How do you secure a modern web application in the AWS cloud?
We'd like to shed some light on this topic.
Especially because we hear from security and IT teams on a regular basis who are moving to the cloud and trying to understand how what they do on-prem translates to web app sec in the cloud.
AWS cloud web app sec: simple threat modeling
SANS Analyst Shaun McCullough kicked off a recent web conference on this topic titled, "How to Secure a Modern Web Application in AWS."
First of all, you need to understand the biggest risks to your application in the cloud and your workflows. This starts with threat modeling. But you must keep that process simple.
"I don't want you spending a weekend in the conference room with a bunch of pizza and your whole team, and then at the end you have a large binder or the most complicated Excel spreadsheet you've ever seen. Now it's not actionable; it's really hard to know what to do."
He says there are numerous ways to approach threat modeling frameworks and the process itself. They are detailed in the whitepaper, "Securing a Modern Web Application in AWS."
However, McCullough likes using the DREAD model, because it's relatively simple and you can build on it. DREAD stands for Damage Potential, Reproducibility, Exploitability, Affected Users, and Discoverability.
And when considering how to address a risk, he says you'll have one of these four outcomes:
1) Mitigate risk: Reduce risk to an acceptable level
2) Eliminate risk: Remove risk, likely through re-architecting
3) Transfer risk: Move login to cloud service provider
4) Accept risk: Risks not addressed are accepted
AWS cloud use case for app sec
Next, McCullough moved onto a web app sec use case. In his example, you have a web application with a database. It's an app with a comments section, which is open to the internet with a login.
"If you have a pentest organization or an internal red team, you can turn to them for discovering the possible range of threats," he says.
Another idea is to look at open resources.
"The OWASP Top 10 gives a very detailed explanation of what this organization sees as the top 10 most likely threats, how likely they are to happen, how successful those attacks are, and how they are carried out."
So for the case study, he picked the Cross-Site Scripting (XSS) threat, where an attacker injects text in comments with JavaScript. In this attack, when someone else goes into the page and reads those comments, the JavaScript steals their cookies and sends them to the attacker, enabling the attacker to log in as if they are someone else.
Examples of what could be done easily in the cloud include implementing a Web Application Firewall (WAF) or choosing a third-party vendor from the AWS Marketplace that handles this type of threat.
Each AWS Marketplace vendor is approved as a solution that easily integrates into the AWS cloud.
Specific AWS tools for web application cybersecurity
David Aiken, Solutions Architect for AWS Marketplace, then took the reigns of the web conference and revealed the AWS services which help enable web application security. He also mapped these services back to the NIST Cybersecurity Framework, as you see here:
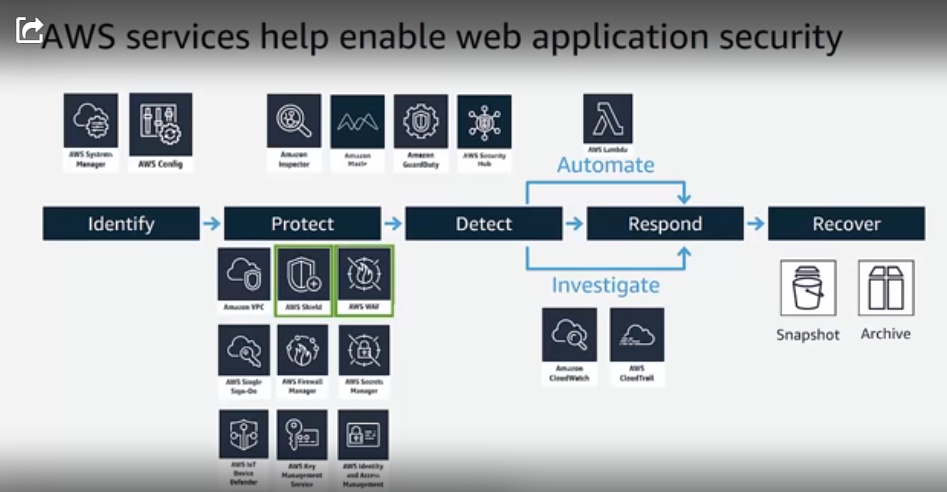
"For example, AWS Config can give you information about whether your users and developers are deploying approved infrastructure. And whether they're meeting the security developments you've set up there," Aiken says.
