As far as we know, it is an unprecedented move by U.S. law enforcement.
Unsealed court documents, reviewed by SecureWorld and shared below, explain a multi-day FBI operation. The agency remotely accessed Microsoft Exchange servers belonging to private companies and organizations in the United States.
The FBI says this stopped an ongoing attack against Exchange servers and remedied an inability by many organizations to end persistent access by nation-state hackers.
Keep reading for details on the FBI's pitch to a judge asking for permission to carry out the plan, and how, exactly, the FBI carried it out.
Then let us know: is this a fantastic approach to shutting down nation-state attacks or a frightening precedent set by the U.S. government?
FBI Exchange server search: fallout from Hafnium breach
It was about a month ago when the U.S. Cybersecurity and Infrastructure Security Agency (CISA) announced discovery of Zero-Day exploits being used to attack Microsoft Exchange email servers.
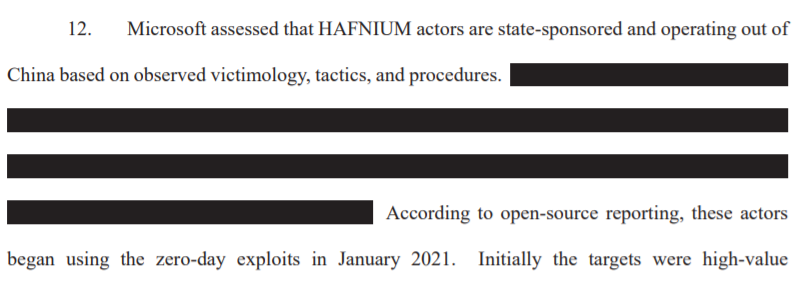
Hafnium, a group believed to be Chinese nation-state hackers, developed or discovered a previously unknown way to secretly access email servers around the globe.
We covered the development as CISA announced the attacks were widespread and indiscriminate.
Following the news of this major attack, CISA and Microsoft issued a flurry of patches and emergency directives. And then this week, CISA announced federal agencies had just 72 hours to complete additional emergency patching of Exchange servers or the agency had to pull the plug on its servers.
What we know now, however, is that the FBI has been taking action behind the scenes. Let's take a look at the reasoning and the operation.
How did FBI get a judge to approve Exchange server search warrant?
The FBI cannot just go around accessing Microsoft Exchange servers on your premises without permission; it needs a warrant to do so. In this case, the Bureau made its case to a federal judge in Texas. The FBI wanted to take secret actions in the name of cyber defense.
Partially unsealed court documents reveal how the FBI made its case. Investigators explained the scope of the problem:
"A public scan of the approximately [redacted] web shells identified by [redacted], conducted on March 31, 2021, revealed that approximately [redacted] web shells were still present on victim servers. Based on my training and experience, most of these victims are unlikely to remove the remaining web shells because the web shells are difficult to find due to their unique file names and paths, or because these victims lack the technical ability to remove them on their own."
The FBI says that many organizations have closed the vulnerabilities on their own through patching and other forensic work. However, it argued to the judge, many organizations may never be able to do this because of a lack of expertise.
And the FBI shared that these web shells were allowing the Hafnium hackers to maintain access into the email servers, meaning the data breach was ongoing.
How would it know this for sure? It was tracking usage of IP addresses known to be operated by the hackers:

The FBI also cited the legal grounds for asking for access, which you can see in the three checked boxes in this document image:
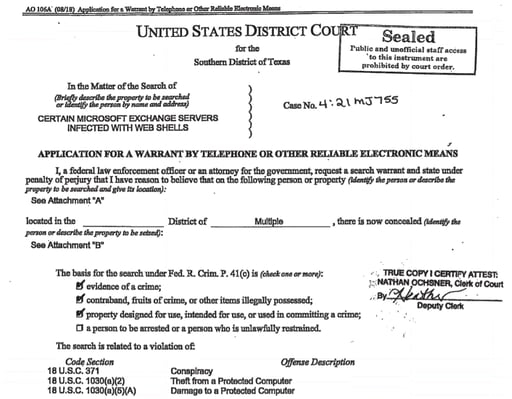
And the investigators explained to the judge that China is likely behind this attack:
FBI Exchange server 'web shell operation' explained
The FBI made its cases for a warrant to remotely access hundreds of Exchange servers in several U.S. states. Next, the FBI explains how it carried out the operation:
"This warrant authorizes the United States to seize and copy from Microsoft Exchange Servers located in the United States the web shells identified in Attachment A, and to delete the web shells from those servers.
