The State of the Phish is the industry benchmark report around the world's leading cyberattack vector: phishing.
The annual Proofpoint report is based on tens of millions of data points from multiple continents and from across 19 industry verticals. It focuses on working adults and what their cyber knowledge and behaviors are like.
"We want to understand that average person, and the average InfoSec professional and what they are experiencing," says Gretel Egan, Senior Security Awareness Training Strategist at Proofpoint.
Egan revealed the findings during the live SecureWorld webcast, State of the Phish Report 2021, which is now available on-demand. She was co-presenting with Proopoint CTO Kurt Wescoe.
Security awareness finding #1: training programs need improving
The State of the Phish research found that nearly every organization surveyed has some sort of security awareness training. However, it is far from comprehensive. Check out the chart:

"98% of our survey respondents said that their organization is running a security awareness training program. On the surface, that's excellent news. But if we dig a little deeper, we see globally that only 64% of people are doing formal training for their end-users; for security awareness training programs in the United States, that number was 53%. And we have 53% of U.S. organizations saying that they are only using simulated phishing attacks to train their users and teach their users about cybersecurity behaviors. And fewer than 35% of organizations are including business email compromise conversations in their security awareness training program."
Business email compromise (BEC) is a multi-billion dollar problem for organizations, yet most security awareness programs do not train on it.
Security awareness finding #2: what phishing attacks lead to
Proofpoint found that 57% of organizations experienced a successful phishing attack in 2020.
And the new research also reveals what happens after a successful phish: loss of data, credential compromise, ransomware infections, malware, and wire transfer fraud. These things can and do start with a phishing attack; see the chart:

Security awareness finding #3: organizations have a sharing problem
The State of the Phish Report 2021 uncovered some unsettling information about device sharing. This includes trends that work from home and pandemic lockdowns have accelerated.
"The question we asked here is, what do you allow your friends and family to do on your work issued device, like a PC or smartphone?"
The answer could be summed up as "sharing too much," as you see in the chart below: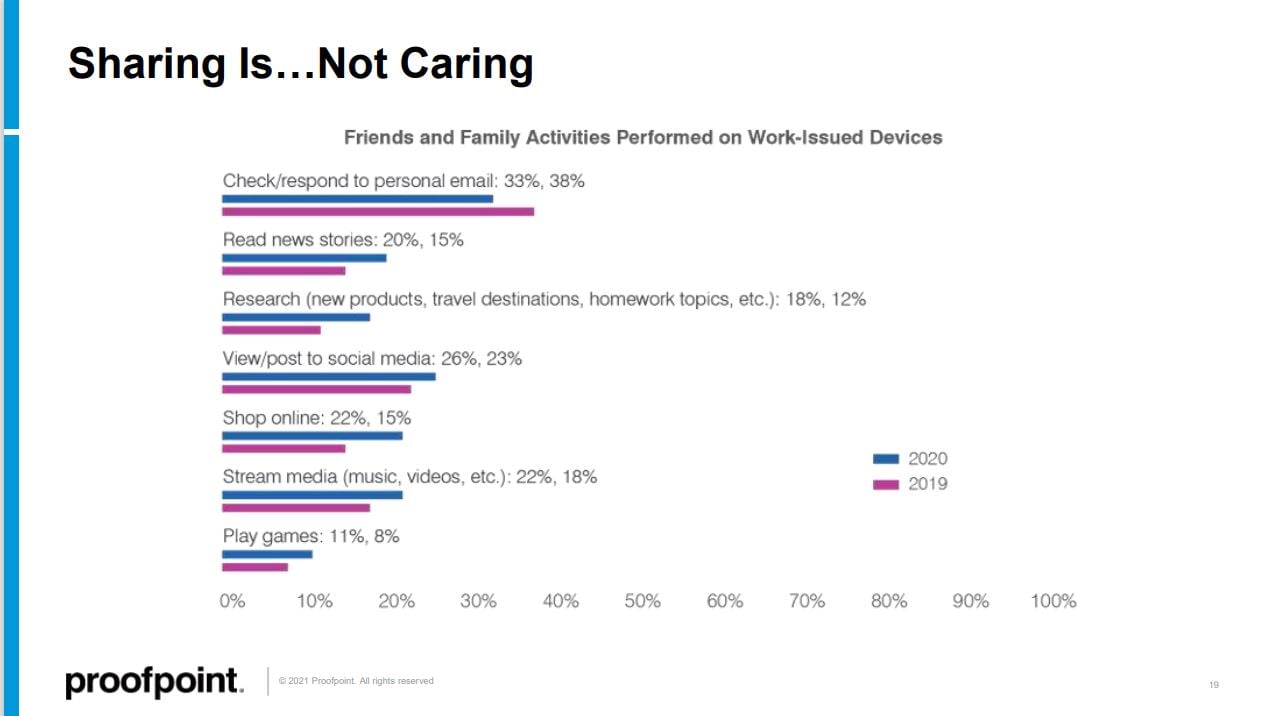
And Egan says these numbers represent another reason why comprehensive security awareness training is so crucial:
"If you are not going beyond the inbox, if you are not talking about behaviors beyond email, then you are courting risk for your organization. It is very important to make sure that we're talking about the significant behaviors that can impact overall security posture."
