How do I change my end-users' behavior? That's the question thousands of security awareness practitioners ask themselves each year about building a successful program. There are so many factors to consider, from timing to appropriate topics to incentivizing users.
Let's take a peek at some highlights from this year's 2021 State of the Phish report to help you successfully build an impactful security awareness program.
Timing: annual training is dying, and that's a good thing
What is the longest amount of time users can go without security education without it impacting their knowledge and skills? Four months, according to a German study of phishing awareness and education over time. After six months, those skills are gone.
Keep in mind that different phish require different skills. An impostor email that appears to be from a supplier is not the same as understanding a malicious URL or attachment. What may be obvious to InfoSec professionals is definitely not to most users (more about that in the report), so these skills have to be taught and reinforced continuously.
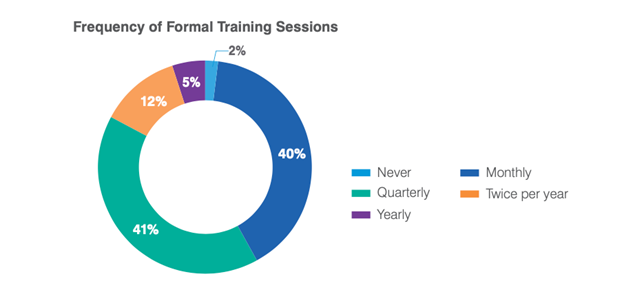 Data showing the frequency of formal training sessions in the 2021 State of the Phish report
Data showing the frequency of formal training sessions in the 2021 State of the Phish report
That's why in the 2021 State of the Phish, annual training is on the outs with security professionals we surveyed. Only 5% of organizations we surveyed in seven countries are doing annual training. This is a great trend, demonstrating more organizations are ensuring the retention of these critical skills through more frequent security awareness programs.
Topics: phishing dominates, but there's more nuance to it
If you have the approval to keep your program running frequently, what should be taught? Who should be learning? Let's start by what our surveyed professionals educate their users on: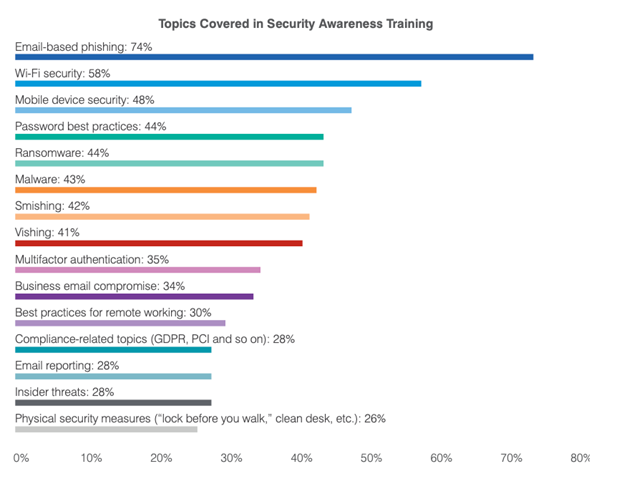 Email-based phishing was the #1 topic taught in security awareness programs according to the 2021 State of the Phish
Email-based phishing was the #1 topic taught in security awareness programs according to the 2021 State of the Phish
Email-based phishing was the most common topic, which isn't a surprise due to the pervasiveness of these types of attacks. Wi-Fi security was #2, which might be explained by the shift to working from home for many employees in 2020.
You can see other topics in the list—such as malware, ransomware, business email compromise, and email reporting—are all related to phishing. Having a better understanding of users being impacted by these threat types will help you deliver to the right people.
Because this area is so critical, we recommend using real data about users being targeted by and engaging with real attacks to help guide your program. While sending out phishing simulations and knowledge assessments to understand user strengths and weaknesses is great, it still means you’re missing out on true user risk and behavior that should be addressed to make the biggest impact.
Consequence models: should you have one for your program?
We hear questions about consequence models all the time from customers. Should repeat offenders have consequences? Should the consequences include loss of bonuses or even termination?
Every organization is different and therefore some may adopt a consequence model while others don’t. What we have seen is that organizations that reward users (with recognition, and sometimes gifts) and focus their programs on the positive get better participation from users and are able to more impactfully drive the right behavior to reduce incidents and risk.
If you should pursue a consequence model, and you believe it to be beneficial for your organization, here’s what organizations are doing and had to say about them.
- 55% of organizations punish users who regularly fall for phishing attacks (real, simulated, or both)
- 82% of those using a consequence model said it has improved employee awareness
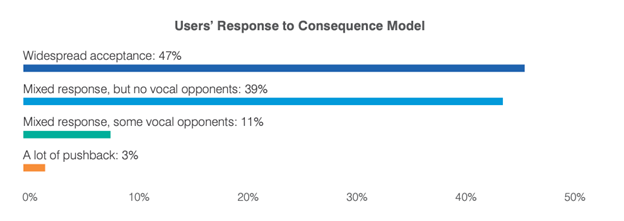 Users' Response to Consequence Model based on a seven-country survey of 600 InfoSec professionals
Users' Response to Consequence Model based on a seven-country survey of 600 InfoSec professionals
Additionally, here's how users responded to consequence models. Surprisingly, only 3% of organizations had a lot of pushback, and 11% of organizations had a mixed response with vocal opponents. There's more interesting findings related to consequence models in the full report.
Take action: make 2021 the year of behavior change
It is more important than ever, with users working from home and many transitioning to hybrid or fully remote home models, to educate your users so they know how to protect themselves. One of the last sections in the 2021 State of the Phish is dedicated to taking action, and we always hear from customers that use this report to help build an effective program each year. We hope you can do the same and ensure your users are resilient in the coming year.





