Have you noticed a fall chill in the air?
More importantly, have you detected
New advisory issued on FALLCHILL
The Department of Homeland Security and the FBI issued a joint Technical Alert with
RAT functionality of FALLCHILL
- retrieve information about all installed disks, including the disk type and the amount of free space on the disk;
- create, start, and terminate a new process and its primary thread;
- search, read, write, move, and execute files;
- get and modify file or directory timestamps;
- change the current directory for a
process or file; and - delete malware and artifacts associated with the malware from the infected system.
- Here is the communication flow-and as a reminder-"HIDDEN COBRA" is the U.S. codeword for North Korean cyber operators:
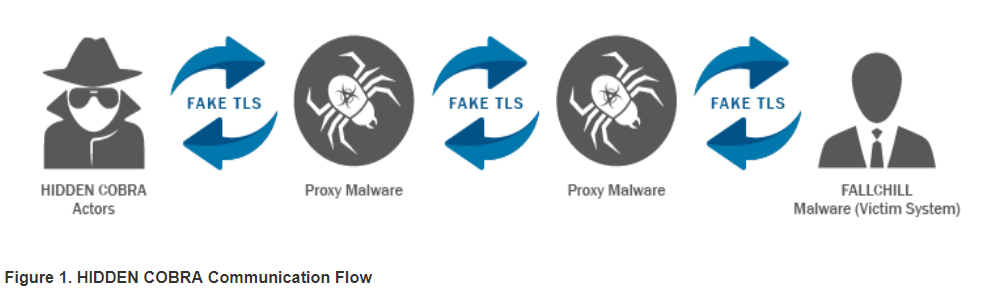
How FALLCHILL RAT infects your system
"
This latest RAT should not surprise anyone, because North Korea is one of the top three cyber threats to the United States, according to Major General Brett Williams.
Williams used to be Director of Operations at U.S. Cyber Command, and we interviewed him at SecureWorld Detroit:




