Looking for information on IoT exploits that cybercriminals are using?
Then follow the money.
That’s what Trend Micro did in extensive new research through top underground hacker forums which operate in Russian, Portuguese, English, Arabic, and Spanish languages.
What are the top 3 findings in IoT security exploits?
According to the report:
1. The Russian language underground is the most mature and best at monetizing IoT attacks.
2. Most monetization occurs through crime-as-a-service to launch DDoS attacks and selling access to botnets of compromised IoT devices.
3. Mirai and its variants will continue to be the most used malware for IoT attacks. You can buy updated versions with more functionality, and tutorials and training on how to use it.
Here is a good summary of the report:
"The Russian cybercrime underground market is the most sophisticated out of all the underground communities we discuss in this paper. The money-driven criminals make up a market thriving with exploits for routers, customized firmware for smart meters, talks of hacking gas pumps, and router-based botnets for sale.
There is a variety of conversations taking place around devices, including less common platforms. Most of these talks have a monetization angle. In general, the Russian underground is a place for business where hacking and technical information are mere details."
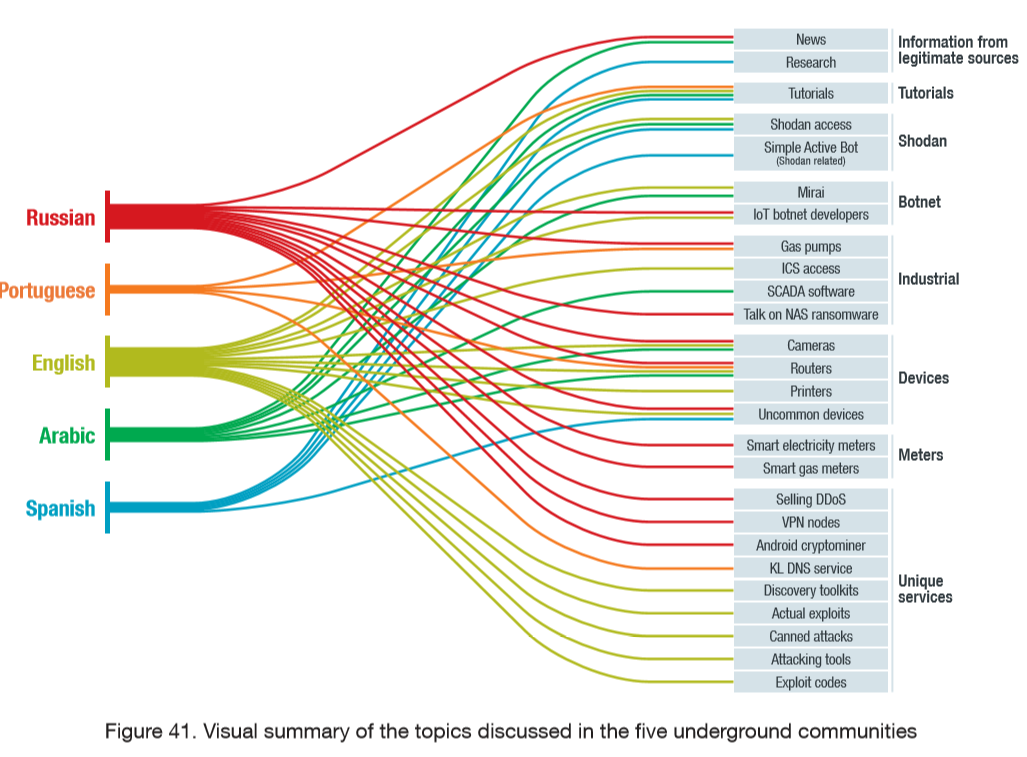
What are hacker forums doing with IoT exploits?
Here is a chart that gives an overview of what cybercriminals are doing with IoT exploits (click for a larger version).
What are specific examples of IoT exploits for sale?
Now, let’s look at some specifics from the research.
