If you leave your laptop on the front seat of your car while you run into the store, you are begging for it to be stolen.
In this day and age, that's stupid.
If you leave the Internet of Things (IoT) devices you make purposely exposed on the internet, you are begging for them to be hacked.
In this day and age, that's brilliant.
Panasonic develops IoT honeypot
Panasonic makes all kinds of connected devices, including cameras, refrigerators, washers, driers, and smart TVs.
And before it ships these devices to your home or office, it wants them to get hacked so it can close the holes the hackers used.
Panasonic developed an IoT honeypot, which is designed to attract hackers and help security engineers see how the devices are being attacked.
The smart IoT devices sit open and exposed on the internet. Hackers and their automated tools cannot resist.
Results of Panasonic IoT honeypot attacks
Panasonic engineers presented recently at the Blackhat Europe conference and revealed astounding results of their IoT honeypot.
"Since its deployment, Panasonic has been able to find 179 million attack cases and 25 thousand malware samples, of which 4,800 were unique samples targeting IoT. 20% of the samples were new and hashes for them did not exist when querying Virustotal. In addition, we discovered 0-day attacks against the SMB protocol, allowing attackers to access data on compromised home appliances."
And this is more than just watching the attacks fly. The company has a feedback loop that increases the security of any Panasonic devices you buy.
"We have developed a system where information being collected through the honeypot is sent to a Sandbox for automated analysis, to address our concern for having a limited number of security experts. What this system allows Panasonic to do is collect 'malware targeting/exploiting Panasonic IoT devices' for quicker remediation, in addition to 'popular malware' targeting a wide-range of IoT devices."
Here is a visual representation of the Panasonic honeypot program:
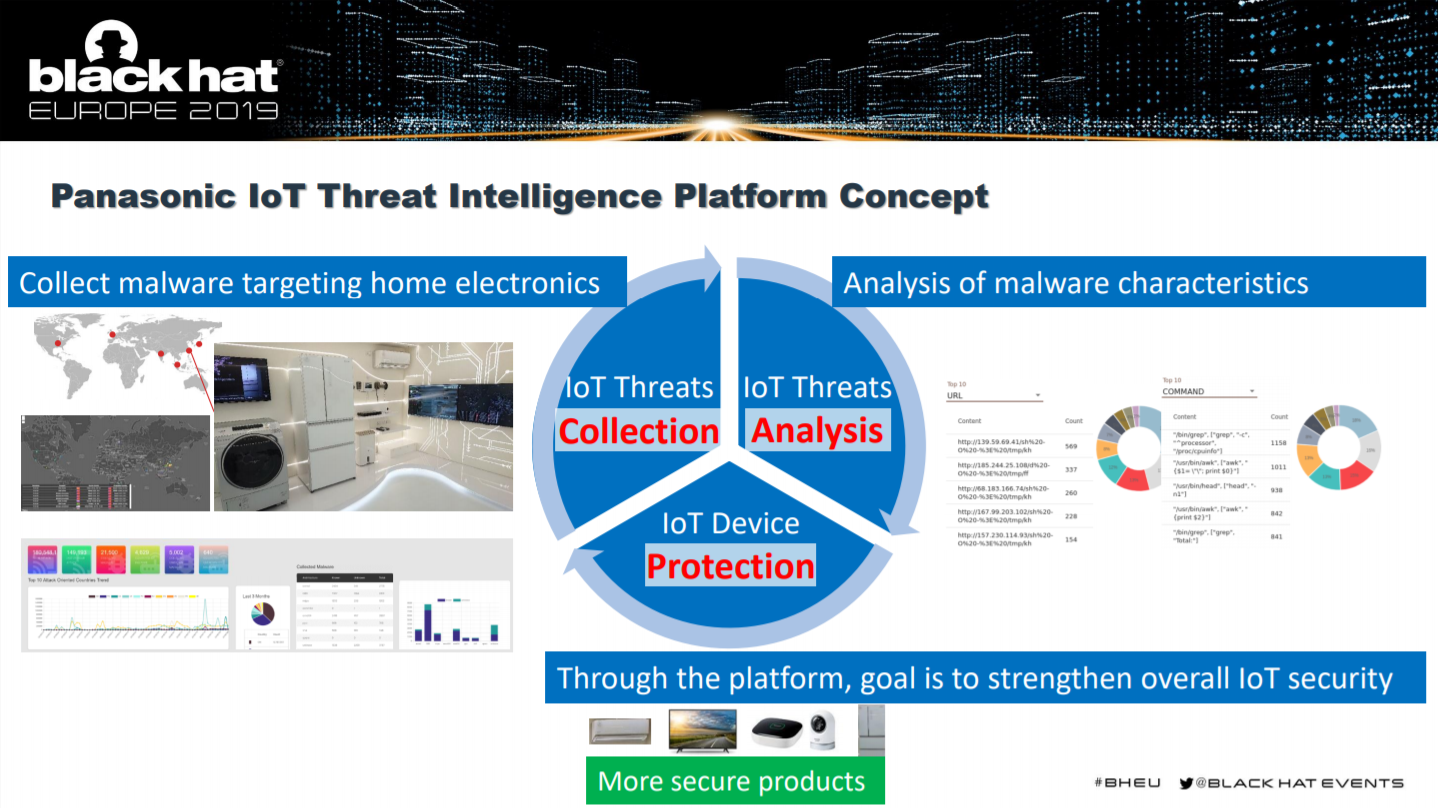 Honeypot discovers IoT cyberattacks are surging
Honeypot discovers IoT cyberattacks are surging
Here's something else that is helpful for cybersecurity teams to know.
