Qakbot is still quacking-and still infecting.
And this time, the malware bot is increasingly going after business from SMBs to the Enterprise.
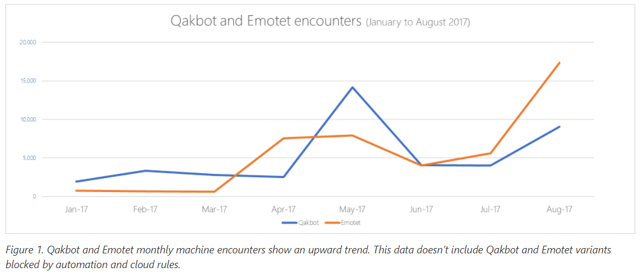
Check out this chart of Qakbot encounters (blue) and Emotet encounters (orange) detected by Microsoft researchers from January to August.
And as the description says, this does not include variants that are blocked by automation and cloud rules.
Says Microsoft, "Recent variants of these malware families have spreading capabilities, which can increase the chances of multiple infections in corporate networks. They can also be spread by other malware during the lateral movement stage of a
This chart backs that up:
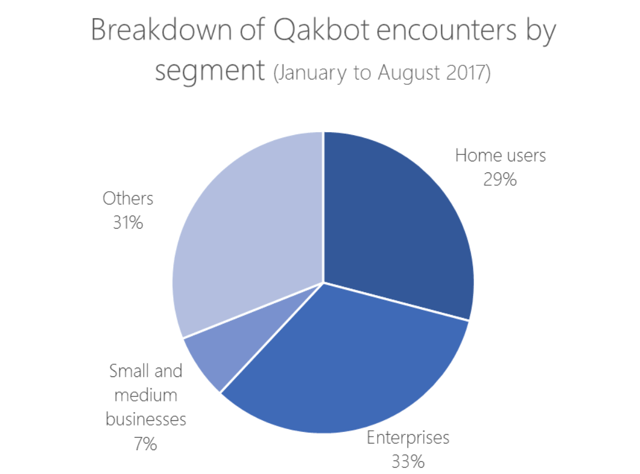
Qakbot and Emotet becoming more sophisticated
And just like human viruses that get tougher to fight over time, researchers say bad actors have also made Qakbot and Emotet tougher to eradicate.
"Over the years, the cybercriminals behind Qakbot and Emotet have improved the code behind their malware. They have evolved to evade detection, stay under the radar longer, and increase the chances of spreading to other potential victims," the researchers say.
The malware Trojans try and steal a user's information through keylogging, stealing cookies, stealing certificates and by hooking browser or network related APIs.
Qakbot and Emotet mitigation
Microsoft spells out commonalities and mitigation techniques in their update.
You might want to save the techniques in case Qakbot quacks your way.