If your organization gets hit with ransomware, does it ever make sense to pay?
This was a point of debate in the SecureWorld web conference, "Ransomware: The Not So Good, the Really Bad, and the Truly Ugly," which is available on-demand for CPE credit.
Ransomware web conference training, section 1:
Jon Neiditz says in some cases it can make sense to pay. He co-leads Cybersecurity, Privacy & Data Governance for Kilpatrick Townsend & Stockton LLP.
"If you weren't prepared for the ransomware, and you didn't do what you were supposed to do to protect yourself in case of ransomware, then you are more likely to end up paying."
Maybe you don't have backups (or they become corrupted), or perhaps you can't stop the ransomware's propagation across your network. Those are examples he gave of where you may find that it is worth it to pay the ransom.
He then walked web conference attendees through nearly a dozen things organizations can do to prepare and minimize the risk of ransomware.
He also says that you need to engage legal counsel immediately as part of your incident response plan. The days of taking a wait and see approach on involving legal are behind us because there is too much at stake.
Ransomware web conference training, section 2:
Matthew Rosenquist is a Cybersecurity Strategist in the AI Group at Intel Corporation. He says you should never pay hackers in a ransomware case.
"Because if you pay, you likely end up on a gold list that cybercriminals trade or sell to each other of those that will pay."
He calls it the Greed Principle: "If I can steal $10 from you today, then I'll try to steal $20 from you tomorrow."
He shared about strategies
He refers to these developments as resistance factors:
• Smarter people
• Hardened technology
• Better security tools
• Greater industry cooperation

This does not mean, however, that ransomware will simply ride off into the sunset. As long as it's profitable, Rosenquist says, hackers will find a way to make money.
Ransomware web conference training, section 3
Erich Kron is a well-known Security Awareness Advocate with KnowBe4 Security. He took web conference attendees into some of the ransomware trends, including a big reason phishing still proves to be the preferred delivery method for this attack.
He says nearly 55% of users who click on a phishing link do so in under 60 minutes. That's a rapid response time.
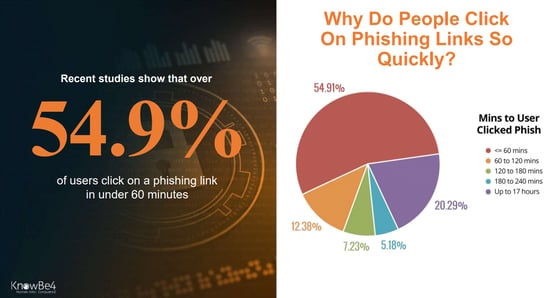
Why does this happen?
"The bad guys know how to get people to do it. They know how to entice people with emotions; they are getting very, very good at doing this—getting people to act before they can think," Kron says.
And he points out that the ransomware threat has gone beyond laptops and PCs and is increasingly hitting endpoints.
- In 2016 alone, more than 153,000 users were hit by mobile ransomware.
Kron then walked listeners through specific things they can do to operate a robust and effective security awareness program, and how that integrates into your organization's overall cybersecurity strategy.
This is only a summary of what was covered.
So check out the complimentary web conference on-demand and arm yourself with expert insights, while you earn CPE credits: "Ransomware: The Not So Good, the Really Bad, and the Truly Ugly."




