When it comes to targeted phishing attacks, who are the Very Attacked Persons within your organization?
It has to be the CEO—or the CFO, right?
Maybe not.
Our team just watched an insightful SecureWorld web conference on how to Identify and Protect Your Very Attacked Persons (VAPs). Eric Schwake, Product Manager at Proofpoint, shared one of the Very Attacked Persons phishing reports he can run for clients.
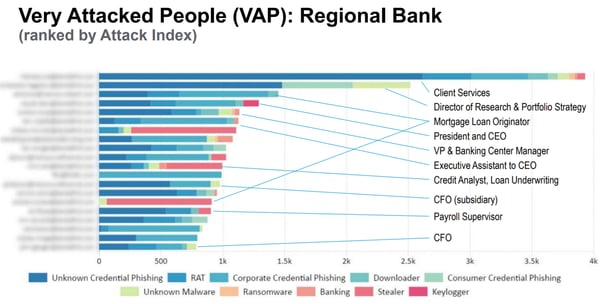
Take a look at these actual phishing attacks against people in roles at a regional bank:
In the case of this bank check out who are the top 3 most phished roles:
- Client Services
- Director of Research and Portfolio Strategy
- Mortgage Loan Originator
The President & CEO came in fourth and the bank's CFO was way down the list.
Surprised?
Schwake explains the results:
"The idea is, if I can get the client services credentials, I can steal that person's credentials, I then become that trusted user. I'm now essentially the client services person and I can start sending attacks laterally within that organization and many users won't think twice about seeing that email. It's not even a spoofed email address at that point, it's the exact email address of the user."
And Proofpoint, in its 2019 State of the Phish Report, found that corporate credential phishing jumped 300% between Q2 2018 and Q3 2018.
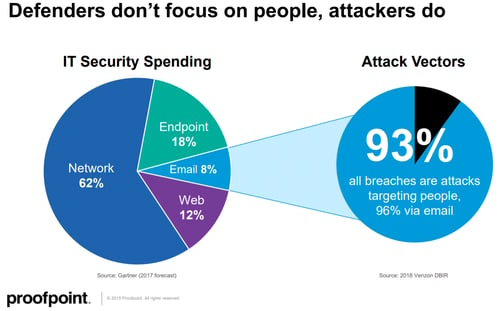
"When you look at the attackers and how they're going to go after your organization, the attacks are going to be generally email based. 90%+ of all attacks we see are going to come in from the email vector."
However, there remains a disconnect or mismatch in the way most organizations focus their cybersecurity resources.
Jeremy Rucker, Cybersecurity Attorney at Spencer Fane, agrees there should be a shift in how we think of and prioritize threats.
"We should focus our data security programs on guarding against threats from leaving the door unlocked as much as or maybe even more so than the threat of the door being kicked in."
Rucker also helped lead the web conference on Very Attack Persons.
And he says those targeted in phishing attacks can be anyone hackers identify as a point of entry.
"I always say, they'll use the janitor, if needed, to carry out the attack."
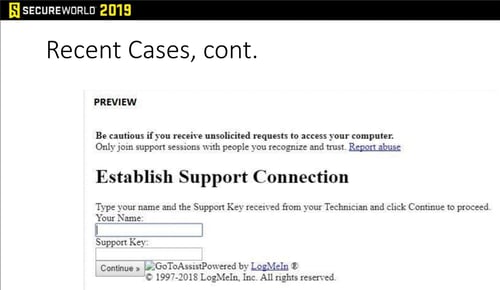
He shared recent examples his firm's clients have faced, including spoofed services that warn users to be cautious—kind of a reverse psychology approach:
We've only hit a few highlights here. For much more, watch the web conference, on demand, on how to Identify and Protect Your Very Attacked Persons.