You know what football teams do the day after a big loss, right?
They watch
Then they attempt to redeem all of it by correcting those things before the next game.
We imagine this is what it has been like inside the walls of Equifax since it announced its 2017 mega-breach. The InfoSec team has been watching the tape and taking action.
And now all of us get to watch the tape, in a manner of speaking.
The U.S. General Accounting Office (GAO) has just published the most detailed public report yet on the Equifax hack and data breach.
For SecureWorld readers, the most interesting and most educational reading comes from several paragraphs of the 40-page report.
This section goes well beyond the Equifax breach timeline from the company's former CEO.
The GAO report on the Equifax breach reveals technical details of the breach that absolutely should be read by every security team.
Here are the key paragraphs:
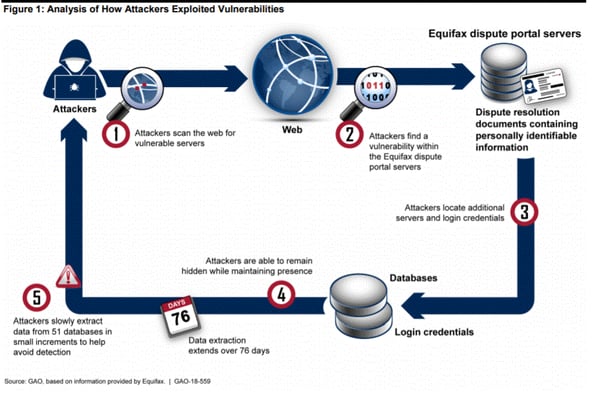
- "... on March 10, 2017, unidentified individuals scanned the company’s systems to determine if the systems were susceptible to a specific vulnerability that the United States Computer Emergency Readiness Team23 had publicly identified just 2 days earlier. The vulnerability involved the Apache Struts Web Framework and would allow an attacker to execute commands on affected systems. 24 Equifax officials stated that, as a result of this scanning, the unidentified individuals discovered a server housing Equifax’s online dispute portal25 that was running a version of the software that contained the vulnerability. Using software they obtained from an unknown source and that was designed to exploit the vulnerability, the unidentified individuals subsequently gained unauthorized access to the Equifax portal and confirmed that they could run commands. No data was taken at this time."
- "According to Equifax officials, beginning on May 13, 2017, in a separate incident following the initial unauthorized access, attackers gained access to the online dispute portal and used a number of techniques to disguise their activity. For example, the attackers leveraged existing encrypted communication channels connected to the online dispute portal to send queries and commands to other systems and to retrieve the PII residing on the systems. The use of encryption allowed the attackers to blend in their malicious actions with regular activity on the Equifax network and, thus, secretly maintain a presence on that network as they launched further attacks without being detected by Equifax’s scanning software."
- "After gaining the ability to issue system-level commands on the online dispute portal that was originally compromised, the attackers issued queries to other databases to search for sensitive data. This search led to a data repository containing PII, as well as unencrypted usernames and passwords that could provide the attackers access to several other Equifax databases. According to Equifax’s interim Chief Security Officer, the attackers were able to leverage these credentials to expand their access beyond the 3 databases associated with the online dispute portal, to include an additional 48 unrelated databases."
- "After reviewing system log files that recorded the attackers’ actions, Equifax officials determined that the attackers then ran a series of queries in an effort to try to extract PII from the databases they had located. Altogether, the attackers ran approximately 9,000 queries, a portion of which successfully returned data containing PII."
- "As before, Equifax officials stated that the attackers were able to disguise their presence by blending in with regular activity on the network. After successfully extracting PII from Equifax databases, the attackers removed the data in small increments, using standard encrypted web protocols to disguise the exchanges as normal network traffic. The attack lasted for about 76 days before it was discovered. Figure 1 depicts an analysis of how the attackers gained access into Equifax’s systems and exploited vulnerabilities."
- "As reported by Equifax, a network administrator conducting routine checks of the operating status and configuration of IT systems discovered that a misconfigured piece of equipment allowed attackers to communicate with compromised servers and steal data without detection. Specifically, while Equifax had installed a device to inspect network traffic for evidence of malicious activity, a misconfiguration allowed encrypted traffic to pass through the network without being inspected. According to Equifax officials, the misconfiguration was due to an expired digital certificate.26 The certificate had expired about 10 months before the breach occurred, meaning that encrypted traffic was not being inspected throughout that period."
- "Equifax officials stated that, after the misconfiguration was corrected by updating the expired digital certificate and the inspection of network traffic had restarted, the administrator recognized signs of an intrusion, such as system commands being executed in ways that were not part of normal operations."
The report also answered a question I've heard asked repeatedly by InfoSec leaders at our regional conferences: What happened with the Equifax patching protocol that allowed a known vulnerability to remain unpatched?
It turns out the email list the company used to alert system administrators of vulnerabilities was out of date.
The people who had responsibility for patching the Apache Struts vulnerability for the web application were not on the email list and were not notified about it.
So when a scan failed to turn up the vulnerability, everyone assumed there was no issue. In reality, the people who might have known better were not even notified. Wow.
These were mistakes made by Equifax. However, we're all more secure if, as a community, we work together to redeem these mistakes by learning from them, one organization at a time.




