Who inserted malware into CCleaner, the software for optimizing PCs, with the express purpose of gaining access to companies like Intel, Sony, Samsung, and Cisco?
That seems to be the question of the day.
Especially when you see the list, which Cisco Talos researchers posted on the company's Threat Intelligence Blog.
They were able to analyze delivery code from a server and found that although 2.27 million computers were infected, the 2nd stage payload was only being delivered to a small subset of computers at high-profile technology companies.
List of technology companies targeted by CCleaner malware
Here is the list of tech targets that researchers at Cisco Talos know about. They even found themselves on the list:
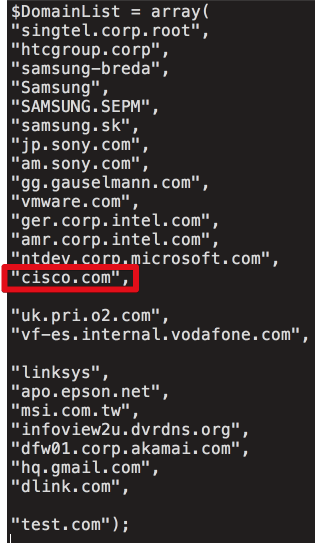
"This would suggest a very focused actor after valuable intellectual property," Cisco researchers said.
Perhaps a nation-state effort? As SecureWorld reported previously, it was a sophisticated attack.
And here's something else that is chilling: this probably is an incomplete list.
It appears a second stage payload was delivered to potentially hundreds of computers based on logs analyzed by Avast, which recently acquired the parent company of CCleaner.
"Specifically, the server logs indicated 20 machines in a total of 8 organizations to which the 2nd stage payload was sent, but given that the logs were only collected for little over three days, the actual number of computers that received the 2nd stage payload was likely at least in the order of hundreds. This is a change from our previous statement, in which
There is more to come on this story. For the latest developments and original stories around cybersecurity, follow SecureWorld on LinkedIn, Twitter, or Facebook.




