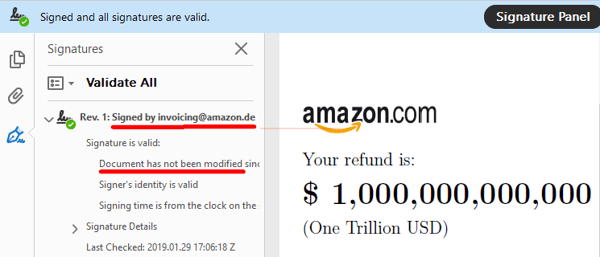
Imagine getting a signed document from Amazon stating that it owes you one trillion dollars—$1,000,000,000,000!
Too good to be true?
Well, here's the exciting news: you have the electronically-signed PDF to prove it. Here it is:
And if you read the areas underlined in red, you can see for yourself, this was signed by Amazon.de (the German division) and the document has not been modified since each party signed it electronically.
The only problem with this whole thing? The document was actually altered in a cyberattack by security researchers in Germany to show how vulnerabilities exist in many PDF electronic signing and verification platforms.
The Network and Data Security Team at Ruhr University Bochum refers to their research as revealing "PDF Insecurity."
3 classes of PDF signature spoofing attacks
"We systematically analyze the verification process of PDF signatures in different desktop applications as well as in server implementations and we introduce 3 novel attack classes.
Each of them gives a blueprint for an attacker to modify a validly signed PDF file in such way that for the targeted viewer, the displayed content is altered without being detected by the viewer’s signature verification code...."
The researchers say each of these three PDF signature attack categories abuses a different part in the signature validation logic.
- The Universal Signature Forgery (USF) manipulates meta information in the signature in such a way that the targeted viewer application opens the PDF file, finds the signature, but is unable to find all necessary data for its validation. Instead of treating the missing information as an error, it shows that the contained signature is valid.
- The Incremental Saving Attack (ISA) abuses a legitimate feature of the PDF specification, which allows
to update a PDF file by appending the changes. We introduce four variants of ISA masking the modification made without raising any warnings that the document was manipulated. - The Signature Wrapping Attack (SWA) targets the signature validation logic by relocating the originally-signed content to a different position within the document and inserting new content at the allocated position.
PDF signature spoofing: a widespread problem
And maybe you're wondering if the successful attacks were carried out on some little known platform that is likely to be less secure than those that are widely used.
Unfortunately, researchers were able to exploit these PDF signature vulnerabilities in 21 of the 22 applications they tested.
Here are the PDF signature viewer applications where researchers found security vulnerabilities.
And here are the online validation services where electronic signature vulnerabilities are reported to exist.
Read the complete PDF attack paper for yourself: 1 Trillion Dollar Refund - How To Spoof PDF Signatures.
And the next time you receive an electronically-signed document, you may want to double-check the numbers are still accurate, just to be safe.
[RESOURCE: Regional cybersecurity conferences 2019 calendar]