When SecureWorld reported on the most interesting things from the bust of the world's largest DDoS-for-hire network, WebStresser, we had no idea it would lead to this story.
Haim Zelikovsky, Vice President of Cloud Business for Radware, shared something with us that raises serious questions for those in information security, especially cybersecurity vendors.
He told us: “Also interesting to see how *legitimate* businesses make money from this rogue DDoS-to-Hire industry. Apparently Cloudflare, a low-cost cloud security service, was protecting WebStresser, the world's largest service for paid DDoS attacks!”
At first we wondered, could this really be possible? After all, Cloudflare touts itself as the "#1 Rated DDoS Attack Protection," as you see here:
Surely the "#1 in DDoS defense" company would not defend the #1 site that was launching DDoS attacks, right?
Investigators say WebStresser.org launched at least 4 million cyber attacks worldwide and openly advertised on the web its stresser and booter services.
Says Radware's Zelikovsky, "Personally, I find it hard to believe that someone missed to note the activity of the most popular DDoS-for-Hire tool, WebStresser, in its CDN network."
SecureWorld investigation into Cloudflare
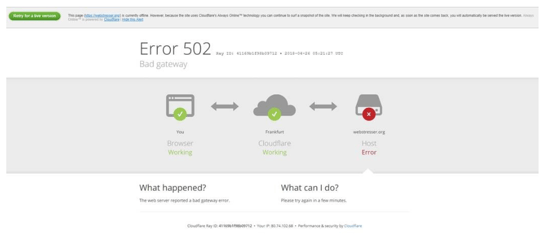
In the face of this accusation, our SecureWorld team started digging. A Google search confirmed several things. First of all, the anti-DDoS vendor was providing DDoS protection to WebStresser.com, as you see below, in this web message from shortly after the site was seized:
Secondly, we learned there have been accusations in IT chat rooms for years that Cloudflare is a "racket" and keeps itself in business by ignoring abuse reports. Reports that could potentially warn the company it is protecting sites that launch DDoS attacks.
Some of the chat comments say that as long as those attacks continue, companies and websites will turn to Cloudflare for protection.

SecureWorld interviews Cloudflare for a response
Of course, you can't believe everything you read on the internet, so we spent time interviewing Cloudflare's General Counsel Doug Kramer, on two separate occasions, to ask about whether the company did indeed make money from its services to WebStresser.org.
He confirmed that WebStresser had a paid subscription account with the company, at times, and a free account at others.
So yes, Cloudflare made some money from the site, but never, he pointed out, by playing a role in the actual attacks.
And Kramer says Cloudflare really lives by its mission of "creating a better internet," but that does not mean policing it.
"We leave those questions to the systems that are in place to enforce those sorts of things, and that's what I think you saw working here. You had law enforcement officials, who we often cooperate with when issues like this come up, made a determination about WebStresser and took action."
He also says critics should look at Cloudflare's role the way the company does:
"We view ourselves as more of a utility service or infrastructure service, that doesn't really care where the water is going or where the electricity is going, we just want to make sure that when you turn on the sink you get all the water you need."
But Radware's VP of Cloud says security companies have a responsibility to deny services to bad actors—something his company takes seriously.
"The question is whether one takes reasonable measures to make sure that he avoids serving bad actors," says Zelikovsky.
"For example, Radware’s Service Level Agreement includes a very rigorous Abuse Clause that allows Radware to terminate the service in case of a reasonable indication of unlawful activity. We take these issues very seriously, and have refused to provide our cloud security services in the past to organizations for which we had reasonable suspicion that are involved in unlawful activities, such as Darknet services."
SecureWorld would like your opinion
We would like to hear from you on this one:
Do cybersecurity vendors have a responsibility to try to limit their services to bad actors?
Or is it okay for vendors to serve any company, no matter what they are up to?