Shipping giant Toll Group proves that lightning can strike twice.
The Australian transportation and logistics company is dealing with its second ransomware attack of 2020—and it is only May.
Toll has posted updates to the company website and vows, "Toll has no intention of engaging with any ransom demands...."
What do we know about this ransomware attack on the company?
The shipping company says it is responding to a strain of ransomware known as Nefilim in the current attack.
Although Toll implemented its Business Continuity Plan right away, the company says the attack disrupted email, forced disabling of core IT systems, and created delays and disruptions for some customers.
The timing is extra tricky as the company transports critical supplies for COVID-19 response in some shipments.
And in addition to encrypting data, this ransomware attacker exfiltrated data, as well:
"Our ongoing investigations have established that the attacker has accessed at least one specific corporate server. This server contains information relating to some past and present Toll employees, and details of commercial agreements with some of our current and former enterprise customers. The server in question is not designed as a repository for customer operational data.
At this stage, we have determined that the attacker has downloaded some data stored on the corporate server, and we are in the process of identifying the specific nature of that information.
The attacker is known to publish stolen data to the 'dark web'. This means that, to our knowledge, information is not readily accessible through conventional online platforms. Toll is not aware at this time of any information from the server in question having been published."
This type of attack is referred to by some as "nuclear" ransomware, which describes an evolution of these types of attacks.
What is nuclear ransomware?
Nuclear ransomware refers to what the particular strain of ransomware can do. If it simply encrypts data on your corporate network, that's the former worst case scenario for ransomware.
Now, the bigger fear is getting hit by ransomware that is "nuclear."
Chief Information Security Officer Sam Masiello of the Gates Corporation explains:
"No longer are some of these attacks just encrypting your data on your network, and you're paying the ransom to get your data back. In some cases, the bad guys already have your information. In some cases, what's happening is your data is being encrypted, while at the same time the data is being exfiltrated out the back door."
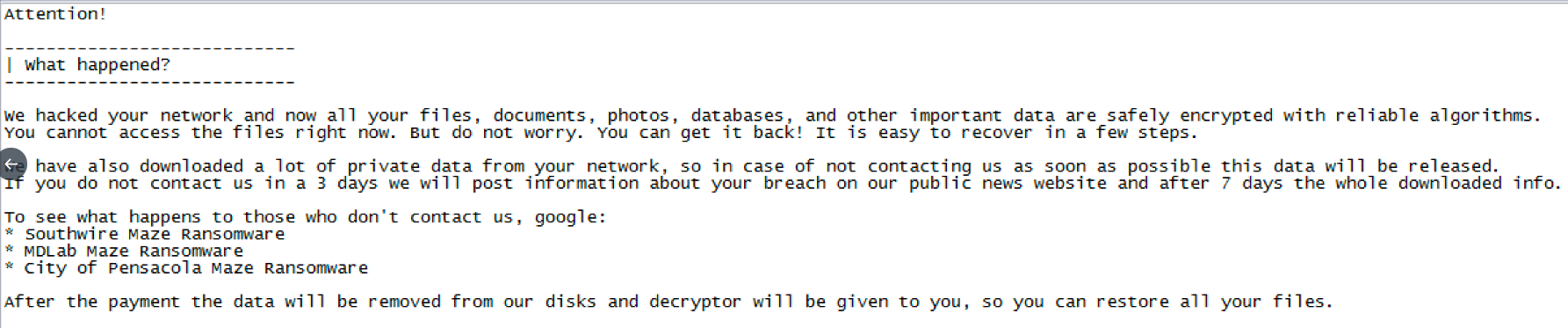
And what do hackers do with that stolen data? They threaten to publish it unless you pay the ransom.
And in the case of the Maze ransomware gang, their ransom notes suggest you Google what happened to previous victims who did not pay. Click to expand:
Several strains of ransomware have gone nuclear: Nefilim ransomware, which hackers used in the attack against Toll shipping; REvil ransomware, which cybercriminals used to attack the law firm to the stars and published part of a Madonna contract as a warning; and Maze ransomware, which published one company's proprietary information, leading to a John Doe lawsuit against the unknown hacking gang involved.
There are other strains of nuclear ransomware and new strains appearing because the business model is so successful.
CISO Sam Masiello sums it up like this:
"They've already stolen your data, and potentially they are going to sell that data again on the white market. So one way or another, they will probably end up getting paid for the fact they've victimized your organization. It's just a matter of whether they'll also get paid by you to get the decryption key to get your data back."
Isn't that what most organizations are looking for? A product that will make money no matter what?
Now we'll wait and see how the ransomware group behind this attack on Toll shipping cashes out with the data it stole.