The lines continue to blur between personal and business use of technology, even though many organizations have rules about the use of corporate IT assets, including on-premises internet access and employer-issued laptops, tablets, and smartphones.
Whether at work or school, many of us have agreed to “acceptable use” and/or security policies—and soon forgotten or outright disregarded them. Many people are comfortable treating employer-issued devices as their own—even if it means exposing sensitive information, increasing their vulnerability to phishing, or flaunting their organization’s security policy.
Who’s really using your corporate devices?
The 2018 User Risk Report from Proofpoint Security Awareness Training reveals surprising insights about the cybersecurity habits of working adults, including how they use employer-issued devices for personal activities. The report is based on a survey of 6,000 technology users across six countries—the US, UK, France, Germany, Italy, and Australia.
Overall, 25% of respondents said they regularly use corporate laptops or smartphones at home; that number is significantly higher among US respondents (35%). And there’s nothing necessarily wrong with that: In addition to remote employees, many workers are expected to be available when they are outside the office. The problem arises when people use these devices for personal (and potentially risky) activities—a problem compounded when they are connected to unsecured home Wi-Fi networks.
As the following data shows, working adults who use employer-issued devices at home are highly likely to use them for personal activities, including online shopping and gaming. In fact, just 10% of respondents said they do not perform non-work tasks on these devices.
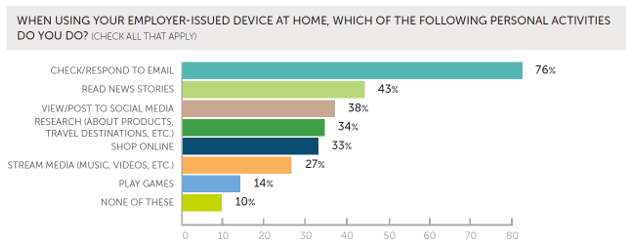
[Source: Proofpoint, 2018 User Risk Report.]
Particularly troubling is that, of those using corporate devices at home, 55% extend access to family members or trusted friends. US respondents were the most permissive: 75% said they grant access to friends and family.
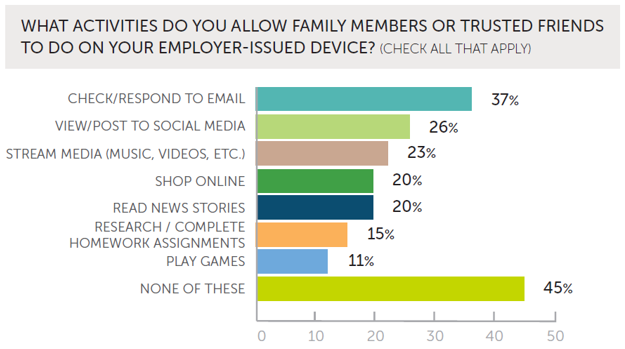
Source: Proofpoint, 2018 User Risk Report.
Why do users violate security policies?
Clearly, allowing friends and family to use one’s corporate device introduces unnecessary risks, and almost certainly violates security policies. But many of the personal activities identified in the survey are things plenty of employees—even infosec professionals—are likely to do at some point. Who hasn’t streamed music from their laptop while working, or occasionally logged in to their personal email account to handle an urgent issue? Bending the rules may seem harmless, but it’s a slippery slope—particularly for untrained employees.
We can only speculate as to why people indulge in these risky behaviors. A Dark Reading article offers several explanations for why employees violate security policies, some of which apply to personal use of corporate devices.
The No. 1 reason? Ignorance. A 2018 survey by market research firm Clutch showed that nearly a third of employees don’t know whether their company has a cybersecurity policy. According to Dark Reading, this indicates that “companies are failing to communicate the rules through effective awareness training and internal marketing.”
Convenience is another reason for violating security policies. While the article focuses on how employees get around cumbersome tools and processes, convenience likely plays a role in how they use corporate devices at home. For example, it’s more expedient to access a private email account on a company device than to stop what you’re doing and start up your own laptop.
The risks of personal email and browsing
Personal email and web browsing can do more than just violate policy. They also increase phishing susceptibility, according to an article on the Proofpoint blog.
“Email is so well suited to attacks that personal webmail, and personal browsing more generally, is now joining corporate email as a major source of compromised accounts and endpoints,” author Mark Guntrip advises. While corporate email gets much of the attention from infosec professionals, employees can also “fall for a phishing attack through their personal webmail on their corporate laptop, which all too often is accessed off the corporate network and its security controls.”
Organizations can use technical controls to mitigate the risks inherent in employees’ personal browsing and email activities. But what about activities like social sharing and extending device access to family and friends? The surest path to better cyber hygiene and improved security postures is to change employee behaviors. Effective security awareness training is essential for teaching end users how to safely manage their email, post to social media, browse the internet, and so on.
Instilling good habits, establishing boundaries
Some overlap between business and personal technology use may be unavoidable. All the more reason why users need to understand your organization’s security policy and be trained to apply cybersecurity best practices—particularly when using corporate devices outside the office. This will help to instill more secure behaviors in your users—even if they do break the rules regarding personal use.
With that said, one boundary should be made crystal clear, both in policy and in direct training: Users should not lend their employer-issued laptops or smartphones to anyone—including coworkers, family members, and friends—unless authorized by your IT team.
Developing an ongoing, comprehensive security awareness training program is essential to establishing boundaries, instilling good habits, and helping users understand the reasoning behind your policies. To learn how to make the case for your training program to management and end users, register for the April 24 SecureWorld web conference, From Skeptics to Champions: Selling the Value of Security Awareness Training Throughout Your Organization.





