The U.S. Department of Justice (DOJ) made a surprise announcement this week: it was able to recover more than $2 million of the ransom money Colonial Pipeline had paid to a cybercrime gang.
But with the ransom being paid in Bitcoin, how could this happen?
After all, the conventional wisdom is that ransomware gangs demand cryptocurrency so they can move the funds anonymously and with impunity. In other words, so they don't get caught. And so the money stays out of the hands of law enforcement.
This time, it didn't work out that way. So what happened? How did the U.S. DOJ track, seize, and recover the crypto?
How did the U.S. government track pipeline ransomware payment?
Colonial Pipeline's CEO made the decision to pay the ransom just hours after learning of the May 7, 2021, cyberattack against the company. And when he did, the payment flowed across an unchangeable ledger: the public blockchain.
{RELATED: Colonial Pipeline CEO: Paying Ransom 'Right Thing to Do for the Country']
While the money was flowing out, the Colonial Pipeline team also did something else: they notified the FBI of the attack and their decision to pay a ransom.
As it turns out, that was key in tracking the money. But how, exactly, did the DOJ do it?
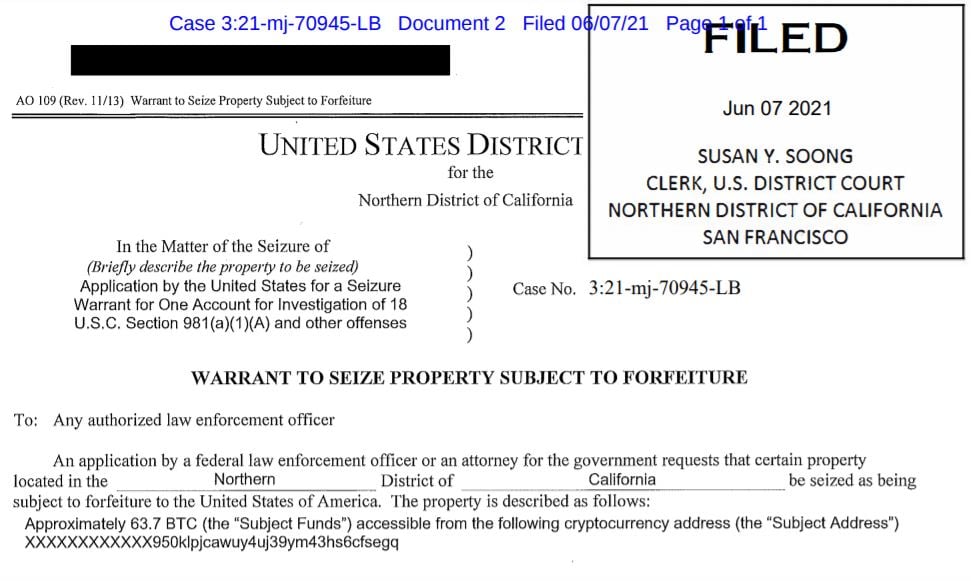
SecureWorld found the answer in the court documents that okayed the Bitcoin seizure:
"As alleged in the supporting affidavit, by reviewing the Bitcoin public ledger, law enforcement was able to track multiple transfers of bitcoin and identify that approximately 63.7 bitcoins, representing the proceeds of the victim's ransom payment, had been transferred to a specific address, for which the FBI has the 'private key,' or the rough equivalent of a password needed to access assets accessible from the specific Bitcoin address.
This bitcoin represents proceeds traceable to a computer intrusion and property involved in money laundering and may be seized pursuant to criminal and civil forfeiture statutes."
It says the ransom payment was made to Russian-affiliated group DarkSide. The amount recovered was worth $2.3 million of the original ransom. The original ransom payment was more than $4 million, however, Bitcoin's value has dropped significantly since the ransom payment was made.
How significant was this recovery of a ransomware payment?
In addition to how the DOJ seized the money, Deputy Attorney General Lisa Monaco shared considerable details about the DarkSide cybercrime group and why this Bitcoin seizure is an apparent milestone.
"DarkSide is a ransomware-as-a-service network—that means developers who sell or lease ransomware to use in attacks, in return for a fee or share in the proceeds. DarkSide and its affiliates have digitally stalked U.S. companies for the better part of the year, and indiscriminately attacked victims that include key players in our nation’s critical infrastructure.
Today, we turned the tables on DarkSide.
By going after the entire ecosystem that fuels ransomware and digital extortion attacks—including criminal proceeds in the form of digital currency—we will continue to use all of our resources to increase the cost and consequences of ransomware and other cyber-based attacks.
The seizure announced today was conducted as part of the Department's recently launched Ransomware and Digital Extortion Task Force, which was established to investigate, disrupt and prosecute ransomware and digital extortion activity. This is the Task Force's first operation of this kind."
And, as it turns out, it is the kind of operation law enforcement has been conducting for a long time—but with a 21st century twist.
"Following the money remains one of the most basic, yet powerful tools we have. Ransom payments are the fuel that propels the digital extortion engine, and today's announcement demonstrates that the United States will use all available tools to make these attacks more costly and less profitable for criminal enterprises."
Justice Department warning about ransomware threats
According to Webster's Dictionary, the legal definition of a clear and present danger is a risk or threat to safety or other public interests that is serious and imminent.
Deputy Attorney General Lisa Monaco used those terms when talking about ransomware:
"In this heightened threat landscape, we all have a role to play in keeping our nation safe. No organization is immune. So today I want to emphasize to leaders of corporations and communities alike—the threat of severe ransomware attacks poses a clear and present danger to your organization, to your company, your customers, your shareholders, and your long-term success."
How did hackers gain access to Colonial Pipeline?
We're also learning more about the Colonial Pipeline ransomware attack vector. The attack led to a shut down of the highest volume fuel pipeline in the United States.
For some cybersecurity incidents, the root of the problem can be so simple it is hard to believe that it caused a major problem. For example, an employee using the same password for multiple accounts.
Or, in this case, one of the largest fuel distributors in the United States having an unused but active VPN account—an outdated VPN account that had its password leaked on the Dark Web.
Bloomberg interviewed Charles Carmakal, Senior Vice President at Mandiant, and uncovered the details of this DarkSide attack:
"Hackers gained entry into the networks of Colonial Pipeline Co. on April 29 through a virtual private network account, which allowed employees to remotely access the company's computer network. The account was no longer in use at the time of the attack but could still be used to access Colonial's network," said Carmakal in an interview.
The account's password has since been discovered inside a batch of leaked passwords on the dark web. That means a Colonial employee may have used the same password on another account that was previously hacked. However, Carmakal said he isn't certain that's how hackers obtained the password, and he said investigators may never know for certain how the credential was obtained.
The VPN account, which has since been deactivated, didn't use multifactor authentication, a basic cybersecurity tool, allowing the hackers to breach Colonial's network using just a compromised username and password. It's not known how the hackers obtained the correct username or if they were able to determine it on their own.
Carmakal adds that FireEye Mandiant conducted an "exhaustive search" to try to determine how the ransomware group got the credentials, but they found no evidence of phishing or any other activity relating to the attack.
A ransomware attack that just got $2.3 million cheaper for Colonial Pipeline thanks to the DOJ seizure of Bitcoin which was on its way to cybercriminals.





