It is a challenge many in cybersecurity are facing right now.
When your organization is moving to the cloud, how do you adapt on-prem security models to maintain security in a virtual environment?
This includes the need to have consistent endpoint security in the cloud since endpoint devices are often a user's interface to sensitive data.
Let's take a look at this IT security challenge, based on an AWS endpoint security webinar we recently attended.
Endpoint security in the cloud: how do you approach it?
During the webcast, there was an initial level set of what's needed to make this change:
"Endpoint security is critical to cloud migration because endpoints must be transferred, provisioned, or migrated from a physical to cloud model," said SANS analyst Thomas Banasik, who helped lead the webcast.
David Aiken, Solutions Architect Manager at AWS, also presented on the webcast. Aiken unpacked the framework for integrated endpoint security in the cloud.
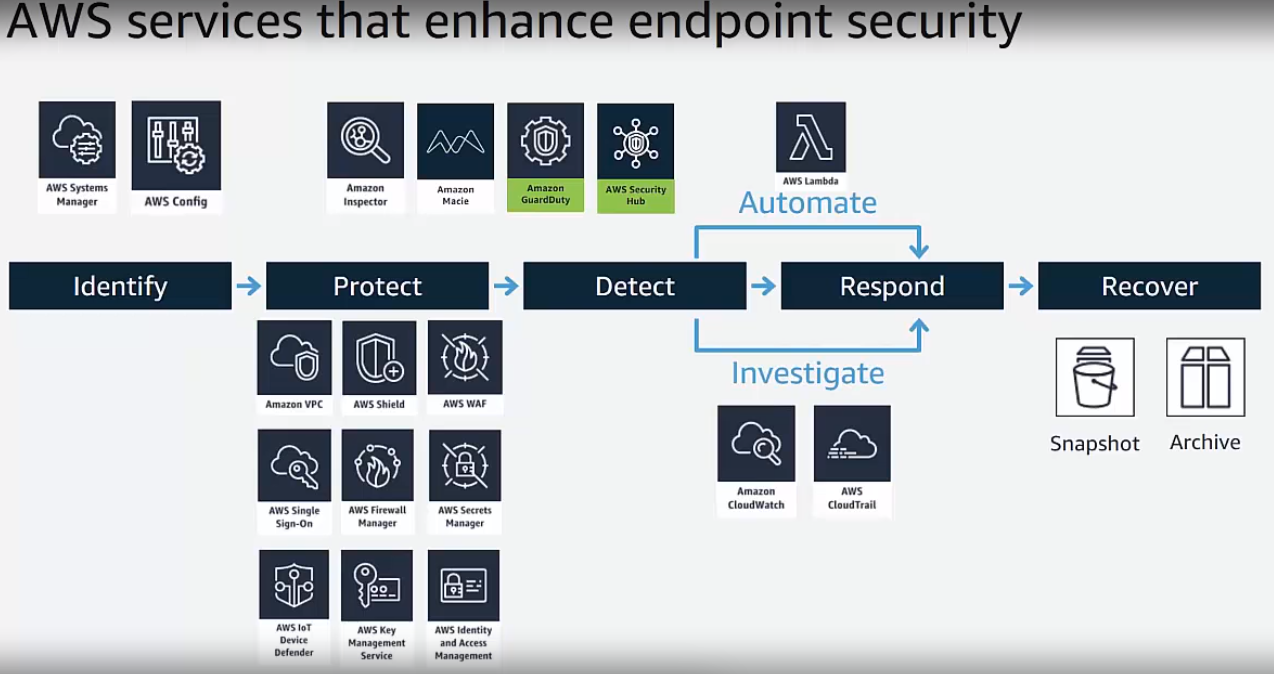
Do you see the two icons in green? Those are two features Aiken identified as security starting points. The services are called AWS GuardDuty and AWS Security Hub.
"The first thing you want to do is go enable GuardDuty in your accounts. There are a couple of clicks to turn it on; there are no advanced configurations needed. It will take you a good 30 seconds to do this, and then you'll start collecting data and reveal insights from that."
What does EDR look like in the cloud?
