We're going on a journey to the Dark Web with security researchers from Trend Micro.
And in this case, they are showing us where the money is flowing.
Specifically, the money for exploits and hacking opportunities against Internet of Things devices and networks.
IoT cyberattacks: exploits for sale
There has been a lot of talk about IoT attacks and what is possible.
But in this recent research, the Trend Micro team tracked how cybercriminals are making money off of IoT attacks and vulnerabilities. Because we know that the ability to monetize attacks increases how prevalent they are.
IoT vulnerabilities: 5 top forums searched
The research team looked at some top IoT hacker forums in five languages to get a good cross-section. The forums operate in Russian, Portuguese, English, Arabic, and Spanish.
They came away with three top findings.
#1: The Russian language underground is the most mature and the best at monetizing IoT attacks.
#2: Most monetization occurs through crime-as-a-service to launch DDoS attacks and through the selling of botnets consisting of compromised IoT devices.
Take this ad, for example:
"We buy vulnerabilities discovered by you in routers and IoT devices. Consider any offers (for payment) but the final amount will depend on the number of available devices... preference will be given to RCE, and other vulnerabilities that allow executing code on the device."
And here is another example:
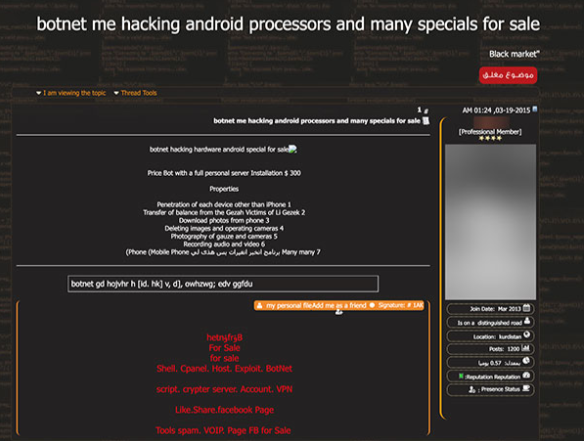
The researchers also found a new Android-based cryptominer for sale which was launching "after a successful beta period," according to its developer.
And they discovered compromised VPN proxies for sale, to help cybercriminals remain anonymous; Linux ransomware that targets network-attached storage (NAS) systems; and even exploits for some industrial robots.
#3. Mirai and its variants will continue to be the most used malware for IoT attacks—by far.
Researchers discovered updated versions with more functionality and tutorials and training on how to use it. Plus, tutorials on how to commit all kinds of IoT exploits.
This is one of many examples:
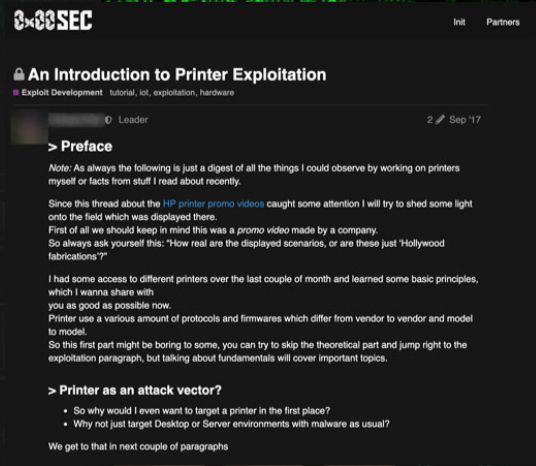
This is just the start of Trend Micro's journey to the IoT criminal underground. Follow the money and the developments and read the research paper, The Internet of Things in the Cybercrime Underground.
It is both well done and informative about the trends in this space.



