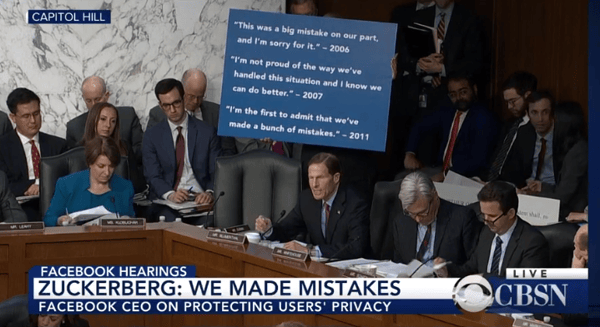
When Facebook CEO Mark Zuckerberg apologized to Congress last year about the Cambridge Analytica privacy scandal, staffers held up a sign of the previous times he'd apologized and questioned whether he was sincere.
Now, we can add another Facebook apology to the list and ask the same question about sincerity.
This time it's the revelation that tens of millions of Facebook users had their passwords stored in plain text for years, and according to Krebs on Security, thousands of employees looked at those files.
Let's take a look at what is being said about this latest breach of privacy and cybersecurity trust by Facebook.
What CISOs are saying about Facebook
Terence Jackson, Chief Information Security Officer at Thycotic, wonders how this came about:
"As a CISO, the first question that comes to mind is, was this a flaw in the system or an accepted risk? Assuming they are following a SSDLC, this should have definitely been a core protection built into the system. Because there is no evidence that anyone external to Facebook had access to the un-encrypted passwords is not reassuring. As a Facebook user, I question why would an internal employee need access to my un-encrypted password?”
That's a good question, indeed.
What Democrat presidential candidates are saying
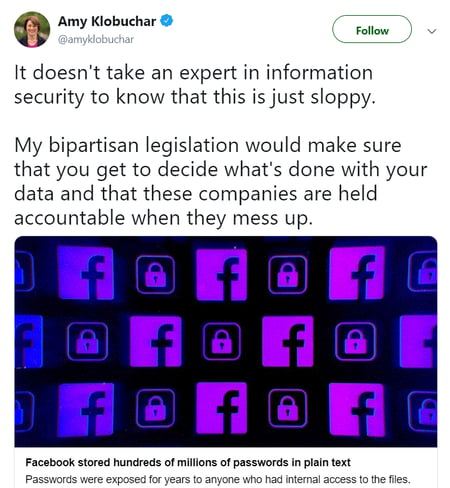
2020 presidential candidates wasted no time in going after Facebook. This includes U.S. Senator Amy Klobuchar, who has often been in the headlines this election cycle:
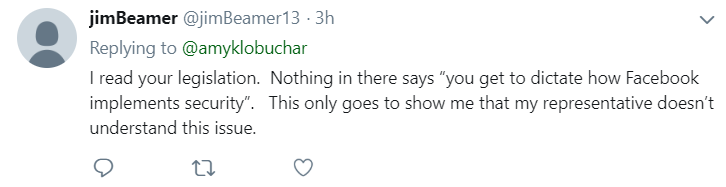
And while her supporters chimed in on the tweet and praised her proposal, others wondered how legislation would actually change things at Facebook:
@jimBeamer replied, "I read your legislation. Nothing in there says 'you get to dictate how Facebook implements security.'"
What Facebook is saying... about Facebook passwords in plain text
Facebook wrote a detailed post on what happened. and here is the part that will reassure everyone in InfoSec:
"There is nothing more important to us than protecting people’s information, and we will continue making improvements as part of our ongoing security efforts at Facebook."
This is good to know.
It says the un-encrypted passwords were discovered during a security review in January, and they include hundreds of millions of Facebook users and tens of thousands of Instagram users.
In the Facebook password post, the company does not explain how things went wrong here, but does say the company is focused on doing things right:
"In line with security best practices, Facebook masks people’s passwords when they create an account so that no one at the company can see them. In security terms, we 'hash' and 'salt' the passwords, including using a function called 'scrypt' as well as a cryptographic key that lets us irreversibly replace your actual password with a random set of characters."
[RESOURCE: 2019 cybersecurity conference calendar]
What those in IT and InfoSec are saying
Brian Krebs broke the story, and some of the most entertaining reading on this latest issue with Facebook is in the comments on that article. Here's an example:
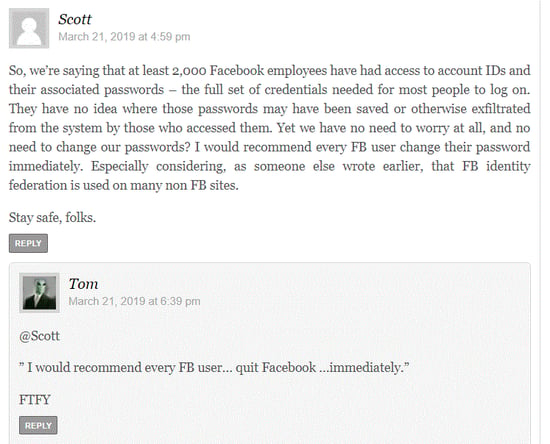
Scott posted, "I would recommend every FB user change their password immediately," and Tom replied, "I would recommend every FB user... quit Facebook... immediately."
You have to appreciate a sense of humor. Or was that actually a joke?
[RELATED: Zuckerberg's 5 Revealing Statements to the U.S. Senate]