We read a lot of breach reports and cybersecurity post-mortems here at SecureWorld.
But this one really stands out.
The agency that insures our bank accounts is failing to insure our Personally Identifiable Information and lacks proper incident response, according to a government report.
FDIC: 18 breaches in two 2 years
This comes from a new report by the Office of the Inspector General that studied 18 confirmed or suspected breach incidents over a two year period at the Federal Deposit Insurance Corporation.
The report says it took nearly 9 months, on average, for the FCC to notify potential PII hack victims:
"In addition, the FDIC did not notify potentially affected individuals in a timely manner for the incidents we reviewed. Specifically, it took an average of 288 days (more than 9 months) from the date the FDIC discovered the breaches to the date that the Corporation began to notify individuals.
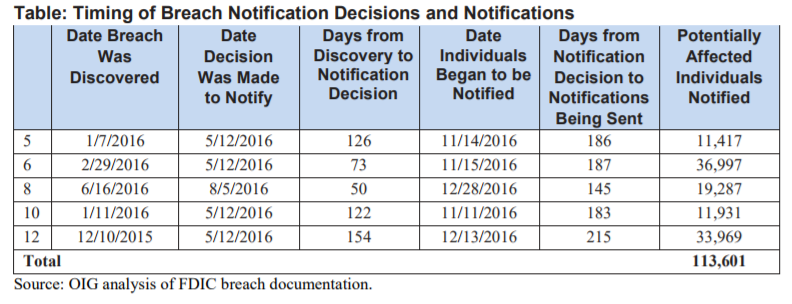
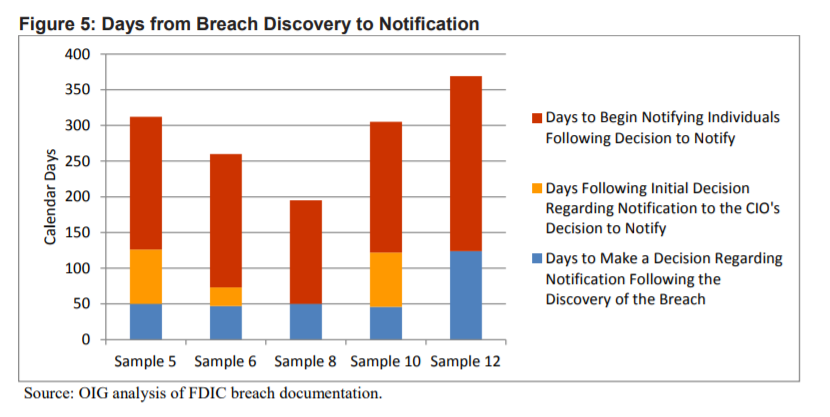 And even when the FDIC decided the breach was worth of notification, several months would sometimes pass before a notification actually occurred as you can see in the chart below.
And even when the FDIC decided the breach was worth of notification, several months would sometimes pass before a notification actually occurred as you can see in the chart below.
And what kind of PII does the FDIC collect? According to the report, "Such PII includes, for example, names, telephone numbers, home addresses, social security numbers, driver’s license numbers, dates and places of birth, credit reports, education and employment histories, and the results of background checks."
We can only imagine what The Privacy Professor would say about this.
4 Ways the FDIC is failing cybersecurity, according to Inspector General report
- FDIC Did Not Complete Key Breach Investigation Activities and Notify Affected Individuals Timely
- "Breach investigations and notifications were not timely because the FDIC did not: have an Incident Response Coordinator to centrally manage its incidents; provide ISMs with adequate training; dedicate sufficient Privacy Staff to manage breach response activities; or take appropriate steps to ensure it was prepared to handle a large increase in required notifications. (Note, NIST guidelines call for an IRC)
- "Breach investigations and notifications were not timely because the FDIC did not: have an Incident Response Coordinator to centrally manage its incidents; provide ISMs with adequate training; dedicate sufficient Privacy Staff to manage breach response activities; or take appropriate steps to ensure it was prepared to handle a large increase in required notifications. (Note, NIST guidelines call for an IRC)
- FDIC Did Not Adequately Document Key Assessments and Decisions
- "Our review of 18 suspected or confirmed breaches found that Incident Risk Analysis (IRA) forms did not clearly explain the rationale behind the overall impact/risk levels assigned to the incidents;"
- "Our review of 18 suspected or confirmed breaches found that Incident Risk Analysis (IRA) forms did not clearly explain the rationale behind the overall impact/risk levels assigned to the incidents;"
- FDIC Needed to Strengthen Controls Over the DBMT (Data Breach Management Team)
- "... the FDIC did not provide DBMT members with specialized training to help ensure the successful implementation of their responsibilities."
- FDIC Did Not Track and Report Key Breach Response Metrics
- "However, the FDIC generally did not track or report the metrics in the DBHG for the suspected or confirmed breaches we reviewed. Absent effective metrics, FDIC managers and other stakeholders lack timely, action-oriented information needed to assess program performance and ensure accountability"
The Inspector General's report on FDIC breach response goes into even greater detail.
For insights and cybersecurity news, follow SecureWorld on LinkedIn, Twitter, or Facebook.




