Australian Prime Minister Scott Morrison had a stark message for the country on Monday morning, and it generated so much web traffic that it led to a false DDoS alert.
"For many young and old, 2020 will be the toughest year of our lives."
He was talking about how limiting the spread of COVID-19 will do major damage to the economy and cost many people their jobs.
"As Australia works to flatten the curve and slow this virus, we also face an immense economic challenge… this is the biggest economic shock our nation has faced in generations," Morrison said.
His message came through loud and clear.
It sent so many Australians to the website, where residents sign up for benefits and job seekers apply for allowances, that the legitimate traffic set off a DDoS alert.
A distributed denial-of-service (DDoS) attack is when something like a botnet of compromised devices flood a target with traffic, denying service to legitimate users.
In this case, legitimate users are the ones who caused the false alarm and crashed the site for a time.
CNN has the numbers:
"Government Services Minister Stuart Roberts said a distributed denial of service (DDOS) alarm was triggered on the MyGov site when 95,000 users logged on at the same time just after 9 a.m., Monday morning. The system was built for 55,000 concurrent users, he said, adding that the government is examining ways to expand the system’s capacity."
And while it turns out this was not a DDoS attack during the coronavirus pandemic, Australian authorities are seeing others COVID-19 cyberattacks.
Coronavirus cyberattacks: phishing and smishing
The Australian Cyber Security Centre is doing an excellent job of sharing the latest coronavirus cyberattacks on Twitter.
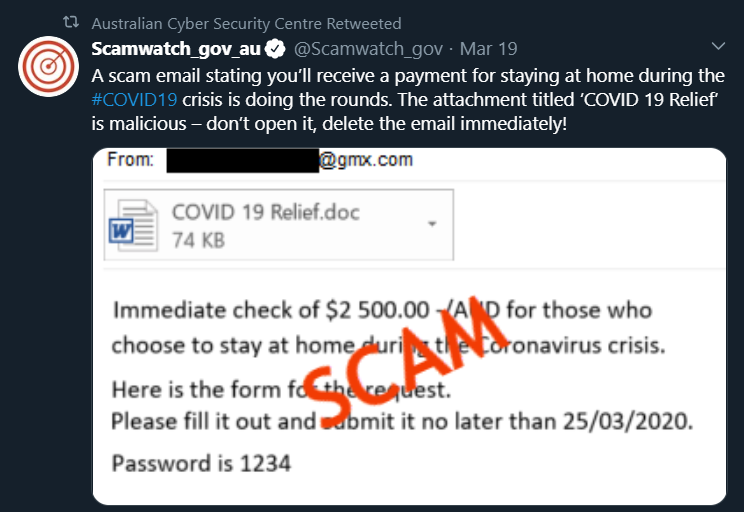
It has discovered phishing attacks promising an "immediate $2,500" from the Australian government which "is malicious—don't open it, delete the email immediately!"
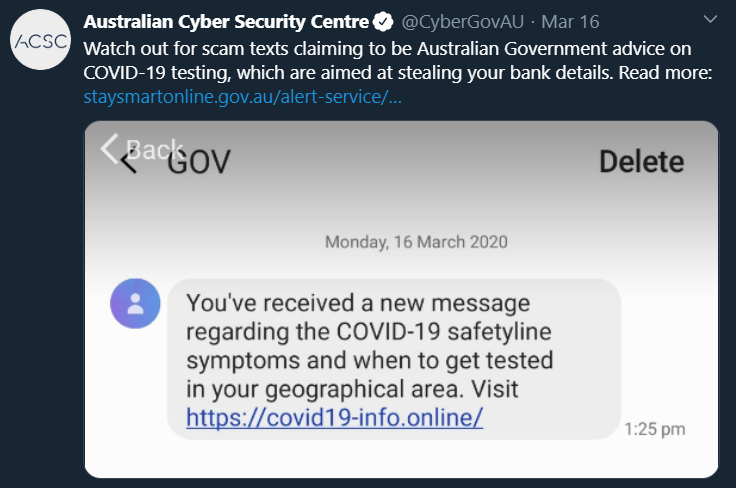
And it is also tracking smishing attacks, which are malicious text messages to mobile devices. This one plays off the emotions around virus testing:
Speaking of emotions, you might want to share this article with employees or friends: 5 Emotions Used in Social Engineering Attacks [with Examples].
Hackers change their words in phishing and smishing attacks, based on what's happening in the world.
However, they use the same old emotions to trick us because social engineering works unless we stop to think.
[RELATED: Coronavirus Cybercrimes: Are These the Lowest?]
[RESOURCE: SecureWorld cybersecurity web conferences]




