News on Wednesday spread like wildfire about a widespread phishing scam that used a seemingly legitimate application impersonating Google Docs.
The scam used Google's ability to create a third-party web application within their system, so that the site appears to come through legitimate Google channels. The app was simply named 'Google Docs'.
Even worse, the actual phishing email may have come from someone you recognize, or had recently corresponded with.
However, since the initial attack, the story just keeps getting weirder.
Here's a brief outline of the scam:
- Victim receives an email from someone wanting to share a Google Doc
- Upon clicking the link, victim gets taken to their actual Google account selection screen
- Victim selects account, and a Google permissions screen pops up
/cdn0.vox-cdn.com/uploads/chorus_asset/file/8459169/gdocphish1.png)
- Victim accepts permission to read, send, delete, and manage your email (yikes!), as well as manage your contacts.
- Scam ensues, and the attacker is able to do all of the above, plus reset your passwords, send out more emails, etc.
What happened next?
Someone appeared on Twitter, calling himself Eugene Pupov, claiming that he was behind the attack. He explained, however, that it was just a test for a final project at Coventry University.

However, Coventry University is denying that he is, or has ever been, a student there.

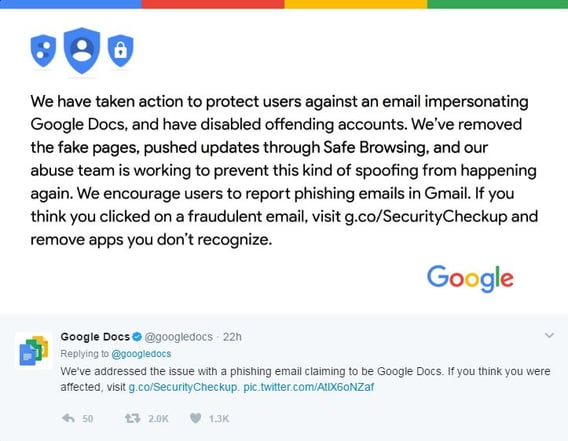
Whether or not Pupov is behind the attacks, Google has since come forth with a statement saying the issue has been resolved.
What if I clicked?
First, make sure to go to myaccount.google.com/permissions and revoke permissions for any apps that seem suspicious.
Next, enable two-step verification on your account. In this particular attack, 2FA wouldn't have saved you, but it can help to prevent other types of attacks.
Third, keep an eye on social media and other sites. In this case, a Google employee discovered the issue from a post on Reddit, and the attack was resolved within an hour by Google. Twitter is also a good warning system.
Lastly, you can report phishing emails directly to Google.
Dan Lohrmann, chief security officer at Security Mentor, sums it up by saying:
"Phishing is usually the path of least resistance for the bad guys to get the sensitive data they want without being detected. If they can become you, they can slowly steal the data over time and cover their tracks as they go deeper and deeper into the network. So once you click on that bad link, what happens next? Popular cybercrime techniques include hidden downloads of malware onto your system, placing keyloggers on your PC to capture keystrokes or using different forms of ransomware to extort cash from victims by encrypting your data and demanding cash for the data back. Additionally, just in case you didn’t get the memo, the litany of major data breach stories that began with the use of phishing attacks is growing by the month."