The presenters also broke out specific elements of endpoint security that become possible in the cloud and which they call superior to an on-prem environment.
"When you put an EDR suite on, it allows you to provide continuous threat monitoring to detect IOCs in that attacker's chain. And it gives your responders the ability to backtrack and do root cause analysis instead of playing a guessing game."
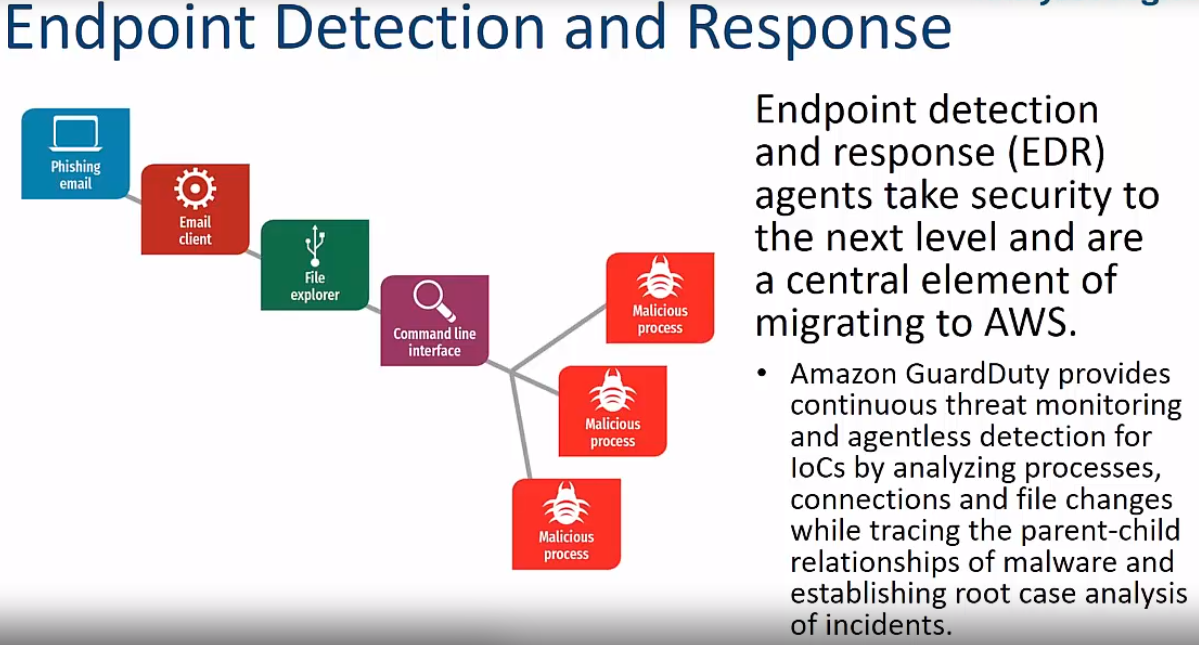
Will any endpoint solution provider work in the cloud?
Banasik had a word of caution about carefully choosing an endpoint solution that will work in the AWS cloud. Some solutions are built for it, others are not:
"If you go for the first solution that is well-marketed and seems like it is low cost upfront, if it doesn't integrate, it's going to be very hard when you are building that cloud security model."
The presenters pointed out that the AWS marketplace has dozens of vendors offering natively-supported endpoint solutions.
The webcast also touches on how AWS customers are leveraging Trend Micro and CrowdStrike (for example) in the cloud.
The webinar covered the following endpoint security topics:
- How to evaluate security, migration, scale, speed, and complexity requirements
- How to implement key endpoint security capabilities in the cloud, including integrated machine learning, EDR, UBA, and DLP solutions
- How to deploy endpoint security agents and use a single pane of glass platform to increase visibility in the cloud
- How to employ agentless monitoring for synchronized threat intelligence
Here is a list of related resources that will ensure your organization's endpoint security strategy and implementation in AWS:
• AWS Endpoint Security webinar which we attended
• AWS Endpoint Security whitepaper
• Endpoint JumpStart webinar




