Is this happy looking young man the face of evil? Perhaps.

The U.S. government says he is the face of a Russian cybercrime group called Evil Corp.
And the Department of Justice (DOJ) just unsealed charges which paint him as a kingpin of cybercrime.
"For over a decade, Maksim Yakubets... led one of the most sophisticated transnational cybercrime syndicates in the world," said U.S. Attorney Scott Brady.
Now, there is a $5 million reward to help track him down.
Dridex malware's leader, and how the malware steals your money
The new charges are part of a sweeping 1-2-3 punch against the man, the crime group, and its money.
The DOJ says under Yakubets' leadership, the crime syndicate developed and deployed multiple types of computer attacking malware and stole hundreds of millions of dollars from both individuals and banks.
Among cybersecurity leaders in our SecureWorld communities, the most discussed malware linked to this case is called Dridex.
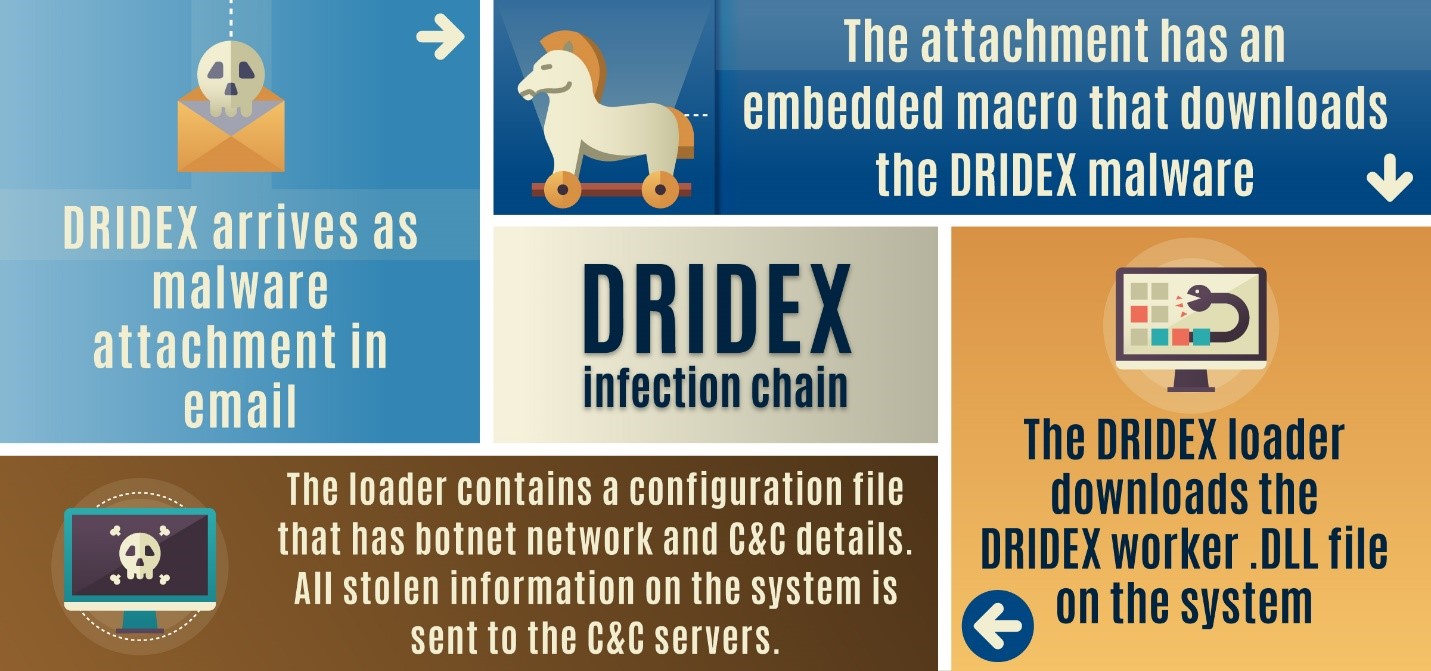
In plain English, Dridex is computer malware designed to capture what you type. It begins with a phishing email containing an attachment. If you open that attachment, it installs the malware onto your device.
The operators of the malware aren't concerned with what you're typing into something like a Facebook post.
Instead, they want the username and password to your bank accounts and that of financial institutions where you have money.
And here's something scary: they know when you log into your bank.
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) explains it like this:
"The primary threat to financial activity is the Dridex's ability to infiltrate browsers, detect access to online banking applications and websites, and inject malware or keylogging software... to steal customer login information."
In some cases, the Dridex malware allows hackers to hijack a computer session to present a fake online banking webpage to trick users into entering personal and financial information.
Security researchers also found some variations of Dridex which can record screen shots of what you are doing and typing. And increasingly, Dridex is changing to try to avoid detection by anti-virus programs.
When the attackers get your banking credentials, they can withdraw or transfer your hard-earned money, just like they are you.
The victims of Dridex malware
Sadly, there is a very human side to what Evil Corp and Maksim Yakubets are accused of doing.
Victims have lost an incredible amount of money to these attacks—upwards of $100 million.
