Here's an insider threat case for you, with a twist.
Shutting off an employee's email and login after their final day used to be enough.
Now, however, there is something else for IT, cybersecurity, and HR to consider, even among their own teams.
Employee creates back door, hacks former employer
Customers of WPML, a browser plugin that allows WordPress websites to be easily translated, received an urgent message over the weekend, both by email and by a post on the company's website.
The message claimed to be from a customer, which some customers believed. However, other WPML users knew right away the organization's website and its email database must have been part of a hack:
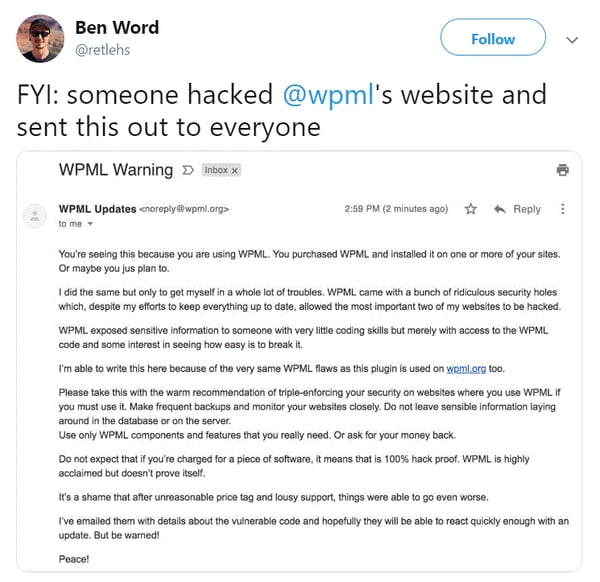 The letter, sent by the person behind the cyber attack, reads in part:
The letter, sent by the person behind the cyber attack, reads in part:
"WPML came with a bunch of ridiculous security holes which, despite my efforts to keep everything up to date, allowed the most important of my two websites to be hacked.... It's a shame that after unreasonable price tag and lousy support, things were able to go even worse."
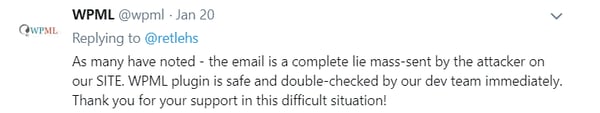
And while some customers tweeted that the customer must have just gotten fed up with notifying the company about security holes and not seeing anything change, the company responded in no uncertain terms:
"The email is a complete lie mass-sent by the attacker on our site. WPML plugin is safe and double-checked by our dev team immediately."
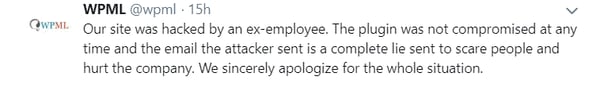
And a few hours later, the company revealed that the hacker was indeed another example of an insider threat:
"Our site was hacked by an ex-employee. The plugin was not compromised at any time and the email the attacker sent is a complete lie to scare people and hurt the company."
 How did a former employee hack the company website?
How did a former employee hack the company website?
So how did a former employee hack the organization's website? By leaving a secret way in—a backdoor—while he worked for the company.
We have learned more now in a company post on the WPML hack:
"Our data shows that the hacker used inside information (an old SSH password) and a hole that he left for himself while he was our employee.
This hack was not done via an exploit in WordPress, WPML or another plugin, but using this inside information. In any case, the damage is great and it’s done already."
That last line sounds eerily similar to something Dr. Larry Ponemon mentioned at SecureWorld a couple of years ago.
"When companies had an insider threat, in general, they were much more costly than external incidents. This was largely because the insider that is smart has the skills to hide the crime, for months, for years, sometimes forever."
In this case, the hiding is over, and as the company says, the damage is done.
[RELATED: How Raytheon Discovered a Systems Engineer Was an Insider Threat]




