The data is in, and ransomware is on the rise in a major way.
According to research by Beazley Insurance Company, ransomware attacks more than doubled in 2019.
The attacks against Beazley's clients rose 131% in 2019 compared to 2018. But how are the details of these attacks changing?
And perhaps more importantly now, how will they continue to change given the global state of COVID-19?
How ransomware attacker profiles are changing
In the past, most ransomware criminals have operated in a very particular way.
In countries where extradition by U.S. authorities is not possible, these bad actors operate like businesses.
For these "companies," according to Beazley, "success is based on ensuring their attack victim 'customers' who pay the ransom know they will receive their data back quickly and fully."
At least with these attacks, we can have more reliable expectations. If you pay, you will likely receive working decryption keys.
But these ransomware attackers are not the major group on the rise.
"Increasing in numbers at the other end of the spectrum are criminals who purchase ransomware kits on the dark web, launch attacks in the hope of getting some level of payment and care little about the data restoration experience of their victims."
Think of these ransomware operators as being like unscrupulous contractors who are eager to start on a project at your house. Yes, they promise to do the work and do it well. But when you pay them, they disappear even though the project remains unfinished or poorly done.
Pay these hackers and you may be out of luck—and Bitcoin.
Challenges with ransomware and COVID-19
And Beazley identified another shift in the ransomware landscape because of the coronavirus.
It is changing everything about the world right now, and employment is one of those many things. The remote workforce is larger than ever.
And this also increases the risk of ransomware. Why? A significant reason is the Remote Desktop Protocol (RDP). The insurer says ransomware perpetrators know there is opportunity here:
"RDP is a very powerful tool that provides a lot of convenience to its users. It is also extremely easy to enable. If the computer you want to access is on the public internet, you gain immediate access to your work computer from home or your company's primary file server while you are on vacation with the press of a button."
This is great for people trying to work from home. Unfortunately, a host of security challenges come with this convenience:
- RDP runs on a standard port (tcp/3389) and is easily identified while scanning.
- Companies have very poor password policies, giving a brute force attack a high probability of success.
- More than 20 vulnerabilities have been identified within RDP, many of which allow unauthenticated access to the target computer.
- Companies tend to have very poor patching policies. So, not only is it easy to turn on, it is also very easy to discover and break into.
And it appears that hackers implementing DoppelPaymer ransomware are already sending coronavirus related phishing messages to end-users around the globe.
These attacks typically arrive through a phishing email with a Word document and a password, like in this example below.
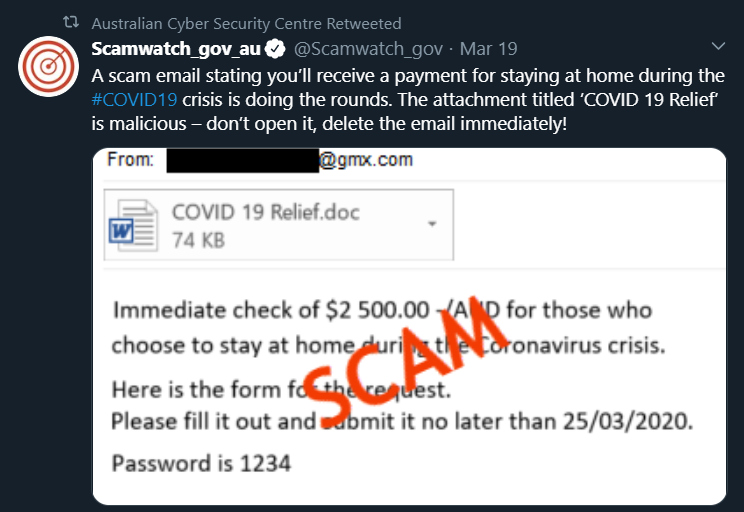
Once the user clicks on the file and enters the password to open it, ransomware can start spreading across the network.
This type of phishing and ransomware attack employs some of the social engineering emotions hackers love to use. In this case, urgency and the fear of missing out.
What's next in ransomware?
At this point in 2020, almost everything is an unknown.
We don't yet know how many people are carrying COVID-19, and how many are not. Some of us don't know when our states and cities will allow us to go outside, travel, or show physical affection for our loved ones.
Many of us don't know when we will return to school or work, and still others don't know if there will be work to return to.
What we do know is that ransomware is such a great opportunity for hackers that it will continue:
"Ransomware attacks in their current form are far too successful and profitable for cyber criminals to shift course. Ransomware perpetrators will continue to evolve their tactics as companies implement new defenses. We have already started to see attackers pairing ransomware encryption with data theft. Instead of encrypting data and asking for an immediate ransom, cyber criminals such as the Maze attack group are now starting to name and shame organizations."
In a world that has rapidly moved online by necessity, we must diligently look after our digital health just as seriously as we take our physical health.
[SecureWorld Remote Sessions briefing: "Ransomware and Digital Extortion: Legal Issues and Practical Responses"]