As described above, in addition to identifying the Microsoft Exchange Servers, The United States therefore has the technical ability to uninstall the web shells by using those passwords. Using the example described above, FBI personnel will access the web shells, enter passwords, make an evidentiary copy of the web shell, and then issue a command through each of the approximately web shells to the servers to delete the web shells themselves."
What if your server crashed because of the FBI's actions? The FBI says it tested its technique to close off the backdoor access to hackers:
"When conducted through an internal FBI testing process, this command successfully deleted the web shell from an FBI server and did not impact other files or services of the computer. An FBI technical evaluation of the code and a related briefing to an outside expert was also conducted to ensure the code would not adversely affect the victim computers and Microsoft Exchange Server software running on such computers."
Why the FBI says it wanted to keep the web shell action secret
The FBI also asked the judge to delay notification of its actions, citing these reasons:
"...allowing premature disclosure to the public at large or to individual victim users of web shell-compromised Microsoft Exchange Servers would likely seriously jeopardize the ongoing investigation.
Such a disclosure, for example, may give the subjects of this investigation an opportunity to destroy or tamper with evidence or change patterns of behavior.
Disclosure also could prompt the subjects to make changes to the web shells before FBI personnel can act pursuant to the requested warrant, which would enable persistent access, further exploitation of the victims, and defeat the efforts of FBI personnel to identify victims and delete web shells."
The U.S. Department of Justice described the operation as just another piece in the Exchange server attack response.
Assistant Attorney General John C. Demers for the DOJ's National Security Division explains it like this:
"Combined with the private sector's and other government agencies' efforts to date, including the release of detection tools and patches, we are together showing the strength that public-private partnership brings to our country's cybersecurity. There's no doubt that more work remains to be done, but let there also be no doubt that the Department is committed to playing its integral and necessary role in such efforts."
And Acting Assistant Director Tonya Ugoretz of the FBI's Cyber Division says this specific operation is a signal to the nation-state hackers of the world:
"Our successful action should serve as a reminder to malicious cyber actors that we will impose risk and consequences for cyber intrusions that threaten the national security and public safety of the American people and our international partners.
The FBI will continue to use all tools available to us as the lead domestic law enforcement and intelligence agency to hold malicious cyber actors accountable for their actions."
And now, those tools appear to include secret actions in the name of defending U.S. organizations.
Cybersecurity reacts to the FBI Exchange server operations
Tim Wade, Technical Director and Chief Technology Officer at Vectra, says the FBI action answers some questions about the attack, but leaves others to be discussed.
"First, this is a strong indicator of the extent at which these vulnerabilities have been leveraged for nefarious ends, and the risk that the FBI perceives to be present.
Second, this likely also exposes the challenges that individual organizations have in the detection, response, and remediation phases of an attack. At least a subset of those targeted for action by the FBI are likely to have patched, but been insufficiently equipped to fully eradicate the adversary's foothold.
Lastly, however, I do wonder about some of the precedent and legal landscape that will inevitably wander through as a result of activities like this becoming more proactive and prevalent on behalf of the FBI. We'll need to exercise good judgment and due care to preserve the balance between acting in the public good and affording proper protections for private entities."
Rick Holland, Chief Information Security Officer and VP of Strategy at Digital Shadows, says this FBI action raises a number of questions:
"Although the search warrant lays out the statutes authorizing the activity, I wonder what the implications would be for any potential damages that occurred with removing the web shells. The FBI did conduct an 'internal FBI testing process' and also consulted with an 'outside expert,' but anyone that has worked in IT knows that when you remove software, there can be unintended consequences (e.g., bricking a server).
In addition to potential legal actions, if damages occurred, this will undoubtedly raise concerns with privacy advocates and civil libertarians."
However, he also highlights something we've heard often on the SecureWorld conference stage. Most organizations need help in the area of nation-state cyber threats:
"Despite the possible objections, American companies are outgunned and overmatched by nation-state actors like China, Russian, Iran, and North Korea. While it may be controversial for some, this type of activity will be welcomed by others. Effective coordination with the private sector will be critical for the success of this and future operations."
FBI action on Hafnium exploits: fantastic or frightening?
After taking all this into consideration, where do you stand on this FBI action? Is it fantastic or frightening that the FBI may have secretly accessed and changed your organization's Exchange server in the name of protecting you? Let us know by sharing a comment below.
[Supporting documentation: Unsealed court documents in this case]




