"After three warnings, we will shut down their incoming and outgoing email," says Mitchell Sprinsky.
The Chief Information Officer at Spectrum Pharmaceuticals believes in tough consequences for end-users who continue bad security behavior.
"First is a discussion with their manager. If there are persistent problems, the employee is referred to HR for an improvement program. If there is no improvement, then there is possible termination, but we've never gotten to that point."
He says this method, along with awareness training and phishing exercises have greatly increased employee vigilance.
But Alan Levine, former CISO of both Alcoa and Arconic, sees things much differently. "Counseling may be necessary, but not counseling that involves HR. If you transfer that responsibility to the HR department, you have become an enemy of the people," he says.
Levine, who is now a consultant for Wombat Security Technologies, says the infosec team should make time for a personal visit or a remote visit for repeat offenders, where specific best practices can be discussed.
These points of view are just the start on the human factor, awareness and phishing.
"People have strong opinions on this, on both sides of the fence," says Sam Masiello, Chief Information Security Officer at
Do you punish employees for risky cyber behavior?
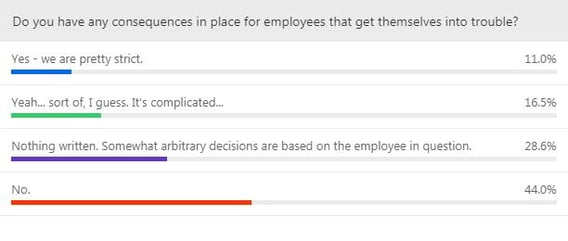
Masiello did a poll of the several hundred cybersecurity practitioners who were live attendees on the web conference. He asked if their organizations have consequences for risky cyber behavior where employees get themselves into trouble.
Interestingly, only 11% report being strict while another 16.5% 'sort of' have consequences. Clearly, many businesses have not developed specific polices on this issue.
 Wombat also shared its most recent survey results to a specific question: If you conduct simulated phishing attacks and have users who continually click, do you have consequences in place?
Wombat also shared its most recent survey results to a specific question: If you conduct simulated phishing attacks and have users who continually click, do you have consequences in place?
Check out these results:

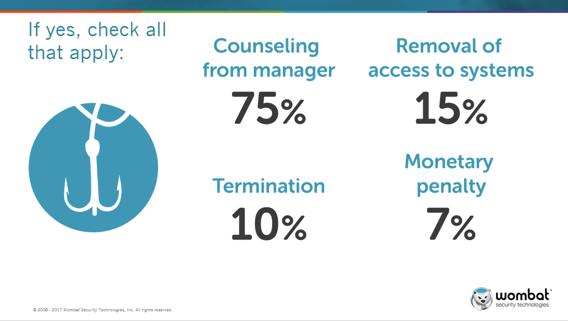
It would be interesting to see which of these consequences have the biggest impact on those who do not alter their digital behavior to protect the enterprise.
Mike Muscatel, Information Security Manager at Snyder's-Lance, Inc., calls security awareness training a shared responsibility. He really believes in making things personal and relatable to employees everyday lives to gain their attention.
"At the end of the
Does security awarenss make business safer?
Alan Levine puts it this way: "When I was CISO at Alcoa, we were attacked. It was significant. And we did not have any cybersecurity awareness in place. When we did the analysis, user awareness was the root of what happened."
The panelists and moderators of this web conference also shared details of what they do around awareness and how often they do each of the components in their program.
And they talked about how to handle executives or sales people that bring in a lot of business. Should they be treated differently if they repeatedly exhibit bad security patterns?




