When it comes to social engineering, phishing rules the pond, if only because of its ability to be many things to many people. One day it’s a shipping invoice from a popular retailer, the next it’s an alert from a top bank, and the next it’s a password reset request from a social media platform. It’s no wonder that technical tools and humans alike have difficulty spotting these numerous and varied attacks.
But as we’ve increasingly seen, phishing success isn’t dependent upon mass appeal. In fact, the more targeted an email, the more likely it is to hit its mark. Cue spear phishing, which is like phishing’s smarter, nastier older brother. Wombat Security, a division of Proofpoint, explored the spear phishing threat in its latest State of the Phish™ Report, which compiles data from a number of different sources, including more than 10,000 responses from surveys sent to the company’s database of InfoSec professionals.
Wombat did share some good news with regard to these targeted social engineering emails: Just 53% of survey respondents said their organizations experienced spear phishing in 2017, a 13% decrease from 2016. Unfortunately, the positive news end there. As is shown in the chart below, it’s clear that affected organizations are dealing with this threat on a regular basis.
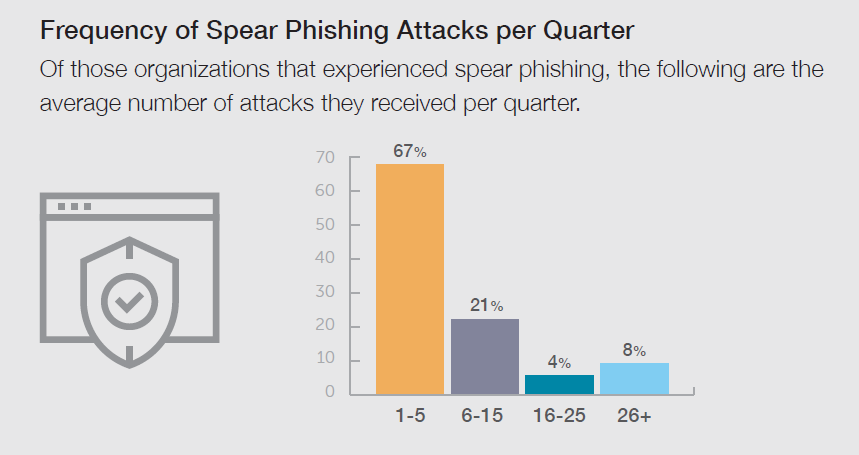
Source: Wombat Security’s quarterly surveys of InfoSec professionals for the 2018 State of the Phish Report
Though most respondents said they deal with between one and five spear phishing attacks per quarter, more than 20% put the number between six and 15, and 8% of InfoSec professionals indicated they face more than 26 of these targeted emails per quarter. The implications of this are very serious, given the sophisticated nature of these social engineering scams and the fact that some forms of these attacks—like business email compromise (BEC)—intend to inflict irreversible monetary damage on organizations.
Wombat’s data reflects the need to actively inform and train employees about the dangers of spear phishing. Organizations that are dealing with this threat could be actively under attack, and the targeted nature of these emails help them more easily evade technical safeguards. Considering these factors, it’s clear that end users are a critical last line of defense. As such, it’s incumbent upon InfoSec teams to raise awareness of the risks associated with spear phishing, and better manage these risks by educating employees to identify the hallmarks of not just "common" phishing attacks, but also those of more personalized and sophisticated messages.
It’s important to note that infrequent, passive training (in the form of PowerPoint presentations and/or auto-run videos) will not prepare end-users to counter frequent, persuasive spear phishing attacks. To change behaviors, you need to deliver an ongoing security awareness training program that is designed to build a culture of security and elevate cybersecurity to a daily pursuit for all end-users.
The full 2018 State of the Phish Report is available on the Wombat Security website. For additional insights from industry experts, register for the July 18 SecureWorld web conference, Cybersecurity Heroes Aren’t Born... They’re Made. You can join live or watch on-demand, and CPE credits are available.