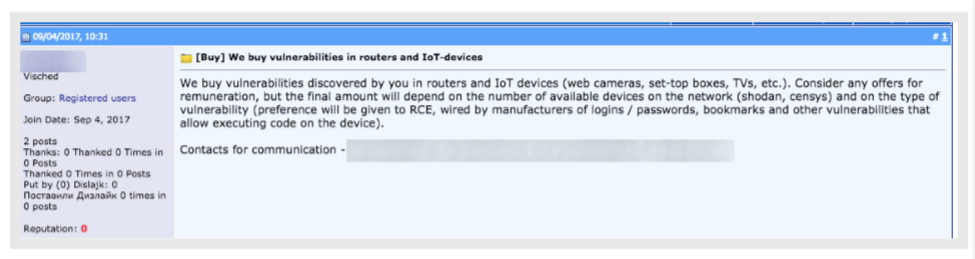
There are cybercriminals looking to buy compromised IoT devices and networks:
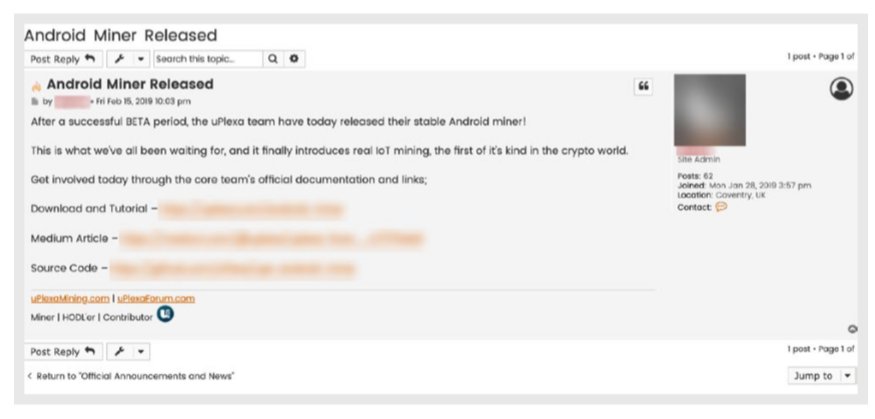
And there are cybercriminals selling brand new IoT exploits, just coming out of testing, such as this Android-based cryptominer:
"After a successful BETA period, the UPlexa team have today released their stable Android Miner… the first of its kind in the crypto world," the Dark Web advertisement reads.
Researchers believe it will not be easily used on Android mobile phones because it would drain the battery too fast. Instead, the impact is more likely on an increasing number of Android-based IoT devices hitting the market.
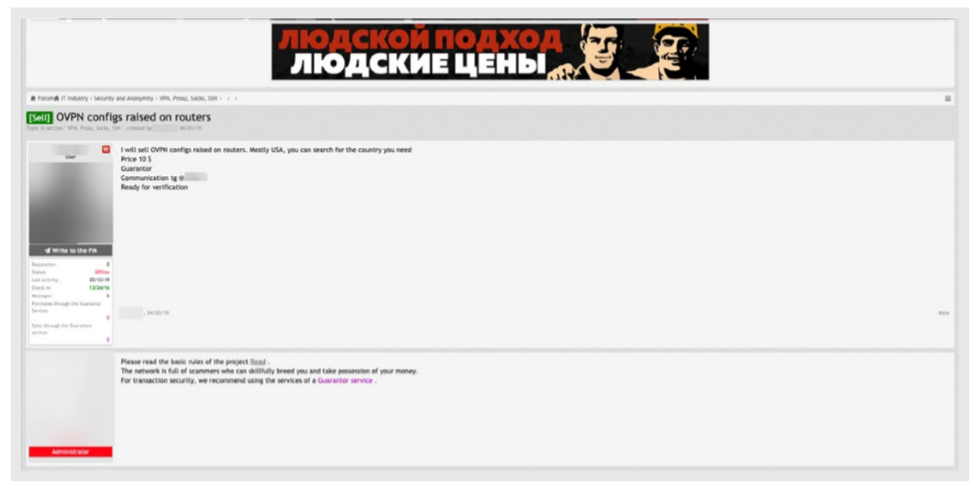
Researchers also found things like compromised VPN proxies for sale, which cybercriminals can use to remain anonymous in their worldwide hops around the web.
