. However, even though both malware strains are worms, PetrWrap is spread through local or internal networks only.
Here is a breakdown of the SMB exploit shellcode from Sophos Labs:

Should the SMB exploit fail, it would begin worming through the two other processes outlined above. Unlike WannaCry, there is no over-arching "kill switch," although there is a local one, as discovered by Russian security firm Positive Technologies:
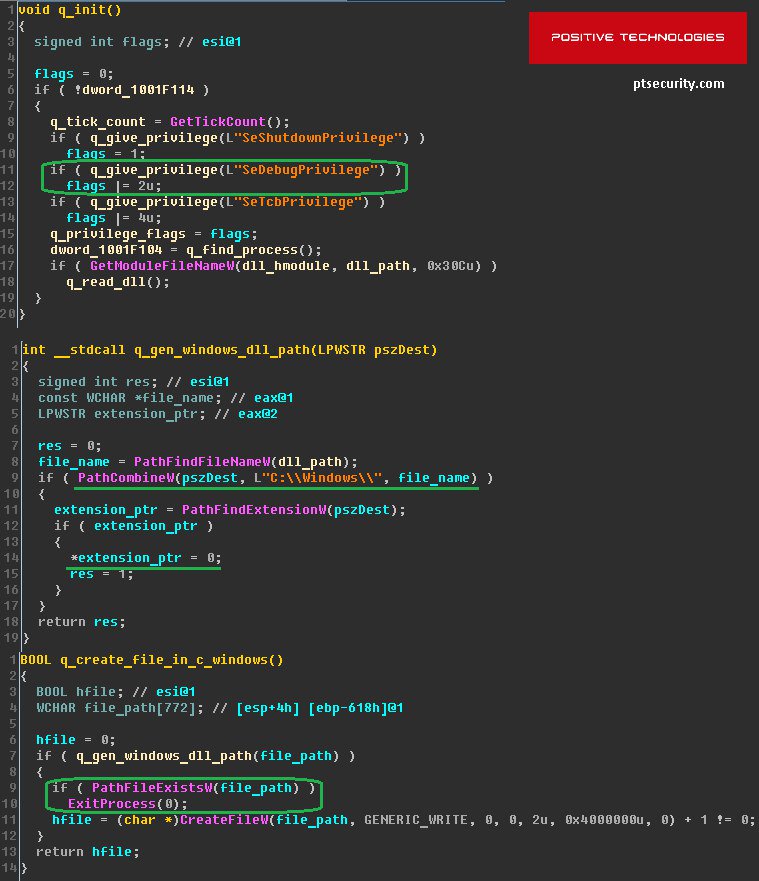
Lenny Zeltser, Vice President of Products at Minerva, said, “Unlike other types of ransomware, the Petya ransomware family appears to be more brutal in the techniques it uses to encrypt files as it goes straight for the hard drive to encrypt the entire machine. Therefore, not only do users lose their data, their entire productivity is shut down as even their Windows operating system won’t run."
PetrWrap is a good reminder that threats are constantly evolving. As hackers are staying ahead of the curve and becoming increasingly creative with their attack methods, we need to be equally vigilant as security professionals.





