Here is a perfect example of how a cyber attack (phishing) can start with a social media post.
This case happened in the UK, but it could have happened anywhere.
Mike Tinmouth was trying to open a business account with Barclays Bank and felt like customer service was sending him in circles. So he did what a lot of people do these days: complain out loud on Twitter, tagging the company's customer service account. Here is his tweet:
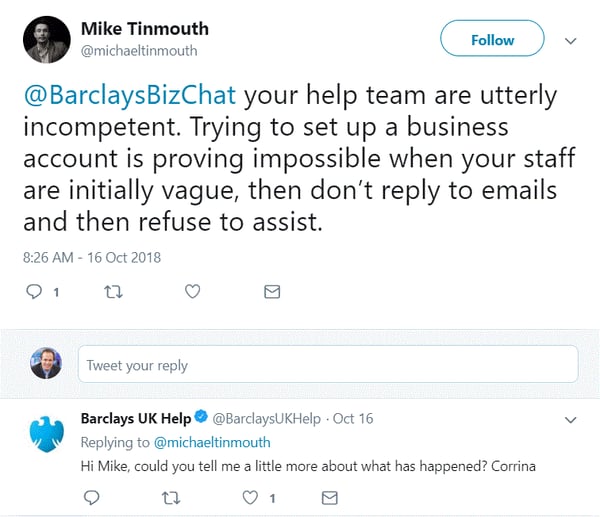
Soon after this Twitter exchange, he received an email that appeared to come from the bank—but it was from a cybercriminal who had seen his tweet. He was being phished and socially engineered. Check out the detail in this phishing email, which was really from the criminal:
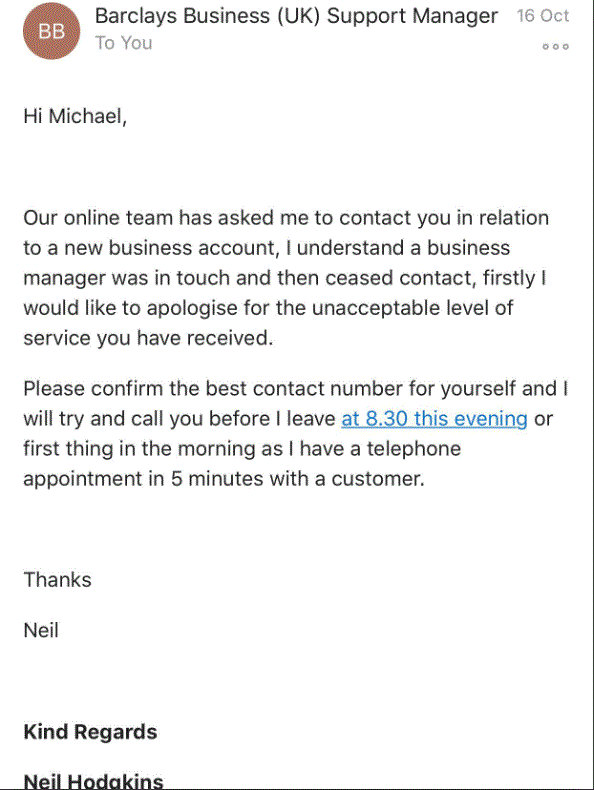
Tinmouth replied with his phone number, spoke with the helpful cybercriminal named Neil (who was posing as a customer service agent), and eventually started to transfer the £8,000 he thought was headed for his new Barclays account.
Fortunately, the transfer was blocked. That, however, is not the end of the story.
Now, Tinmouth is tweeting about something else: Barclays' apparent unwillingness to investigate the attempted cybercriminal, even though the suspect is allegedly one of the bank's own customers:
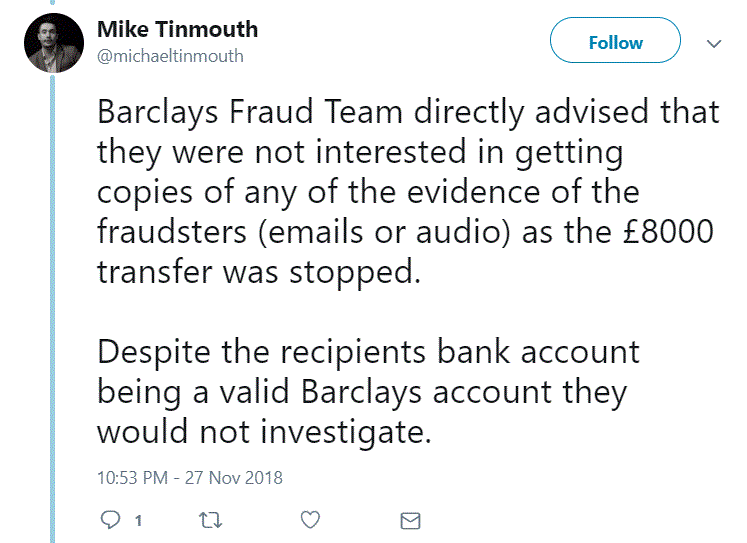
Regardless of what happens in this case, it's a great reminder of how social engineering and a targeted phishing attack can start with something you post on social media. Hackers are getting more sophisticated and more patient; they are willing to study your online moves to trick you.
Tinmouth summed it up for the BBC:
"They targeted me because they are monitoring the big banks' customer support Twitter channels where they can get enough information on name, location, and photo to then be able to track down further information."
It almost worked.
And it is something to consider with any social media posts you make public.