"Also, AWS Inspector can be used throughout the Dev process to do vulnerability scanning. A lot of these security tools are behind an API in AWS, so you can automate much of this."
That includes creating custom rules that block common attack patterns and deploying new rules within minutes to quickly respond to changing traffic patterns. Here's how web app sec looks behind the AWS WAF (Web Application Firewall):
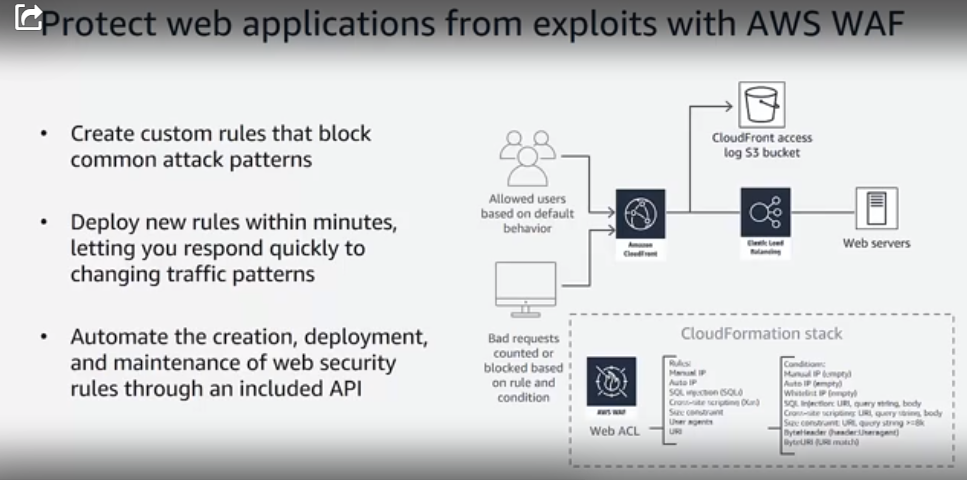
And here's a productivity saver: you can define application-specific rules, and they ship to the cloud within your code.
AWS web app sec integration example using Fortinet
And when it comes to defining the rules, you can simplify and speed up the process by using an AWS Marketplace integrated partner.
In this web conference, Aiken used Fortinet as an example.
When you layer Fortinet on the AWS WAF, you still work within the AWS console, but you can now pick a rule-set that accounts for emerging threats.
"If you go adopt those rules, you don't have to think too much about whether you have full coverage or how do you define a rule to stop a cross-site scripting attack. Fortinet and the security experts there have already figured those things out and packaged these into bundles."
And he explained how this process just simplified what you and your security team have to do.
"So if you're using AWS WAF, there's no infrastructure for you to manage. And if you use an AWS partner for rules, there are also no rules for you to manage. And you're going to get continuous updates from Fortinet on a regular basis."
Resources and links: web app sec in the AWS cloud
What we've covered here just scratches the surface on this topic.
So we have two kinds of resources that can help you get started securing your infrastructure in the cloud—or help you verify you are doing things correctly. Web conferences and whitepapers are below.
Web Conference: How to Secure a Modern Web Application in AWS
Whitepaper: Threat Modeling and Securing a Modern Web App in AWS
Web Conference: Jump Start Guide to Application Security in AWS
Whitepaper: How to Jump Start App Sec in the AWS Cloud
Rapid cloud deployment continues, and it's helpful to have tools like these to guide how app sec can be enabled in AWS.
[RELATED: How to Deploy Endpoint Protection in AWS]




