If you are looking for best practices when it comes to cloud security and compliance, there are four significant areas to consider.
These areas were discussed in the SecureWorld web conference, Cloudy with a Chance of Breach, which is available on-demand.
1. Cloud security and compliance: your cloud provider MSA
Cyber attorney Rebecca Rakoski focused on legal considerations as you migrate to a cloud environment or operate within it. This includes your Master Service Agreement (MSA) and making sure it protects your data from upload to removal:
"Looking at your data processing agreements, data ownership is key. I can't tell you how many times I've seen cloud service provider contracts where this is an issue. You want to make sure it's clearly delineated and spelled out in the contract. That data is yours and only you can use it," says Rakoski, who is Co-Founder and Managing Partner of XPAN Law Group.
"And look at the data retention and deletion policies, what happens when you leave a cloud service provider. What are their policies when they give it back to you? Are they deleting it, are they retaining it? If they are retaining it, how long are they retaining it?"
She also told the audience that cloud providers try to limit their liability and push it onto you and your organization instead. She offered suggestions for how to limit this, and also looked at many other legal and compliance issues to consider in the cloud.
2. Cloud security: responsibility changes based on environment
"Your responsibility varies depending upon the type of environment you have in the cloud," says Keith Kammer, Principal Market & Competitive Analyst at Code42.
"There are several different types. With your traditional IT environment, you are responsible for the entire environment. Or you can move into Infrastructure-as-a-Service (IaaS), where they simply provide the basic infrastructure and you create your environment. There is Platform-as-a-Service (PaaS), and then you can go all the way to Solution-as-a-Service (SaaS), where you really are only responsible for the access control, administration, and the data itself."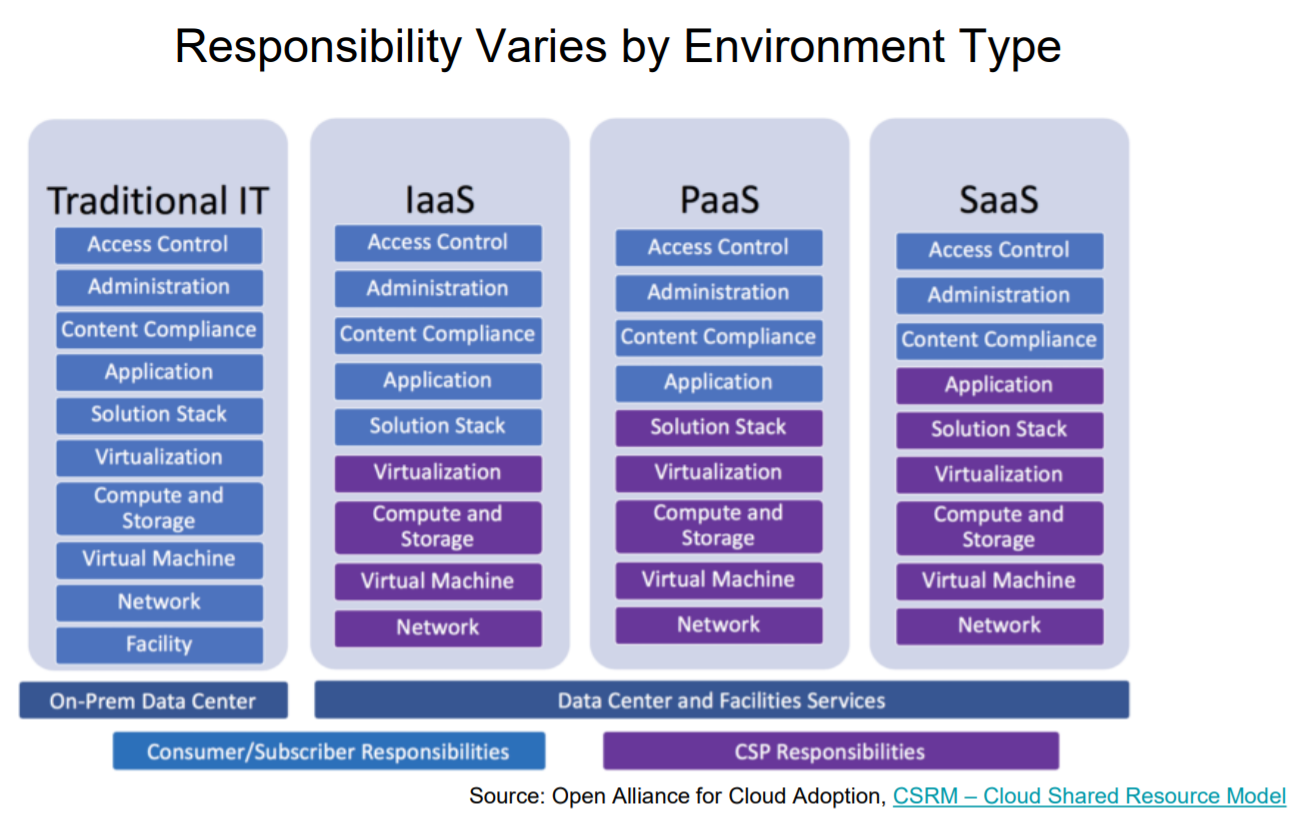
Kammer also covered hybrid cloud environments and shared an overview of attacks against the cloud environment itself and attacks on specific controls that organizations depend on to enable cloud security.
3. Hybrid cloud: IT security and compliance challenges
It's widely acknowledged now that the hybrid cloud is a trend that has taken hold and will continue. This can be any sort of mix of on-premise, private cloud, or public cloud.
And Prashant Gandhi, VP and Chief Product Officer at Big Switch Networks, shared security considerations organizations must handle in the public cloud.
"When we go to public cloud, shared cloud, because of the ease of consuming resources from public cloud, shadow IT has emerged as a security challenge," he says.
"And inconsistent enforcement of security policies is another one. Especially if you have multiple people within the organization implementing policies or not being trained on policies. As well as across multiple clouds.
And finally, when security needs to be enabled through security monitoring tools, you need to have access to the application traffic that is resident in the cloud environment. You need to gain access to this traffic in order to do monitoring."
4. Cloud security and compliance: key management
One thing you are not inherently buying in the cloud is... security.
Nathan Schmidt, who is Sr. Solutions Architect at Thales eSecurity, puts it like this:
"At the end of the day, regardless of how much security is presumed to be good enough or supposedly baked into the new, hot PaaS cloud offering, it can be a false sense of security. You can't simply buy security. You'll have to be an active participant in protecting your data and your customers' data."
He says key management is a crucial part of security in the cloud, and one that goes well beyond compliance issues.
"Key management is an important part of your practice of security. It's about making sure users can interact with your systems safely. The practice of key management includes generating them, using them, the storage of keys, destruction and rotation of keys, the key types, protocols, servers to manage them, and all other compliance related from keys."
Schmidt also covered two growing trends in cloud security: bring your own key and bring your own encryption.
For more details on these four areas of cloud security and compliance, and many other considerations as well, listen to the SecureWorld web conference, Cloudy with a Chance of Breach.
We know the InfoSec community is trying to get cloud security right, and hopefully, these ideas will help.
So far this year at our SecureWorld regional conferences, cloud security has been the first or second most attended session.