Security awareness finding #4: burned by ransom demands
Successful phishing attacks are often the first step in a ransomware attack against your organization. When faced with a ransomware incident, 34% of organizations paid the ransom demand, Proofpoint found. That was nearly identical to the previous year.
However, there was a significant change that involves organizations getting burned after they decide to pay. Ransomware operators are increasingly demanding a ransom twice.
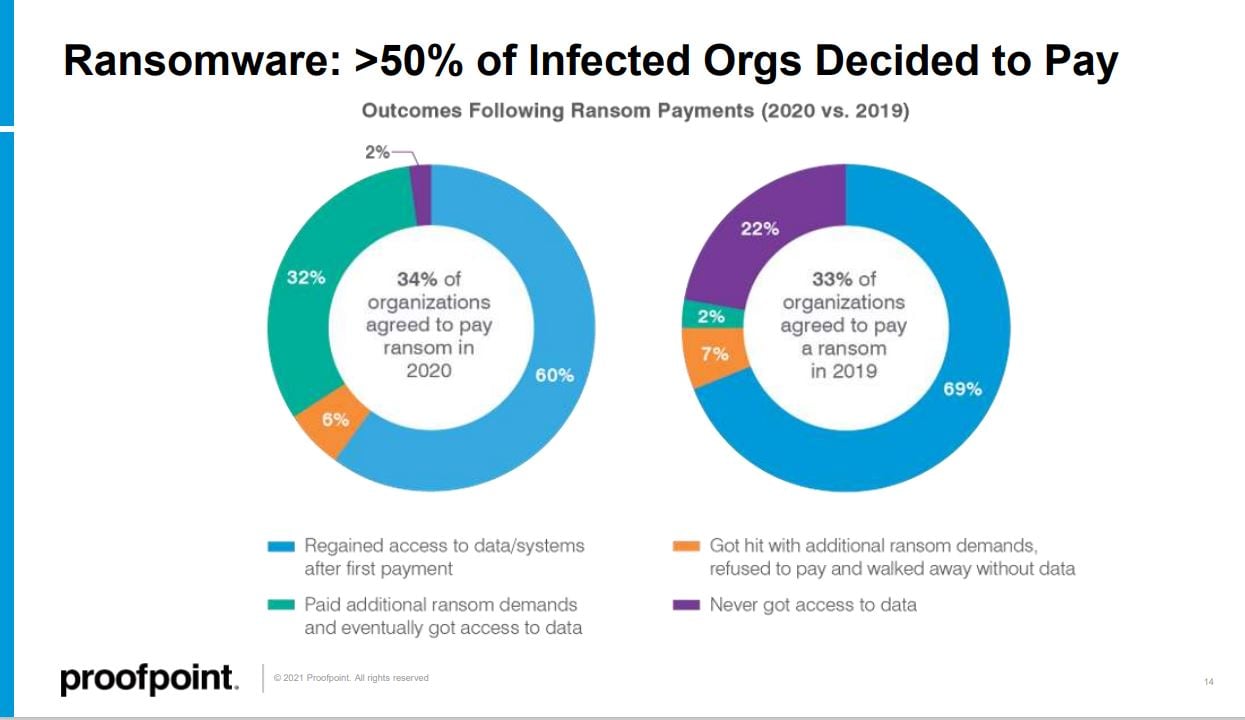
"The big difference is the way things went after meeting the demand. We saw fewer people getting their data back after initial payments. That is concerning in itself.
But if we look at the number of follow-up payments, the number of organizations that decided to go pay a follow-up demand, like 32% of 2020 respondents were willing to pay that compared to just 2% previously. That is a 15,100% increase year over year, so that is really an incredible shift that speaks to the complexity of what a ransomware infection can mean for any particular organization."
Security awareness is a key tool is preventing a ransomware attack in the first place.
This points to the need for a comprehensive security awareness program, one that increases understanding of phishing and the cyber threats beyond the inbox.
And Egan says the language you use is crucial:
"If you have a doctor that walks in to see a patient, and that doctor uses a bunch of medical jargon which the patient is not familiar with, that patient is going to disengage from that conversation.
Even if the advice the doctor gives is relatively simple, easy to follow, and easy to put into practice, the patient is not going to know what to do because they were lost at the beginning of the conversation.
My advice is to really think of your end-users as patients. Have you explained to them what you want from them? Do they understand what you're talking about and the words you're using?"
Those are great questions that every organization should answer.
To download the 2021 report and take a deep dive into key findings, watch the SecureWorld webcast, State of the Phish Report 2021, which is now available on-demand.




