"When you start talking about digital transformation, these are typically new technologies and there is a knowledge gap. We don't know what we don't know," says Blake Wood, Director at Thales eSecurity.
Wood spoke during the SecureWorld web conference, The Future of Securing Data Storage, which is available on demand.
He says hackers love digital transformation as much as business does because the newness of it all gives attackers time to poke and prod the technologies and applications to find security holes.
Digital transformation: advancing business, increasing cyber risk
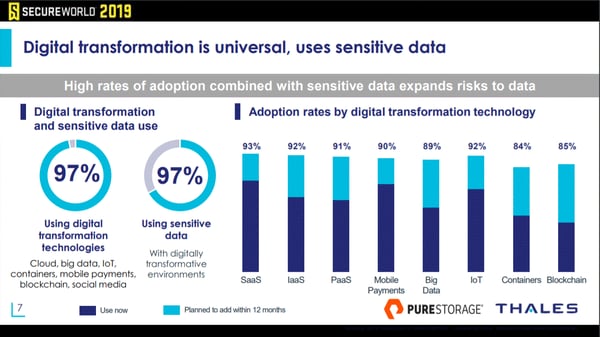
The 2019 Thales/IDC Data Threat Report shows that digital transformation at companies with $100 million in annual revenue (or more) is nearly a given. Click to expand:
That is the good news, you might say. Organizations are taking advantage of new technologies to advance business objectives.
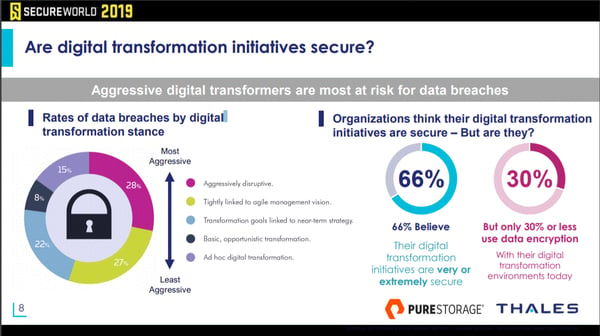
The downside, however, is found on the very next page of the report.
It turns out there is a strong correlation between a more aggressive digital transformation stance and the risk of a data breach.
When transformation becomes more significant, so do data breach rates. Look at the left side of the image below; click to expand:
Using encryption to protect your data in digital transformation
"We need to use encryption. It's a great tool and something I've been working with since my days in the payment industry," Wood says.
Wood then shared encryption fundamentals during the web conference and took a look at what he calls the data protection stack along with the use and best practices around encryption key management.
Data encryption best practices
Here are eight encryption best practices covered during the secure data storage webinar:
- Know the laws, rules, regulations
- Assess data/risks
- Locate sensitive data—where does it live?
- May want to avoid handling/storing certain data types
- Determine the required level of encryption
- Support mixed types of encryption (including tokenization)
- Implement best practices for key management, including centralized key management
- Maintain consistent security policies
New vs. legacy data storage encryption
Part of that may be because there is something lost in translation between data storage teams and IT security teams.
When cybersecurity teams talk about securing the data, storage teams may believe you are asking if the data is secure, meaning protected from failure or loss. They may not be thinking about data security or encryption standards at all.
So Stewart suggests being very specific when communicating with data storage teams.
He also covered encryption's impact on storage efficiency and the falling costs of end-to-end encryption that will make this more cost effective in the future.
And these are just the highlights. The presenters covered key management use cases and best practices, auditing for secure and compliant storage, and much more.
Watch or listen to the SecureWorld web conference, The Future of Securing Data Storage, which is available on demand and helps you earn CPE credits.