Panasonic engineers say they are tracking a huge surge in attacks against the IoT devices in their honeypot setup. That surge of IoT attacks is coming from hackers in the United States and China.
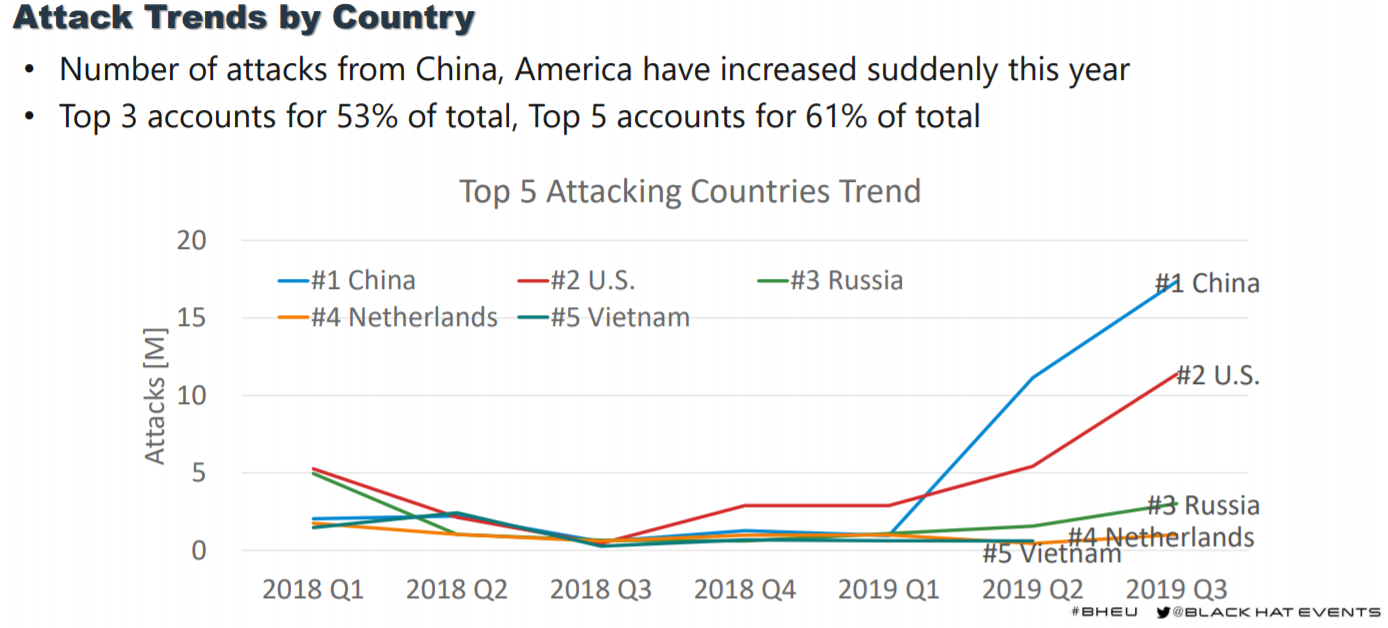
Internet of Things attacks are also increasing from Russia, but the size of the increase is smaller.
What hacker forums tell us about IoT attacks
Trend Micro researchers recently investigated five top Dark Web forums that are focused on IoT security vulnerabilities. Here is the type of advertisements they came across, as hackers explore ways to make money from IoT attacks:
"We buy vulnerabilities discovered by you in routers and IoT devices. Consider any offers (for payment) but the final amount will depend on the number of available devices... preference will be given to RCE, and other vulnerabilities that allow executing code on the device."
The researchers also found a new Android-based cryptominer for sale which was launching "after a successful beta period," according to its developer.
And they discovered compromised VPN proxies for sale, to help cybercriminals remain anonymous; Linux ransomware that targets network-attached storage (NAS) systems; and even exploits for some industrial robots.
The ways hackers are trying to attack IoT and Industrial Internet of Things (IIoT) devices continues to grow.
Now Panasonic's honeypot and sandbox setup uses that growth to make its connected devices more secure.
In this day and age, that's brilliant.




