A large multi-national organization knew it had a problem.
The organization was tracking a bad actor in its network.
And with the help of a cybersecurity vendor, it made a surprising discovery that no one saw coming.
How the hacking started and could have been stopped
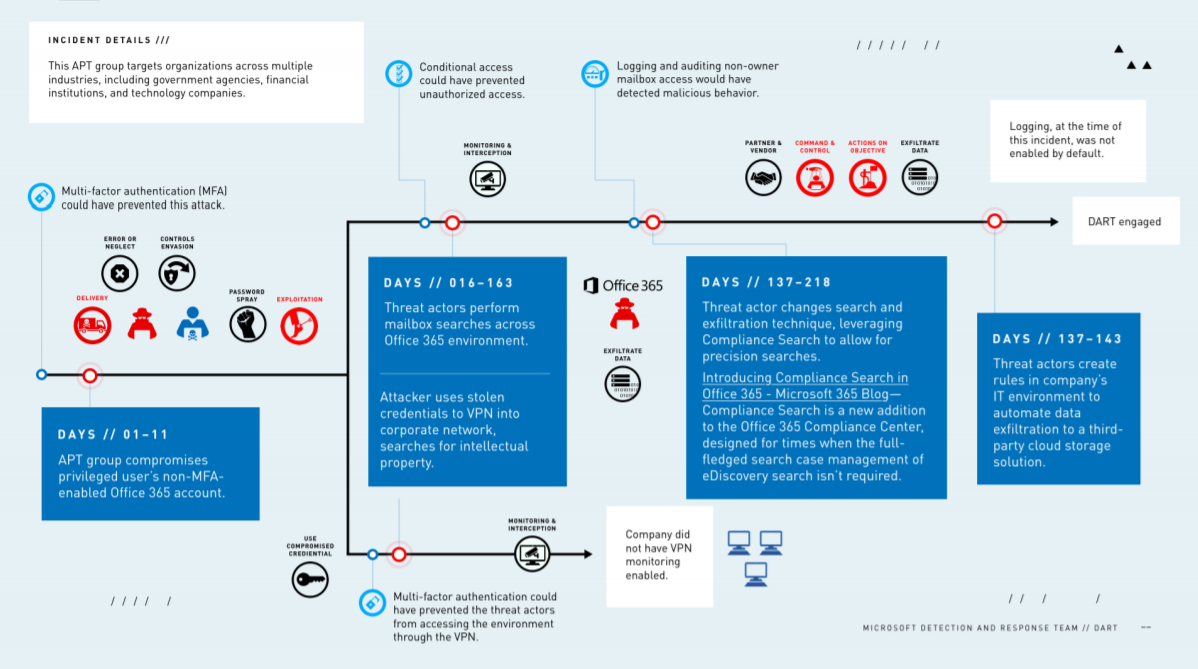
The organization's investigation revealed that the hack started when the threat actor used compromised credentials to access the corporate network.
It was a "password spraying attack" that tried common passwords against O365, where attackers use automated attempts to find a password that can work.
A significant percentage of cyberattacks begin this way.
Once inside the network, the attacker searched and found additional user credentials that had been shared via email.
Here's a really unfortunate part of the story. The first set of credentials the hacker compromised were not for some low-level employee. These were administrator credentials with the kind of privileges you never want in the keyboard hands of hackers.
The admin's account did not have multi-factor authentication (MFA) enabled, or experts say that could have prevented the entire attack.
Instead, the start of the attack was successful and once the hacker was in, they then:
"Used sophisticated techniques to systematically access and transfer data as well as sensitive emails. Despite multiple attempts by the company to remove the malicious actor, it remained in the network for 240 days," according to Microsoft.
Following the 240 days of being unable to shut the attacker out of its system, the organization brought in Microsoft’s Detection and Response Team (DART) to help regain control of the network.
Incident investigation reveals multiple attacks in network
Following a seven-month investigation, the organization brought in DART to work alongside another incident response firm and with its in-house team.
And that's when Microsoft discovered that there was not one attacker in the network, there were six!
"DART quickly identified targeted mailbox searches and
compromised accounts, as well as attacker command-and-control
channels. DART also identified five additional, distinct attacker
campaigns persisting in the environment that were unrelated to the
initial incident. They discovered these attackers had entered the
environment even earlier to establish access channels (i.e., back
doors) for later use as needed."
DART says these were nation-state backed adversaries who might have been detected sooner except the organization was missing some things:
"The company could not see the APT group’s attack coming because they did not have the recommended auditing and logging set up. This was a big factor in the adversaries’ ability to exploit attack opportunities in the company’s environment."
And although Microsoft did not reveal the organization it worked with in this case, it did create a detailed info-graphic which shows multiple ways the attack could have been mitigated at various stages.
Related podcast: Top Nation-State Cyber Threats
Nation-state actors are considered Advanced Persistent Threats. What do these APT actors want and how do they go about it? Listen to this recent SecureWorld podcast for more:




