Organizations around the world have been on the same quest.
They've been searching. Many have been testing. And some have been guessing.
When it comes to passwords, where is the holy grail that will miraculously maximize security and usability at the same time?
A team of researchers at Carnegie Mellon University claim they have found it after nearly a decade of hunting. Now, they are sharing their scientific evidence and practical guidance.
Password best practices: 10 years of research
The researchers start their new paper on passwords by explaining that everyone on the secure and usable password quest has lacked "empirically evaluated and definitive guidance" on password usage and policies—until now.
"Our results, derived through two successive experiments that
investigated a wide range of potential interactions between requirements, allow us to provide concrete, practical recommendations for how to combine and configure these mechanisms."
They examined combinations of length, character-class, blocklist, and password meter type requirements, along with minimum strength requirements.
And during the decade of research, it wasn't just passwords that changed; it was the people, too.
"We find that how users pick passwords has changed over time, and that this, in combination with advances in password guessing, implies that requiring passwords to have multiple character classes brings at best minor benefit to password strength."
Before we get to the findings, let's briefly look at how this unique research worked.
Password security and usability: Carnegie Mellon research
For each experiment, the Carnegie Mellon researchers ran a user study where participants were tasked with creating and then recalling a password under a randomly assigned password policy.
"In Part 1, participants were asked to role play, imagining that they
needed to create a new password because their main email account
provider had been breached. We emailed participants two days
later asking them to participate in Part 2, in which they were asked
to recall their password."
Researchers tracked keystrokes, analyzing those recalling their passwords only from memory, and documented the number of people who actually dropped out of the experiment after failing to recall their password under each type of password policy.
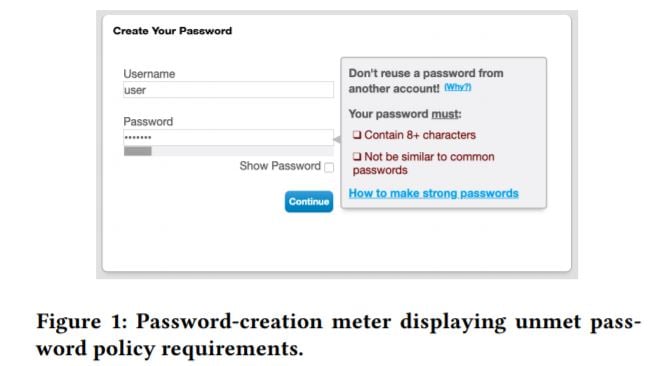
They then compiled tables of data like the one below, which break down how long passwords took to create, how often a password was rejected by the policy assigned to its creation, and the "guessability" factor of the password that met the set requirements. This is for those of you who like to get technical (click to expand):
Now, let's move on to what works with passwords and what doesn't. We're getting closer on our continuing password policy quest.
Password policy research: the findings and details
Let's break down the results by category: character-class requirements, blocklists, and minimum strength policies. What impact do each of these individually and/or collectively have on password strength and usability?
Character-class requirements
The research team disproved the idea that requiring more Ch@r@ct3r classes in a password is a security silver bullet. On the usability front:
"Although prior work has repeatedly found that requiring more character classes decreases guessability, researchers have shown
that character-class requirements lead to frustration and difficulty
for users.
Since other requirements, e.g., minimum-length or blocklist requirements, can strengthen passwords with less negative impact on usability research has advocated retiring character-class requirements [7, 26]. These recommendations have been standardized in recent NIST password-policy guidance."
[RELATED: NIST's 2019 updated password guidance]
And the team says you can achieve similar levels of security in other ways:
"While our results suggest that, when combined with a minimum-strength requirement, policies that require multiple character classes improve resistance against offline attacks, similar improvement can be achieved with less impact on password-creation usability by increasing the minimum-strength threshold or the minimum required length.
In general, increasing length requirements for a given minimum strength policy strengthened passwords produced under that policy against offline attacks, while maintaining strength against online attacks."
Carnegie Mellon University professor Nicolas Christin sums up the key finding: "We found that a policy requiring both a minimum strength and a minimum length of 12 characters achieved a good balance between security and usability."
Minimum-strength requirements
What kind of minimum-strength requirements were found to be optimal? Researchers say you want to balance this out with the level of security you are trying to achieve at your organization, but clearly, they found a sweet spot of security and usability in this area:
"Our results confirm that minimum-strength requirements can effectively guide users toward stronger passwords without significantly inhibiting password memorability or ease of password creation.
Synthesizing these results, we recommend a password policy
of 1c12+NN10 for security settings that need protection against
offline attacks while still providing reasonable usability. Similar
to blocklists, system administrators using a minimum-strength
requirement should check that the requirement is met at both the
client and at the remote server."
Wait a minute, though. What does that equation mean, in plain english? We reached out to researcher Nicolas Christin. He is giving our SecureWorld readers the translation:
"This is a "password composition policy." It specifies that a password must conform to the following criteria:
- "1c": contains at least one class of characters (this is basically not a requirement, since anything fits in that category -- a class of characters is "upper case," "lower case," "symbols," "digits" -- so this requirement means that - "12": be at least 12 characters long
- "NN10": pass a "cracking test," in which a neural-network based password cracker doesn't guess it within 10^10 tries (that's 10 billion, in plain English)."
Check out the Carnegie Mellon password demo meter for more. If the bar turns green, the password passes the test!
Blocklists
The researchers found evidence that blocklists have limited security benefit and create a lot of end-user frustration. They urge you to take another approach:
"Password policies incorporating blocklist requirements should not
impose character-class requirements.
We also find that minimum strength policies, which we believe our work to be the first to closely investigate in a user study, can improve upon blocklist policies by increasing resilience to offline attacks without degrading usability."
If you and your team want to read the specifics of this password policy research, here it is: Practical Recommendations for Stronger, More Usable Passwords Combining Minimum-strength, Minimum-length, and Blocklist Requirements.
"Now that we are providing concrete guidance on password policies, we're optimistic that companies and organizations may adopt our recommendations," says Joshua Tan, a postdoctoral researcher at Carnegie Mellon's CyLab.
Is your quest finally over? Have we found the holy grail of passwords where security and usability intersect?
You'll have to answer that question yourself.