The United Kingdom's National Crime Agency (NCA) also worked on this investigation, and Rob Jones of the agency's Cyber Crime Unit talked about the impact to victims:
"Following years of online pursuit, I am pleased to see the real world identity of Yakubets and his associate Turashev revealed. Yakubets and his associates have allegedly been responsible for losses and attempted losses totalling hundreds of millions of dollars. This is not a victimless crime, those losses were once people's life savings, now emptied from their bank accounts."
Dridex and the operators behind it have virtually attacked customers at more than 300 banks in 40 different countries.
These Dridex attacks can also cause you and your account to be linked to money laundering.
With control of your bank account, cybercriminals can move money through it. Your account could become a transfer point as stolen money travels from a cybercrime victim to your account and then moves onward to a hacker's bank in another country.
This is a typical way of moving money after Business Email Compromise (BEC) attacks have occurred. Listen to our recent podcast where we interview a top investigator at the U.S. Secret Service about that type of cybercrime and the business model attackers are using:
Financial sanctions against Dridex creators cybercrime group
At about the same time that the U.S. Department of Justice announced charges against Yakubets and an associate, the U.S. Department of Treasury announced financial sanctions to try to slow the group's ability to move money.
"Treasury is sanctioning Evil Corp as part of a sweeping action against one of the world's most prolific cybercriminal organizations. This coordinated action is intended to disrupt the massive phishing campaigns orchestrated by this Russian-based hacker group," said Steven T. Mnuchin, Secretary of the Treasury.
"OFAC's action is part of a multiyear effort with key NATO allies, including the United Kingdom. Our goal is to shut down Evil Corp, deter the distribution of Dridex, target the 'money mule' network used to transfer stolen funds, and ultimately to protect our citizens from the group's criminal activities."
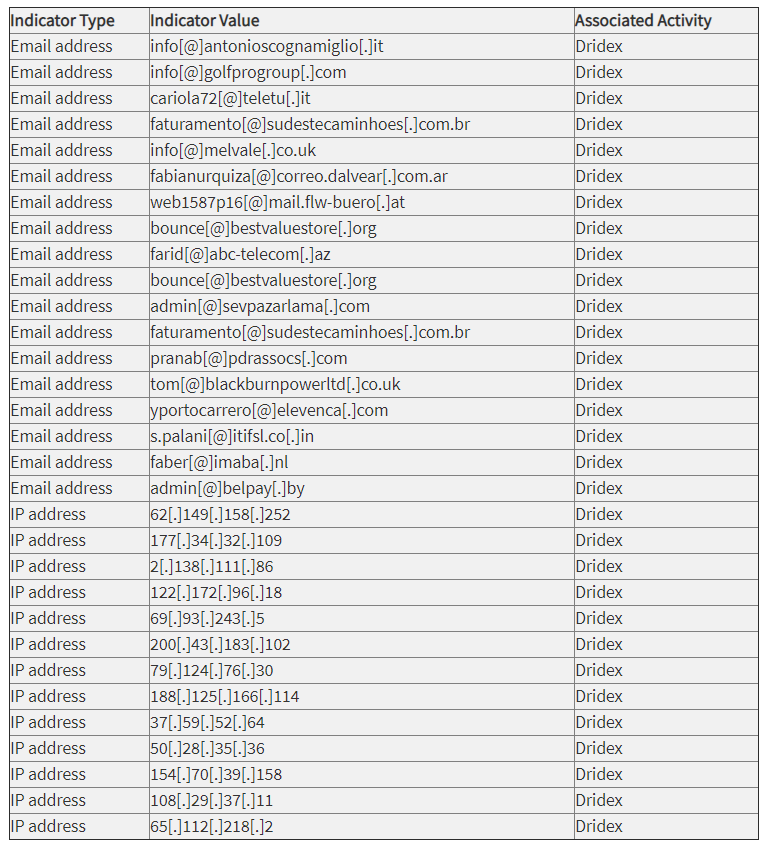
Dridex malware: new indicators of compromise
Treasury and CISA also issued new indicators of compromise (IOCs), including a list of accounts and IP addresses known to be used by Evil Corp to deliver the Dridex malware to victims:
Downloadable IOC files are here:
And the agencies confirmed that the hackers are most likely to attack banks in English-speaking countries through massive spam campaigns—in some cases, sending millions of infected messages per day.
Dridex creator: the $5 million manhunt
Now, a global law enforcement fund is putting a $5 million bounty up for grabs if you help find Maksim Yakubets and he faces his charges in court.
But don't count your reward money before it's hatched. He's a Russian national, and if he is located in Russia, he and his associates may be out of reach.
"We are dealing with cyber criminals in a foreign country that does not extradite its own citizens unless they want to," says Chris Morales, head of security analytics at Vectra, which uses AI to hunt for cyber attackers.
"If they are indeed found to reside in Russia, it is likely that Yakubets might never be brought to trial in the United States. Perhaps not impossible, but highly unlikely."
However, you never know when charges like these could hit a suspect who might be out of reach right now. One Dark Web criminal got busted when he flew to the United States for a beard competition. Seriously.
Now, back to our original question.
Is Maksim Yakubets the face of evil? Or just the face of Evil Corp?
Either way, he now has a wanted poster and a $5 million bounty as part of the international effort to find him.

READ: United States indictment of Maksim V. Yakubets and Igor Turashev.