The idea of hacking back against those who hack you has been called a lot of things.
The terms "goofy idea" and "illegal" are some I've personally heard at our cybersecurity conferences.
But for a ransomware victim in Germany, you can add the words "sweet revenge."
And not just revenge for him, but for all of cybersecuritydom.
Cybercrime victim hacks back against hackers
Bleeping Computer caught up with ransomware victim Tobias Frömel, who paid an approximately $700 ransom in Bitcoin and then hacked back into the attacker's command and control server.
He then grabbed and released thousands of keys to decrypt the Mushtik ransomware which has been hitting victims since late September 2019. Here's a screen grab:
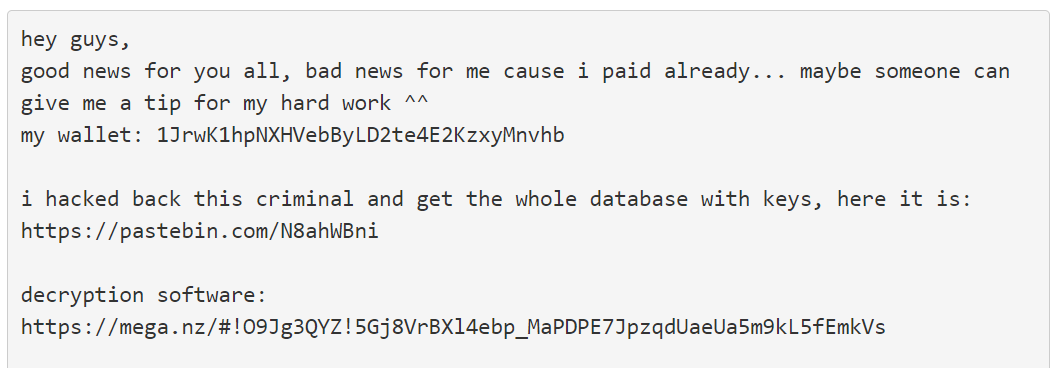
"Victims have since confirmed in our support topic that the decryptor is working and that they were able to decrypt their files," says Bleeping Computer.
You could say he got the keys to this ransomware kingdom.
Hacking back: is active defense a bad idea?
Critics of hacking back call it a bad idea. Perhaps it is the worst one.
A recent article by TechBeacon is titled, "Why the hack-back is still the worst idea in cybersecurity."
It quotes Chris Porter, Chief Strategist for FireEye, as saying most companies lack the expertise to safely conduct an offensive cyber operation.
"Even when the FBI gets a court order and is careful in doing a shutdown, there is still collateral damage. So you can imagine [that], in the heat of an incident, a company responding to an attack could certainly do a lot of collateral damage."
Certainly this is a concern.
At the same time, the article cites Bruce Schneier on the topic. Bad idea or not, the law and reality can be two different things.
"It is, right now, kind of like international bribery. It is illegal and you can't do it, but it is happening," Schneier says.
[RELATED: Listen to our Market (In)security interview with Bruce Schneier in The SecureWorld Sessions, our cybersecurity podcast.]
Congress tries to legalize hacking back
Some in Congress are trying to push through the Active Cyber Defense Certainty Act (ACDC), which can be referred to as the hacking back bill.

The bipartisan legislation would make changes to the Computer Fraud and Abuse Act (CFAA) to allow the use of what it calls, "limited defensive measures that exceed the boundaries of one's network in order to monitor, identify and stop attackers."
What kind of hacking back measures are in the bill?
The ACDC specifies five reasons why organizations would be allowed to go hunting for their attackers. To do the following:
• establish attribution of an attack
• disrupt cyberattacks without damaging others' computers
• retrieve and destroy stolen files
• monitor the behavior of an attacker
• utilize beaconing technology
An explainer by the bill's proponents provides more details in the FAQs:
Most defenders would likely use active-defense techniques to perform "deep reconnaissance" of the hackers who originated the attack. For example, a defender using active-defense techniques could "follow the bread crumbs" back to the source of the attack. They could then attempt to attribute the source, "naming and shaming" the attacker, turn over relevant information to law enforcement, or simply learn the "vector" that the attacker took to execute the original malicious attack and avoid it.
What about collateral damage from hacking back / active defense?
The bill's authors also specifically address the topic of unintended consequences as a result of hacking back scenarios.
ACDC has a very high standard for cyber defenders. If a defender behaves improperly or recklessly, they will still bear the full penalty of existing law. ACDC does not change the existing penalties for "unauthorized access;" it merely allows a legal defense for such access in cases where self-defense is clearly justified. The bill makes clear that if a person is inadvertently impacted by active-cyber defense, their right to sue for civil damages or injunctive relief is preserved. Defenders would be forced to take a very deliberate, step-by-step process of using active-cyber defense or they would still run the risk of civil and criminal penalties.
So is hacking back the worst idea in cybersecurity? Or a concept that needs to be legalized? Let us know your opinion in the comments below.
While the debate goes on, we know this much: Some victims of Mushtik ransomware are very glad a guy in Germany decided to hack back.