And you can also buy direct access to compromised IoT devices, some by brand name. Here is an advertisement for the “Nest Shop” and the compromised Nest data streams from homes and businesses that you can purchase access to:
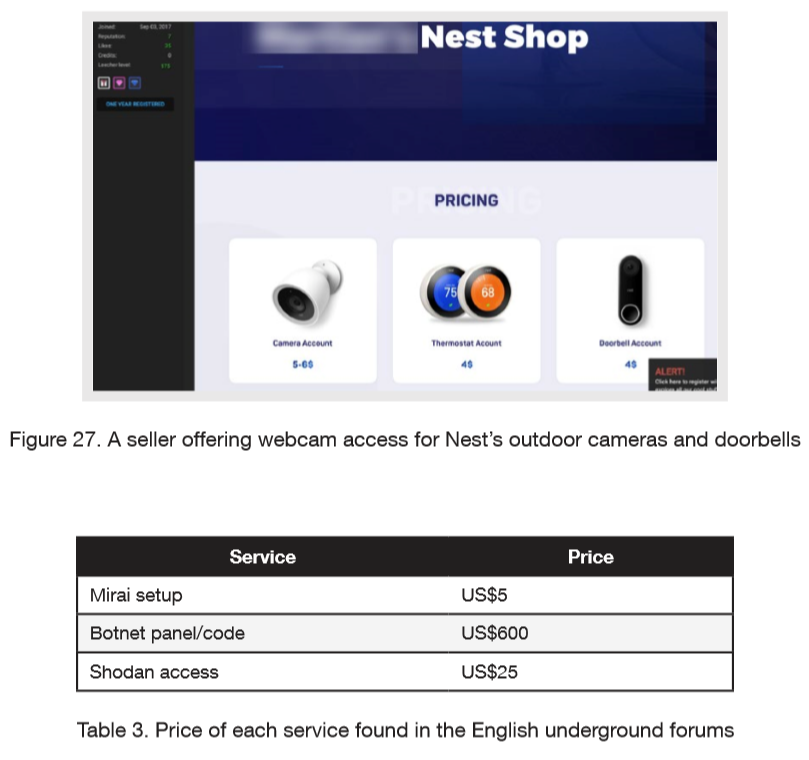
And, of course, cybercriminals are doing more than asking what's for sale. They are also asking for help from each other:
"The most requested hacking methods were for routers, webcams, and printers.
There were also tutorials on the inner workings of commercial gas pumps, including programmable logic controllers (PLCs). PLCs are devices found in factories and other structures with industrial machinery that enable complex equipment to be managed remotely.
Another popular offering is either software for or tutorials on automating searches for specific devices on Shodan, which is a very popular web search engine for finding online devices."
What type of IoT exploits can be used against industry and organizations?
And there are some disturbing developments which could have big implications for organizations:
"Recently, a new Linux ransomware that targets network-attached storage (NAS) systems has surfaced in the forums as well. This may be a big deal for companies which rely on such devices to store corporate data. This also brings forward a new monetization scheme for IoT devices, but since this is a new development, we cannot know how effective it is and, therefore, whether it will establish a new trend for IoT attackers."
However, the report points out that a lot of new Linux-based equipment (well beyond routers) is hitting the market, which will increase the ability for Mirai botnet operators to automatically infect all kinds of equipment.
Trend Micro researchers also came across exploits for some types of industrial robots and downloadable SCADA software.
And they say the things happening in the underground on IoT hacker forums now point to what is ahead:
"We predict an evolution of IoT attacks within the next 12 to 18 months, including rapidly maturing business models.
PLCs and the HMIs used to control PLCs are increasingly being found online. Behind these are smart factories or other heavy equipment or machinery. These devices will be attacked more often, to the point where their current policy of 'availability first, then security second' will need to shift to a more secure setup.
The likeliest business plan to monetize an attack against these devices would probably involve extortion. In this kind of attack, the business model comes from threatening the device's owner with downtime. This way, the criminal can make money out of the attack without the need to understand how the device functions."
And where the money flows, attacks will go.
There is much greater detail available in the Trend Micro research. It really paints a picture of what is happening in hacker forums when it comes to the IoT.
Research report: The Internet of Things in the Cybercrime Underground