The Identity Theft Resource Center® (ITRC) and CyberScout® have released the 2017 Annual Data Breach Year-End Review, a report that examines the confirmed data breaches that affected US organizations and consumers in 2017.* The stark headline numbers—1,579 total breaches and nearly 179 million records exposed—are troubling in their own right. But deeper analysis of these data points tells an even darker tale.
How 2017 measured up
Numbers compiled from 2017 revealed record highs for data breach incidents; confirmed reports were up a dramatic 44.7% over 2016, which itself was a record year. The two years combined account for 2,699 of the 8,190 confirmed breaches identified by the ITRC between January 2005 and late December 2017—which means that more than 30% of recorded incidents have happened in the last two years alone.
It’s also worth mentioning that the concluding months of 2017 were very active on the breach front. At the end of October, a post on the Wombat Security Blog highlighted year-to-date breach totals for the five sectors tracked by the ITRC. Following is a comparison of year-end numbers versus those that were on the books on October 25th. (You’ll note that the Business sector far outpaced the others, topping the ITRC list for the third year in a row. At 55% of the overall total, this sector experienced more breaches than all other sectors combined.)
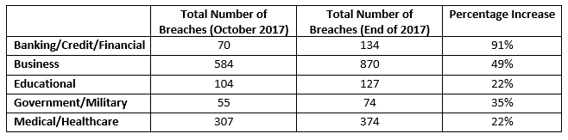
Data sources: 2017 Annual Data Breach Year-End Review and ITRC Data Breach Report dated 10/25/2017
Phishing, ransomware, and the fear of the unknown
The ITRC tracks seven categories related to data loss, a few of which are directly tied to end-user actions:
- Hacking—which includes phishing, ransomware and/or malware, and skimming—was the main source of data loss, accounting for nearly 60% of all breaches, a 3.2% increase from 2016. It was particularly prevalent in the Business sector, with nearly 40% of organizations attributing their breaches to this type of attack.
- Phishing was fingered in 21.4% of all hacking-based attacks and 14% of Business hacks.
- Ransomware and/or malware figured into 12.4% of attacks attributed to hacking. It was identified as the source of 8.4% of hacking breaches in the Business sector.
- More than 145 million compromised records were the result of end-user behaviors (i.e., employee error, negligence, improper data disposal, and loss). These factors were at the root of 10.4% of breaches.
- Accidental web/internet exposure resulted in 6.4% of breaches and more than 8 million compromised records.
It’s clear that poor cyber hygiene among employees is having a significant impact on businesses. As was echoed in Wombat Security’s recently released State of the Phish™ Report, organizations are regularly feeling the impacts from these issues. More than three-quarters of infosec professionals who were surveyed for the study said they experienced phishing attacks in 2017, and the reported impacts from phishing—including malware infections, account compromise, and data loss—were up by more than 80% from 2016.
And here’s an even more sobering reality: the huge numbers revealed by the ITRC aren’t even close to the full picture. There is a lot to fear in the unknown, because there isn’t true transparency into the actual number of records compromised last year in the US (let alone globally).
More than one-third (36.7%) of the breaches confirmed by the ITRC in 2017 failed to identify the number of exposed records. Though this is a move in the right direction from 2016—when more than 50% of notifications had an unidentified number of compromised records—it’s still far from ideal. That’s because visibility into the numbers is just the tip of the iceberg; what’s even more important is knowing the types of data exposed, which is also unclear. As Karen Barney, the ITRC’s Director of Program Support, noted, “Understanding the type of personal information that has been exposed is absolutely critical for affected consumers.”
In the end, the ITRC report is a tale of two opportunities for organizations. First, the opportunity to better educate end users and reduce the number of preventable data breaches. It’s time for organizations to acknowledge not only the role of the user in causing breaches, but also in the capacity of the user to create a much stronger last line of defense against attackers.
Second, organizations have the opportunity to be a better friend to the end user, namely by recognizing that employees are also consumers. Organizations should be more respectful of the public’s right to know when personal data has been exposed, and how they might be impacted by that exposure.
The full 2018 State of the Phish Report is available on the Wombat Security website. For additional insights from industry experts, register for the January 31st SecureWorld web conference, State of the Phish Report 2018: What Your Peers Are Doing to Reduce Successful Phishing Attacks. You can join live or on-demand, and CPE credits are available.
* According to the ITRC: “A breach is defined as an event in which an individual’s name plus Social Security Number (SSN), driver’s license number, medical record, or a financial record/credit/debit card is potentially put at risk—either in electronic or paper format. For data breach incidents involving only emails, user names, and/or passwords, the number of records are not included in the overall total number of records.”





